The FBI’s Cyber Division on Friday issued a flash alert on how organizations can tell if they’re victims of affiliates of the LockBit ransomware-as-a-service.
The alert also enlists the public’s help for information, requesting boundary logs showing communications with foreign IP addresses, sample ransom notes, communications with threat actors, Bitcoin wallet information, decryptor files and samples of encrypted files.
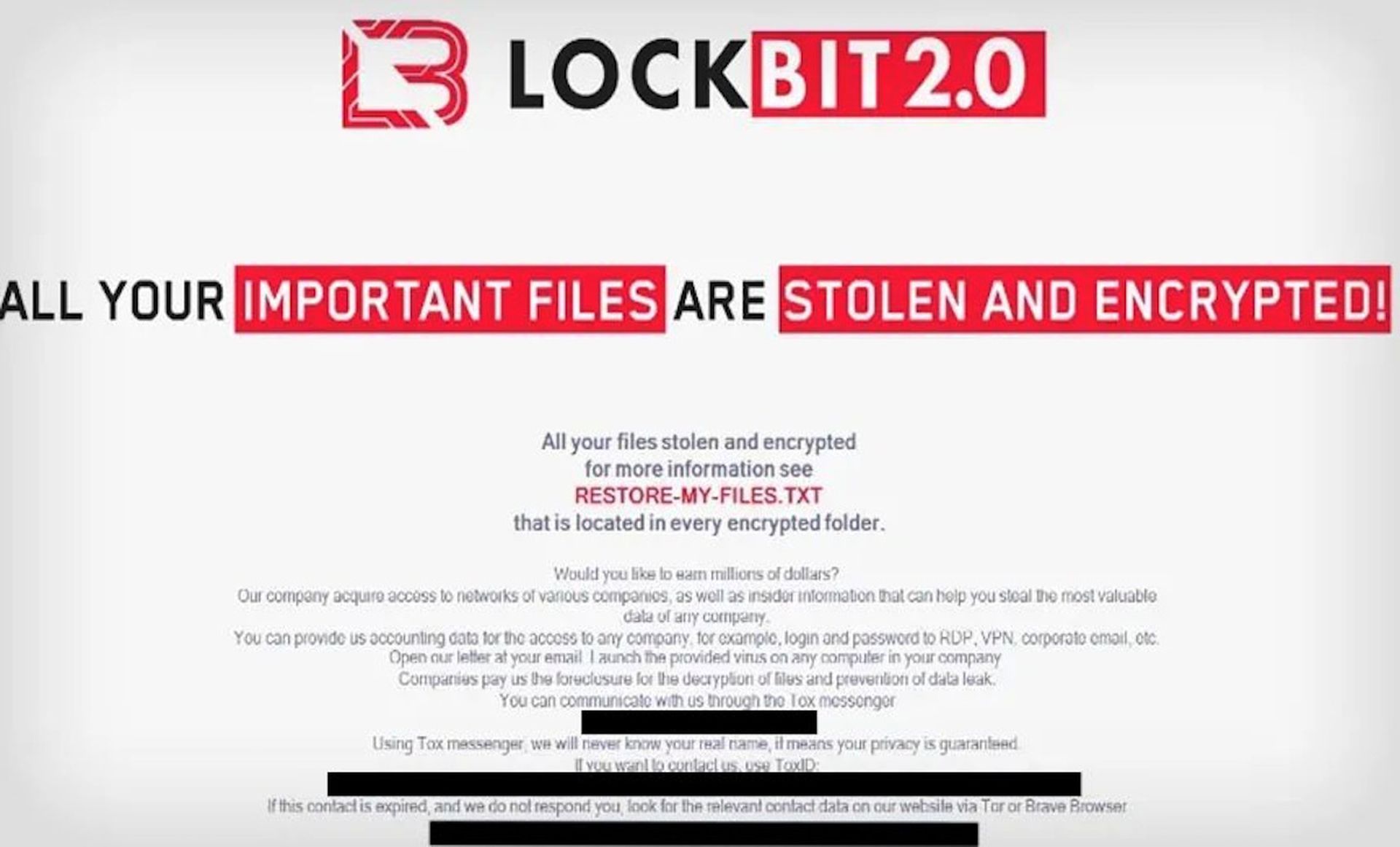
The FBI alert warned that LockBit 2.0 actors use a variety of techniques to compromise networks. The alert also noted that the ransomware determines if the targeted system uses an Eastern European language and deletes itself without infection if it matches a set list of languages. SC Media has reported that 90% of ransoms are paid to ransomware that avoids victimizing Russian-speaking countries.
The alert noted that the group released an update in July that automatically encrypted devices across Windows domains by abusing Active Directory group policies. In August, the ransomware gang began advertising to split proceeds of successful attacks with insiders who establish initial access to networks. LockBit 2.0 also developed a Linux-based malware targeting vulnerabilities in VMWare’s ESXi virtual machines.
The FBI recommends cybersecurity professionals require strong passwords, multi-factor authentication and updated software, among others, as ways to reduce the risk of compromise from LockBit 2.0 ransomware.
View the FBI’s alert here to view technical characteristics that indicate a compromise and further resources here (PDF)https://www.ic3.gov/Media/News/2022/220204.pdf.