Readers of the North Korea-focused news website called NK News are being targeted by advanced persistent threat group Kimsuky. The campaign targets Google and subscription credentials of website visitors, according to a collaborative investigative report by SentinelLabs and NK News.
Based in Delaware, NK News, is an independent news, analysis and research website owned by Korea Risk Group that publishes news and analysis critical of North Korea. Earlier this month, the US Department of Defense issued a warning (PDF) that North Korean-linked adversaries are targeting think tanks and media outlets in a new campaign.
On Tuesday the NK News outlet published a detailed report on how the site and its users were targeted in tandem with SentinelLabs, who also published a separate report on the incident.
Going down the Kimsuky rabbit hole
According to the report, the campaign involved a highly targeted and persistent spear-phishing campaign that combined spoofed emails, fake websites and reconnaissance malware. The objective was to gather intelligence and steal account credentials from a highly targeted group of non-governmental experts.
“Looks like [NK Pro] got under someone’s skin,” according to the NK News report quoting Dennis Desmond, a former U.S. counterintelligence officer.
NK News detailed the assault and revealed adversaries used a spoofed email address membership[@]nknews[.]pro to send known subscribers a message outlining “updates for ip security”. The spoofed email was falsely identified from an actual NK News account manager.
“A link included in the email directs recipients to a malicious copy of the product login page that appears to send any entered credentials to the attackers,” according to the SentinelLabs report.
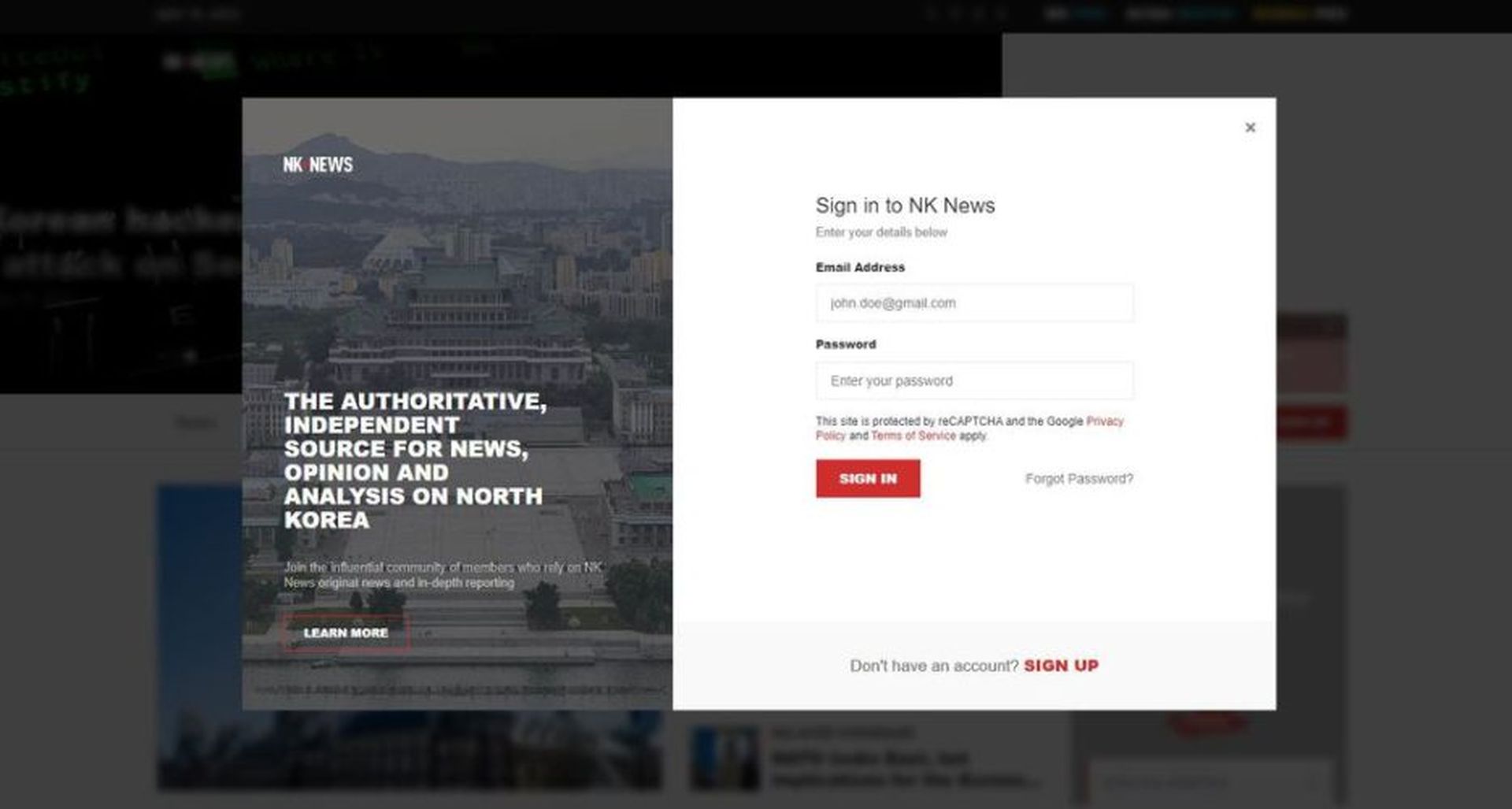
“The fake login site, hosted at https[://]www.nknews[.]pro/ip/register/, features a login form with the standard web elements, such as Sign In, Sign Up, and Forgot Password? buttons. When clicked, the Sign In button executes the loginAct JavaScript function, whereas the rest of the buttons do not conduct any activities,” wrote Aleksandar Milenkoski, senior threat researcher at SentinelLabs.
According to an analysis of the spoofed login page, if users interact with the JavaScript code it captures any credentials entered by issuing an “HTTP POST request to https[://]www.nknews[.]pro/ip/register/login[.]php and then redirects the user to the legitimate NK News site.”
Nuke-based bait and hack
In a separate phishing ploy to target NK News readers, Kimsuky threat actors created the domain nknews[.]pro in an attempt to spoof the legitimate nknews.com domain. Targets were sent a HTML-formatted phishing email asking the recipient to follow an embedded link directing them to nknews[.]pro, to review a draft article analyzing the nuclear threat posed by North Korea.
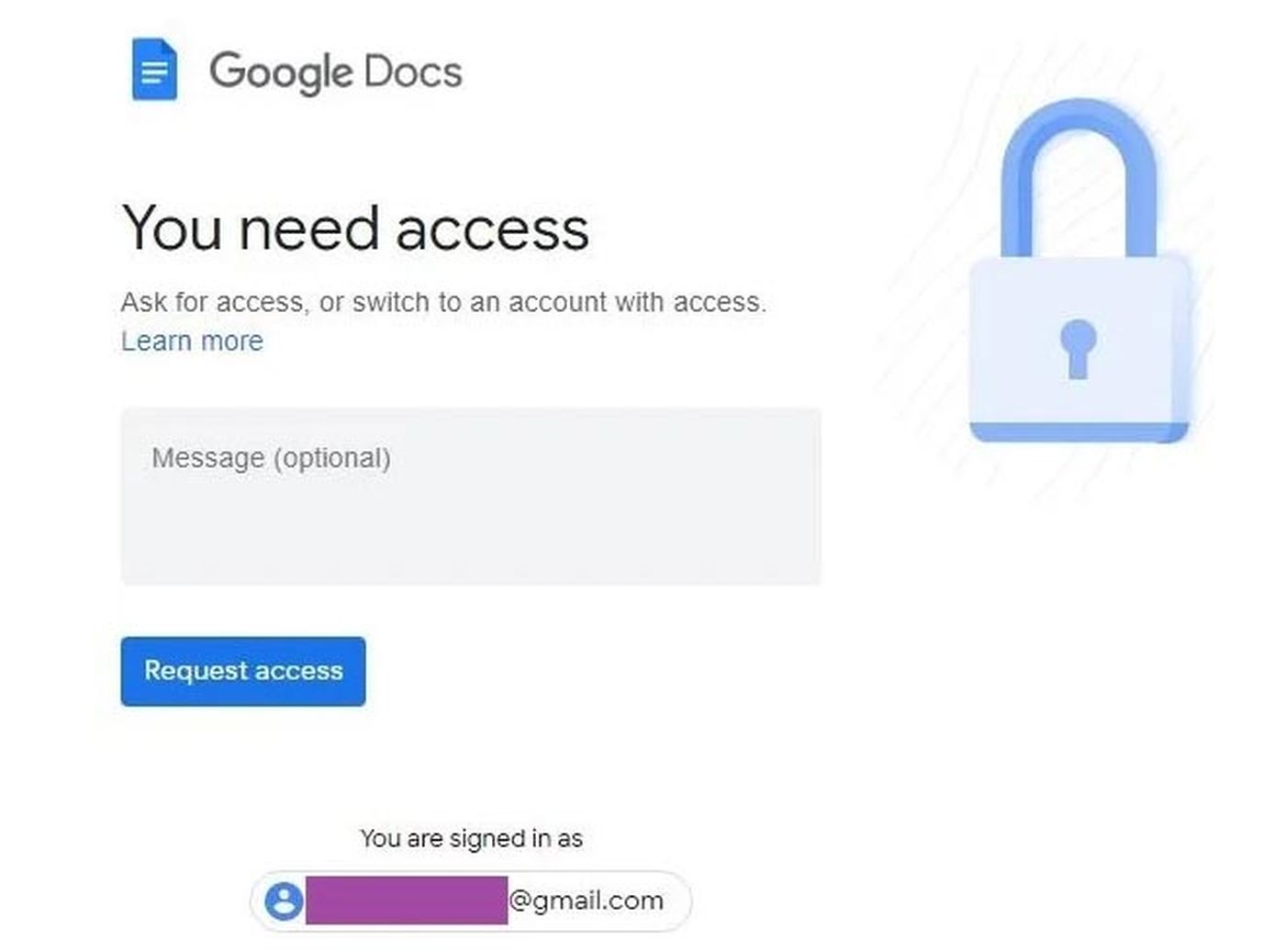
“If the target engages in the conversation, Kimsuky uses the opportunity to deliver a spoofed URL to a Google document, which redirects to a malicious website specifically crafted to capture Google credentials. Kimsuky may also deliver a weaponized Office document that executes the ReconShark reconnaissance malware,” Milenkoski wrote.
Once a level of trust was established, targets were sent a “compressed file named ‘NK_nuclear_threat.zip,’ which contained a Microsoft Word document infected with the known ReconShark malware,” NK News reported.
ReconShark is a tool used by threat actors as a reconnaissance tool to collect technical details of a target’s computer to aid in future attacks. According to SentinelLabs, command-and-control sites delivering the ReconShark tool (staradvertiser[.]store) have known Kimsuky controlled domains.
“This Kimsuky activity indicates the group’s growing efforts to establish early communication and foster trust with their targets prior to initiating malicious operations, including the delivery of malware. Their approach highlights the group’s commitment to creating a sense of rapport with the individuals they target, potentially increasing the success rate of their subsequent malicious activities,” according to SentinelLabs.
Ongoing Kimsuky efforts
Kimsuky — also known as APT43, Thallium and Velvet Chollima — Is well known for its focus on social engineering, and is linked to North Korea’s main military intelligence organization, the General Reconnaissance Bureau.
According to an NSA advisory issued last week, the APT group’s primary mission is “provide stolen data and valuable geopolitical insight to the North Korean regime”.
The NSA advisory, co-authored with several other U.S. and South Korean government agencies, was written to alert potential targets of Kimsuky’s spear-phishing efforts to the risks the group posed and red flags to look out for.
“North Korea relies heavily on intelligence gained by compromising policy analysts,” the advisory said.
“Further, successful compromises enable Kimsuky actors to craft more credible and effective spear-phishing emails that can be leveraged against more sensitive, higher-value targets,” the NSA warned.