The Cybersecurity and Infrastructure Security Agency is ordering federal agencies to harden their network edge and remote management devices, citing “recent threat campaigns” that have exploited improperly configured network devices.
The June 13 order, a Binding Operational Directive that all civilian executive branch agencies must follow, covers a range of actions across scores of devices used throughout government, particularly those that connect to the internet.
The order covers network devices like routers, switches, firewalls, VPN concentrators, proxies, load balancers and out of band server management interfaces. It also covers remote management tools that use protocols like Hypertext Transfer Protocol (HTTP), Hypertext Transfer Protocol Secure (HTTPS), File Transfer Protocol (FTP), Simple Network Management Protocol (SNMP), Teletype Network (Telnet), Trivial File Transfer Protocol (TFTP), Remote Desktop Protocol (RDP), Remote Login (rlogin), Remote Shell (RSH), Secure Shell (SSH), Server Message Block (SMB), Virtual Network Computing (VNC), and X11 (X Window System).
"As agencies and organizations have gained better visibility of their networks and improved endpoint detection and response, threat actors have adjusted tactics to evade these protections by targeting network devices supporting the underlying network infrastructure," the order states.
“Threat actors have used certain classes of network devices to gain unrestricted access to organizational networks leading to full scale compromises. Inadequate security, misconfigurations, and out of date software make these devices more vulnerable to exploitation. The risk is further compounded if device management interfaces are connected directly to, and accessible from, the public-facing internet.”
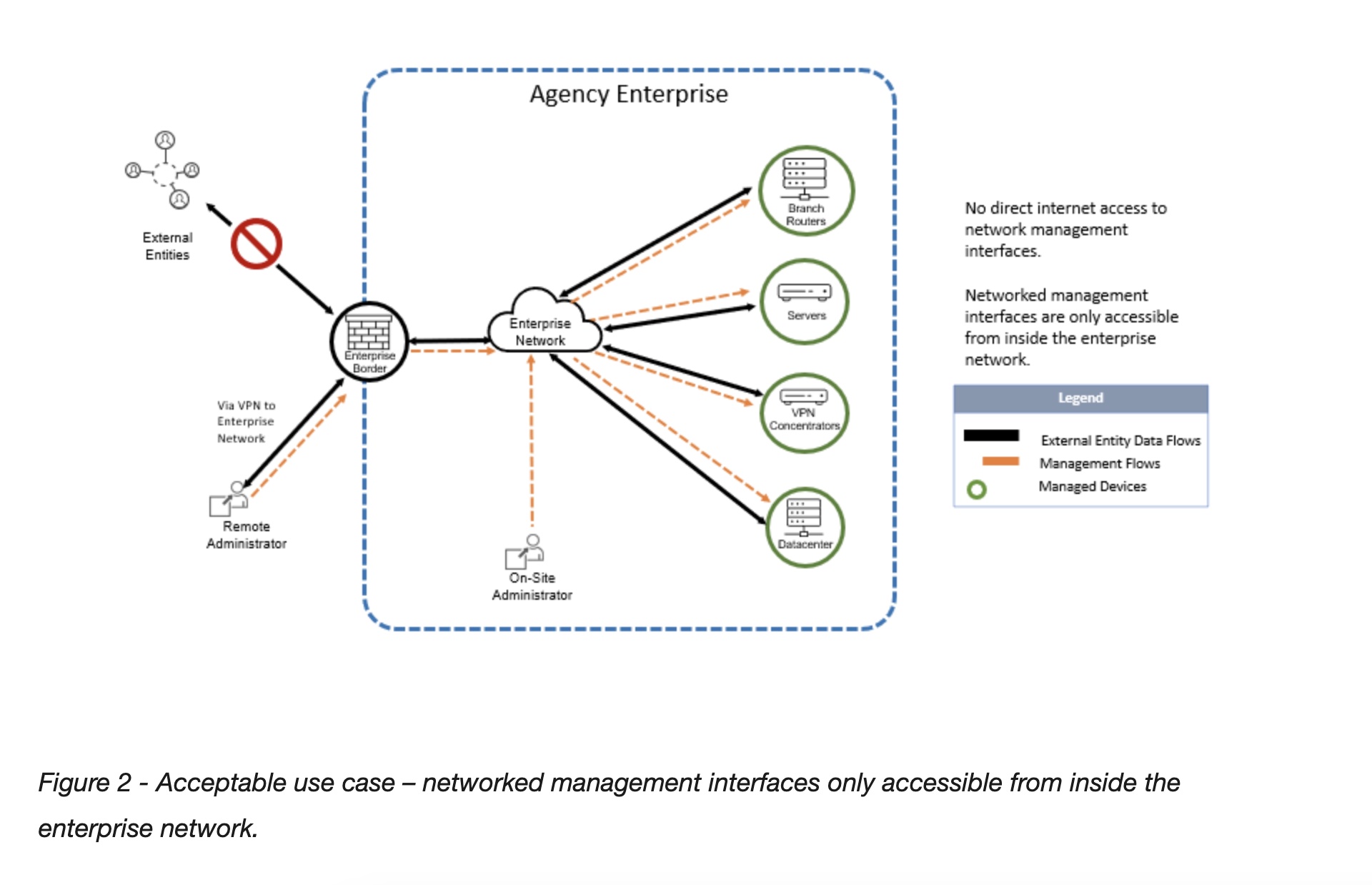
CISA will begin scanning agency networks for vulnerable devices. After being notified, agencies will have two weeks to disconnect their device from the internet or deploy enhanced access controls. Further, they must implement technical controls for all newly added or discovered devices and their management interfaces that restrict access to an internal or isolated network.
Wherever feasible, CISA asks that agencies align their protections with the federal government’s broader push for Zero Trust security architecture. To that end, they recommend agencies consult a number of existing federal guidelines around implementing Zero Trust, including OMB-M-22-09, NIST 800-207, the TIC 3.0 Capability Catalog and CISA’s Zero Trust Maturity Model.
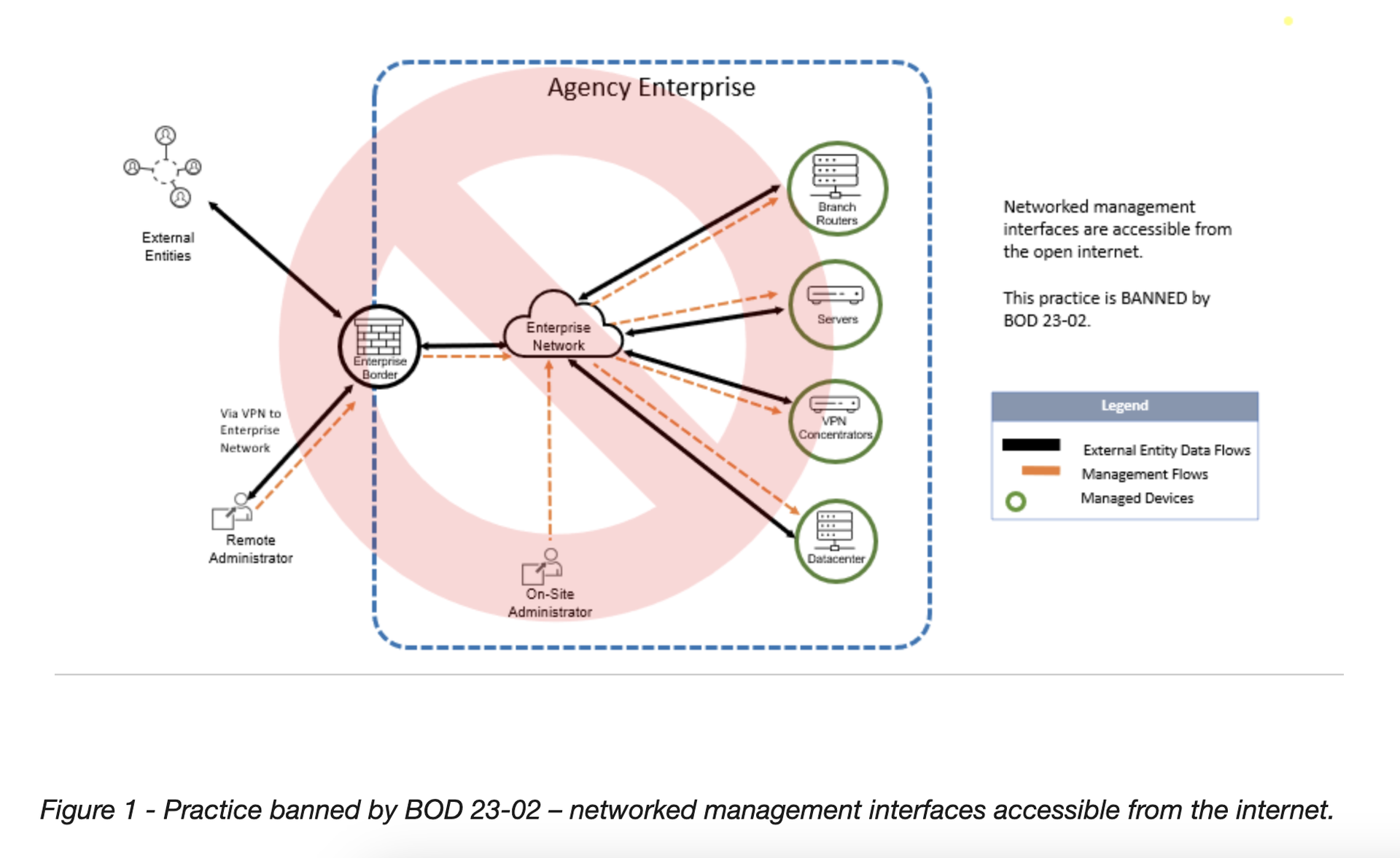
An implementation page for the order further clarifies the kind of devices and actions the order is targeting. One example they give is a router that manages traffic inside the network, has a web management interface and is accessible via HTTPs and the internet.
“In the context of this Directive, a ‘networked management interface’ is a device interface dedicated to configuration and management operations (meant exclusively for authorized users to perform administrative activities on a device, a group of devices, or the network itself, and is accessible from a network over a network protocol),” the guide states. “Other terms used to describe these types of interfaces include management interface, administrative (admin) interface, and ‘back end’ interface.”
The directive applies to federal contractors as well as civilian executive branch agencies. It explicitly excludes Application Programming Interfaces (API), management portals or web applications that manage offerings from third-party cloud providers. However, the implementation guidance states that certain infrastructure-as-a-service and platform-as-a-service devices might qualify, while most software-as-a-service applications would not.
CISA plans to offer agencies an interface to report vulnerable devices as well as a standardized remediation templates, and coordinate with CIOs, CISOs and other agency leaders to map out and address covered IT. The agency also plans to update and revise the order in two years to account for changes in the technology and threat landscapes.
CISA does not provide any further details about existing campaigns targeting the government, but Mandiant and other private threat intelligence agencies have noted a broader trend by Russian and Chinese hackers towards exploiting edge network devices to avoid detection from EDR and other scanning tools on endpoints.




