This month, SC Labs assessed several identity and access management solutions. This review comes at a relevant time with the recent events surrounding COVID-19 and the global shift to working from home. The traditional, known perimeter has grown increasingly immaterial over the years. The unprecedented, world-wide scramble to work remotely has emphasized that the previously known perimeter is virtually non-existent.
These trying times have mercilessly highlighted a number of cybersecurity weaknesses across industries. It is our sincere hope that these reviews find our readers in a state of proactive due diligence instead of a post-incident scramble following a lesson learned the hard way. The identity and access management solutions reviewed here guard the proverbial gates of critical organization resources, checking the IDs of everyone that attempts to enter, ensuring identities match end-user claims and privileged access is sufficient for entry. Without this cybersecurity bouncer to guard the door to your resources, malicious actors have a free pass into critical applications and data.
Product Group Opener
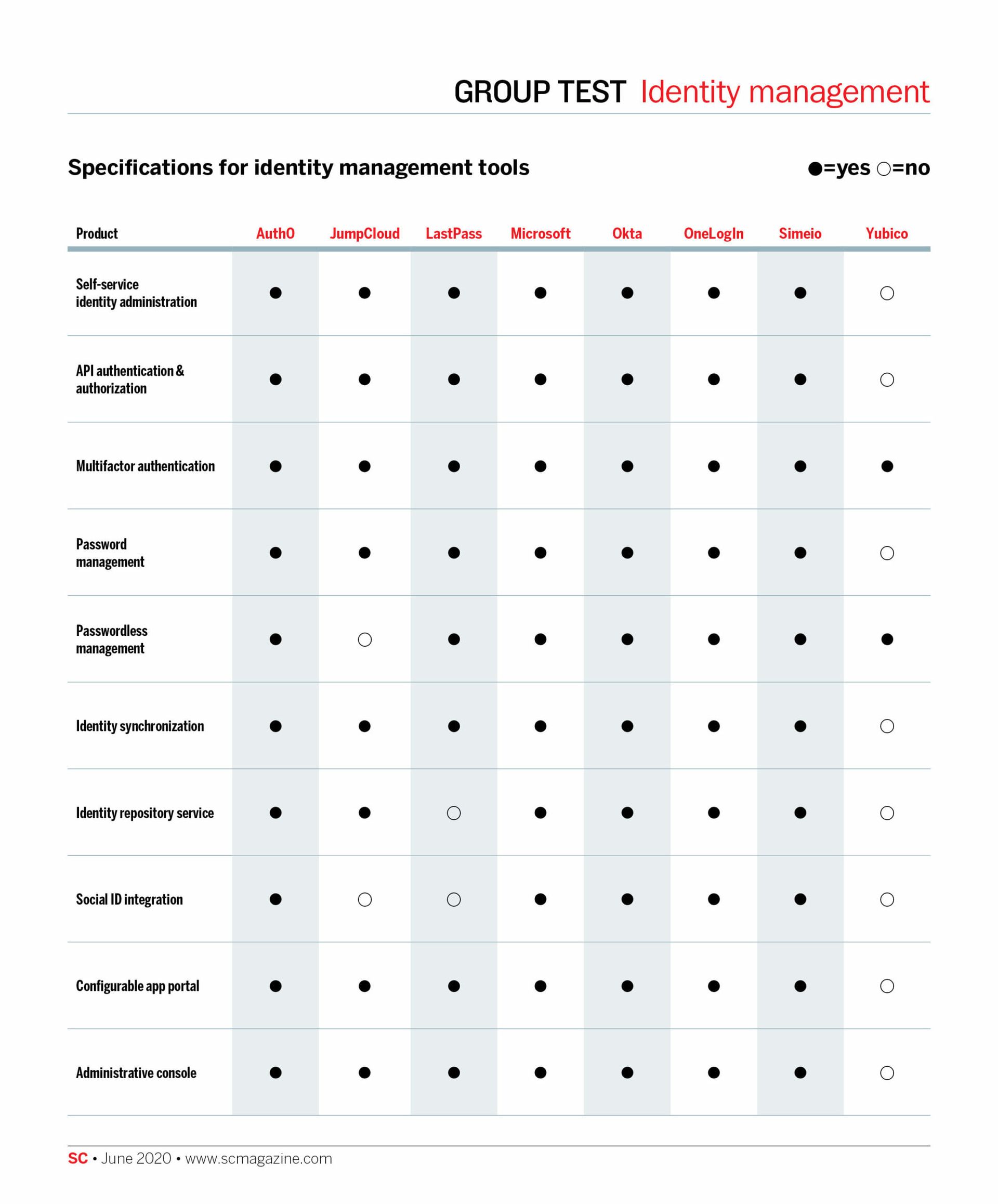
This month, SC Labs looked at a handful of products within the identity and access management (IAM) space, which collectively function as an enterprise gateway between end-users and critical organization information with centralized access control of cloud, on-premises and legacy applications and resources. The emphasis here is on the word collectively. Although these solutions nearly exclusively offer core capabilities such as authentication and authorization, the products we assessed are most effective when deployed alongside at least one other IAM solution. Several of these products already have built-in integration to support one another.
Onboarding users onto the platform, in most cases, is automated with a broad range of directory integrations. Bisynchronous relationships between the identity platform and supported directories takes the manual work almost entirely out of the hands of administrators and dramatically reduces the complexity of implementation and time-to-value.
Some of this month’s products may operate on the frontend with MSSP functionality while a paired identity and access management solution operates in the backend. This particular use case and type of deployment enables a seamless switch between IAM solutions without the need to retrain end-users. A third type of product, YubiKey (hardware), can add an additional layer of identity security functioning as a key to the backend identity and access management lock.
We see the industrywide trend of incorporating artificial intelligence and machine learning with identity solutions as well. Advanced features such as user behavior analysis enable dynamic assessments of, and responses to, varying risk at the user or session level. A baseline understanding of expected user behavior (time of day, IP address, location, etc.) enables the flagging of anomalous behavior.
Identity and access management products enhance traditional login credentials with various security capabilities including password management and analysis, single sign-on and multifactor authentication. Some of the solutions have password vaults so that end users may securely store enterprise credentials. Password management keeps tabs on the frequency with which passwords are reused and the inherent security of those passwords according to length and complexity. Single sign-on streamlines application and resource access serving as a central, unified login portal. This encourages end users to use long and complex passwords because only need to sign in once to access all an organization’s resources instead of having to log into every single individual resource. Some products even permit authentication at the workstation level.
Identity and access management products are vital to enterprise security across industries and greatly enhance existing security investments. In addition to bringing in an extra layer of security and going a step farther with data loss prevention, their capabilities and features can increase productivity and overall return on investment.
Pick of the Litter
Yubico YubiKey 5Ci offers the easiest and highest level of security available for an identity solution that is so consumer friendly. If there were an ease-of-use category, this would win by a mile. The one-touch YubiKey experience comes with a large ecosystem of integrations, a low total cost of ownership, and a substantial return on investment, making Yubico YubiKey an SC Labs Best Buy.
Okta Identity Cloud is a flexible solution with an extensive integration network that covers every identity use case for any technology. Okta reliably and efficiently enhances productivity and security, driving profitability and growth to maximize overall return on investment and to reduce the total cost of ownership, making this our SC Labs Recommended product for this month’s round of testing.
June reviews
Microsoft Azure Active Directory (Azure AD)
OneLogIn Trusted Experience Platform (TEP)
Simeio Identity Orchestrator
Click on the chart below for the full-size version