A new phishing-as-a-service called “Greatness” has been offering affiliates an attachment and link builder to make convincing Microsoft 365 decoy and login pages, making it well-suited to target business users.
Researchers at Cisco Talos noted in a May 10 blog that several phishing campaigns using the service have been observed since at least mid-2022, with spikes in activity in December and March. The campaigns have been targeting mostly manufacturing, healthcare and technology companies in the U.S., UK, South Africa and Canada, with over 50% of all targets based in the U.S. alone.
Researcher Tiago Pereira wrote that “affiliates must deploy and configure a provided phishing kit with an API key that allows even unskilled threat actors to easily take advantage of the service’s more advanced features. The phishing kit and API work as a proxy to the Microsoft 365 authentication system, performing a ‘man-in-the-middle’ attack and stealing the victim’s authentication credentials or cookies.”
Pererira explained that the phishing-as-a-service contains a phishing kit (which contains the admin panel), the service API and a Telegram bot or email address.
The attack begins when victims receive a malicious email that typically has an HTML file attachment, Pererira continued. Opening the attachment runs an obfuscated JavaScript code in the web browser that contains a blurred image displaying a spinning wheel to pretend it’s loading a document.
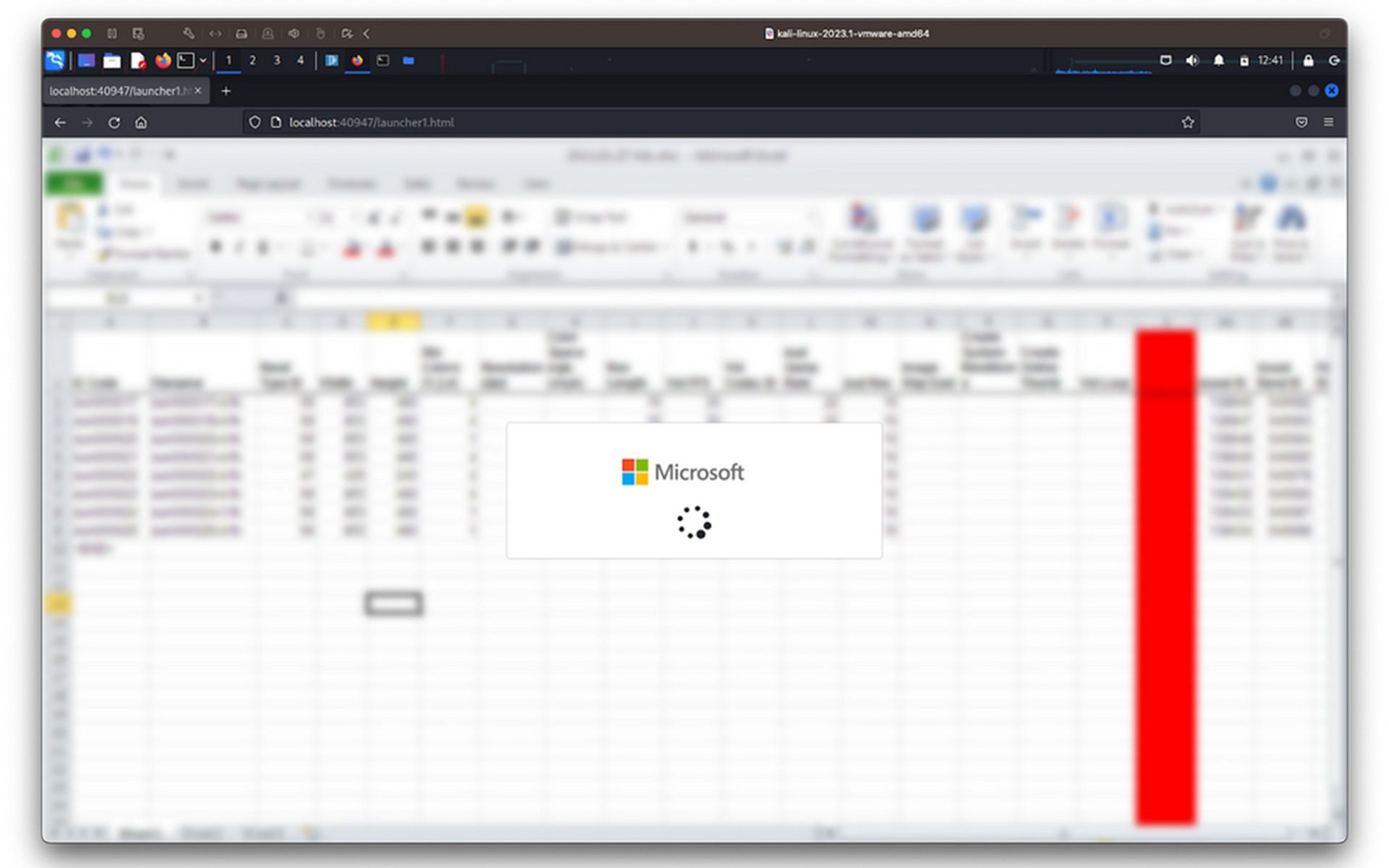
The victim is then redirected to a Microsoft 365 login page that's often pre-filled with their email address and a custom background and logo used by their company. Once the victim types in their password, the phishing service connects to Microsoft 365 and impersonates the victim to attempt a log in. The phishing-as-a-service will even prompt the victim to authenticate a multi-factor authentication request by the real Microsoft 365 page, such as SMS code or push notification.
The PaaS kit stores the credentials locally so they can be accessed via the administrative panel and sends them to the affiliate’s Telegram channel, if configured to do so.
As Pererira wrote: “Working together, the phishing kit and the API perform a ‘man-in-the-middle’ attack, requesting information from the victim that the API will then submit to the legitimate login page in real time.” Since authentication sessions time out after a while, the attacker is informed as soon as possible by the Telegram bot that the victim’s authenticated session cookies have been obtained.




