Hundreds of congressional leaders and staff had their data stolen by threat actors through DC Health Link, the health insurance marketplace for Washington. An email notifying House members and staff of the breach was first revealed by the Daily Caller.
Calling it a “significant data breach,” the Capitol Police and DC Health Link notified House of Representatives Chief Administrative Officer Catherine Szpindor late March 8 that the personally identifiable information of thousands of health insurance enrollees may have been exposed.
The scope and source of the hack is currently unknown. The FBI has confirmed that the account information and PII of “hundreds of members and staff” were included in the stolen information.
However, the data appears to not only have been leaked online: the dark web posting on IntelBroker, is listed as “SOLD.” IntelBroker, or Endurance, emerged in October 2022 and uses a “small wiper malware written in C# using the .NET framework.”
A screengrab posted on Twitter shows IntelBroker first compromised the DC Health Link Health Benefit Exchange Authority in the early hours of Monday, March 6. The actor claims “to be in possession” of the data tied to 170,000 individuals.
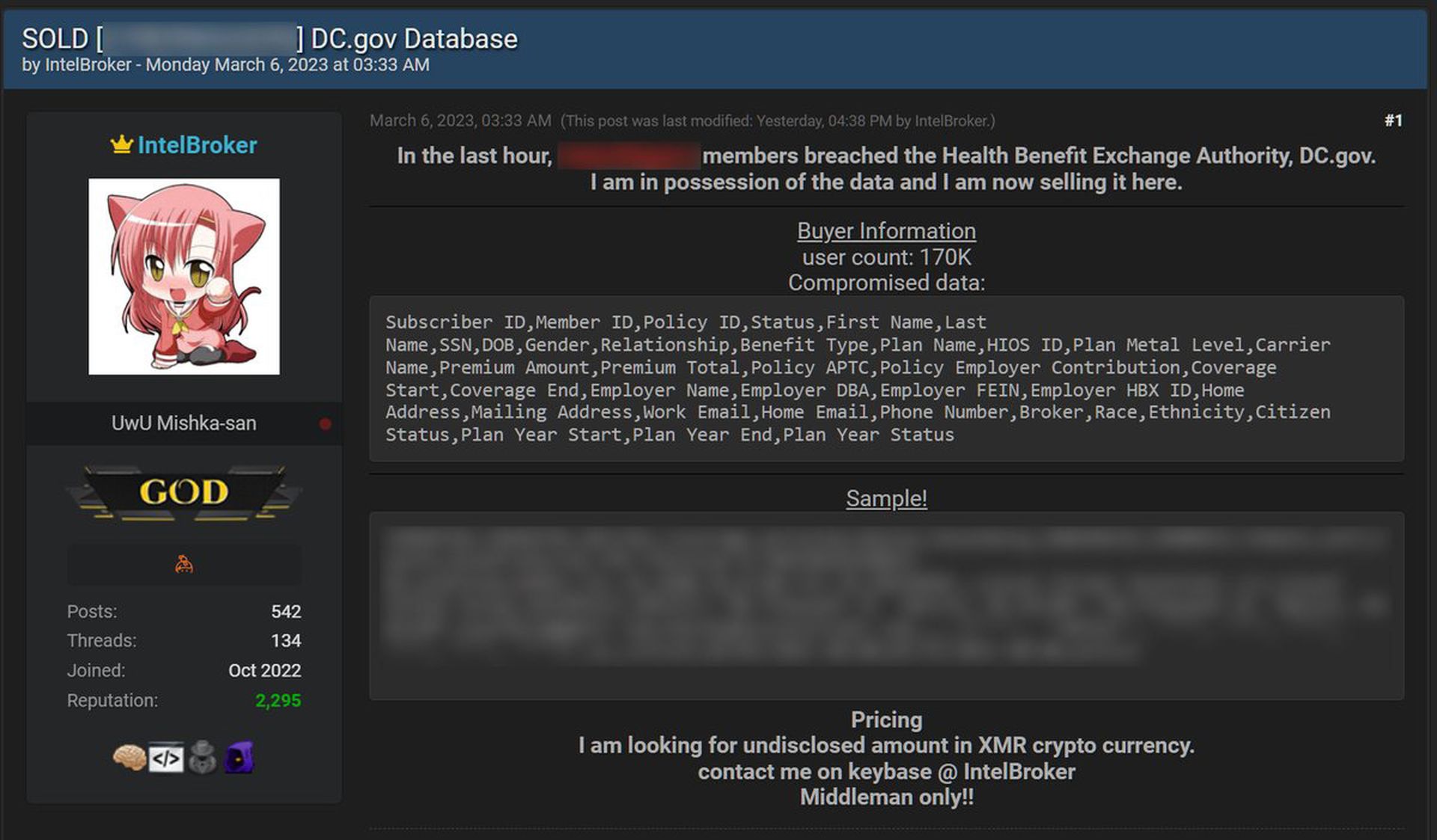
The alleged stolen data includes subscriber, policy, and member IDs, full names, Social Security numbers, dates of birth, gender, benefit types, plan and carrier names, employers, home addresses, brokers, citizen status, work emails, and a host of other highly sensitive information that could readily identity users and their locations.
IntelBroker was seeking “an undisclosed amount in XMR cryptocurrency” and only wanted to work with a “middleman.”
It’s important to note the IntelBroker “group” is suspected to be a single actor, who claimed to have hacked several U.S. government agencies in November 2022. At the time, several security researchers indicated the previous ad could be a scam in an attempt for notoriety.
FBI says House members were not targeted in DC Health Link breach
For now, the FBI is leading the investigation that may clear up these details. House members were told that Szpindor expected “to have access to the list of impacted enrollees” and will inform the affected members if their data was found to be included in the stolen data.
“It’s important to note that, at this time, it does not appear that Members of the House of Representatives were the specific target of the attack,” Szpindor wrote. It’s currently unclear whether other plan enrollees were affected.
House Speaker Rep. Kevin McCarthy, D-Calif., and House Minority Leader Rep. Hakeem Jeffries, D-N.Y., have already sent inquiries to DC Health Link to determine just what data was stolen, individuals impacted, and steps the insurer is taking to protect House members from the breach fallout.
The incident joins an earlier hack of the U.S. Marshals Service last month. Officials reported that the division of the Department of Justice discovered ransomware deployed on a stand-alone U.S. Marshals’ system where data was exfiltrated, including law enforcement officials’ legal process returns, administrative data, and personally identifiable information.




