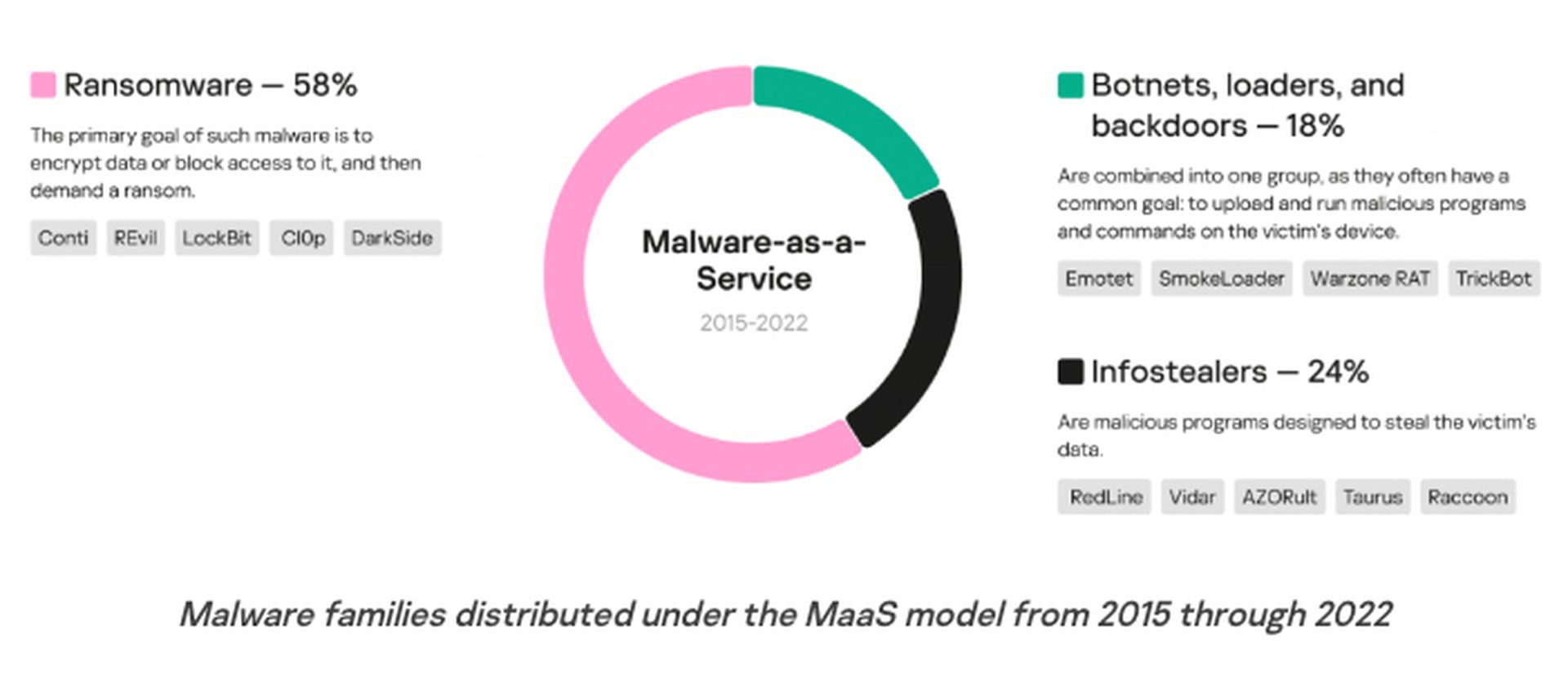
Ransomware accounted for 58% of all malware families distributed as malware-as-a-service in a new study of the cybercrime business model over a seven-year period.
Cybersecurity firm Kaspersky’s Digital Footprint Intelligence team researched 97 malware families distributed on the dark web and other resources between 2015 and 2022 to identify the most popular types of “as-a-service" malware offered by criminals.
The company described malware-as-a-service (MaaS) as an “illicit model of business involving the leasing of software to carry out cyberattacks. Clients are typically offered personal accounts through which they can control the attack, which “lowers the initial threshold of expertise needed by would-be cybercriminals,” Kaspersky explained.
Broken down into five categories, ransomware led the pack as the malware most detected at nearly 60%, followed by infostealers (24%), and the remaining 18% divided between botnets, loaders and backdoors.
Infostealers were mentioned the most on dark web communities, however, ahead of ransomware and other attack methods.
Interestingly, Kaspersky researchers wrote that there is “a direct correlation between the number of mentions of malware families on the dark and deep web and various events related to cybercrime, such as resonant cyberattacks.”
Looking at five “infamous” strains of ransomware as an example (GrandCrab, Nemty, REvil, Conti, and LockBit), the Kaspersky team was able to piece together a timeline of ransomware mentions with events such as arrests of ransomware gang members or the termination of group observations, as detailed in the graphic below:

“As we can see in the graph above, the termination of group operations, arrests of members, and deletion of posts on hidden forums about the spread of ransomware fail to stop cybercriminal activity completely,” researchers wrote. “A new group replaces the one that has ceased to operate, and it often welcomes members of the defunct one.”
Cybercriminals subscribe for ransomware-as-a-service (RaaS) for free, paying a cut of the ransom proceeds after a successful attack. According to Kaspersky, payment is determined by a percentage of the ransom paid by the victim, typically in the 10% to 40% range.
Infostealer services are offered through a paid subscription model, with prices between $100 and $300 a month for software designed to steal data such as credentials, passwords, banking accounts, browser history, crypto wallets data, and more.





