Threat monitoring service Shadowserver on Monday said that its systems recorded thousands of attempts to exploit a critical flaw on Atlassian Confluence Data Center and Server.
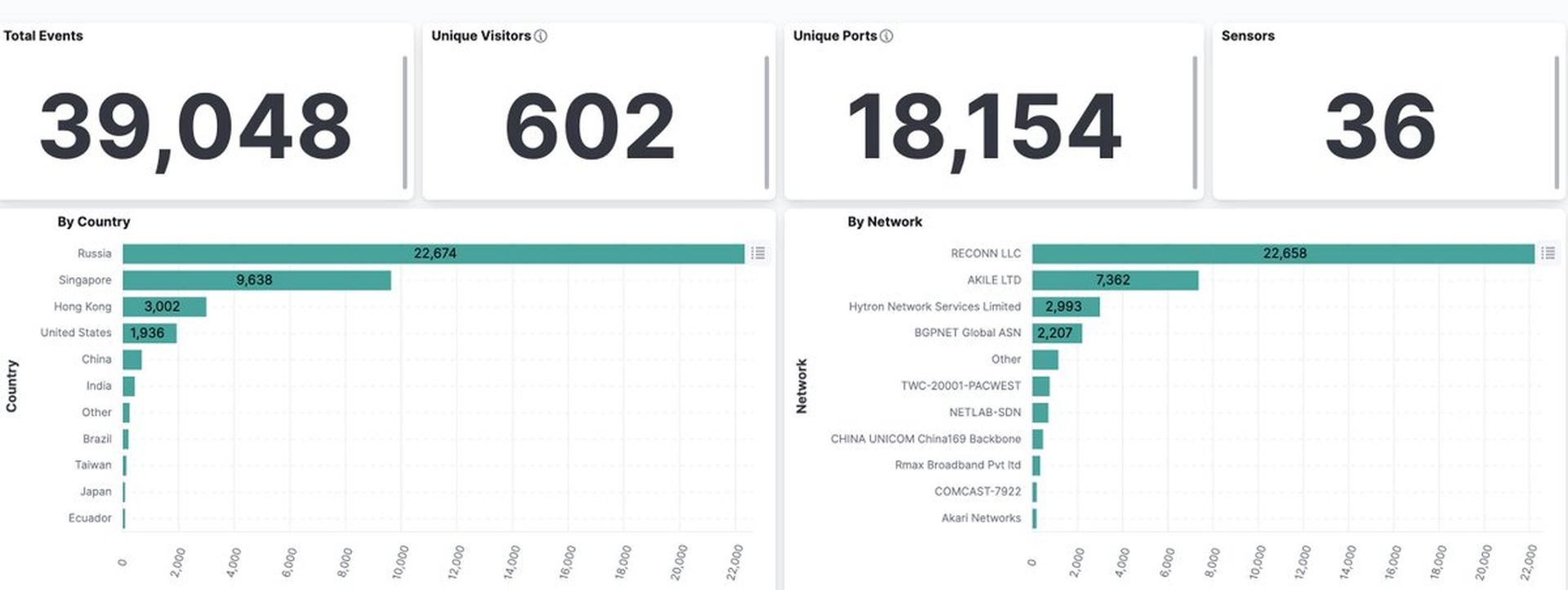
In a post to its X account, Shadowserver listed that it observed 39,048 total events across 18,154 ports and 602 unique IP addresses.
“We are seeing Atlassian Confluence CVE-2023-22527 pre-auth template injection RCE attempts since 2024-01-19. Over 600 IPs seen attacking so far (testing callback attempts and 'whoami' execution). Vulnerability affects out of date versions of Confluence:"
As SC Media reported Jan. 17, Atlassian customers using Confluence Data Center and Server version 8 are affected if they have not updated to at least 8.5.4, released Dec. 5. Atlassian recommends that all customers update to the latest Confluence version — 8.5.5 — immediately.
The critical Confluence vulnerability — CVE-2023-22527 — was given a maximum CVSS score of 10 by Atlassian because of the ability for attackers to achieve a remote code execution (RCE) in a low-complexity attack and without authentication.
CVE-2023-22527 operates as a template injection vulnerability, similar to CVE-2023-22522, which also risked RCE on Confluence Data Center and Server. However, the earlier flaw required authentication and this new now exploited vulnerability can be used to launch attacks by unauthenticated users. This latest flaw was discovered and reported by security researcher Petrus Viet on Dec. 13 as part of Atlassian’s bug bounty program.
Sarah Jones, cyber threat intelligence research analyst at Critical Start, said unlike certain vulnerabilities, CVE-2023-22527 stands out because of its severity and the broad spectrum of potential exploitation. Jones said of notable concern is the fact that attackers can exploit this vulnerability without the need for authentication, significantly amplifying the potential attack surface.
Jones also stressed that the delay in patching poses a notable concern, as it creates a window of opportunity for attackers to exploit the vulnerability. Organizations are urged to expedite the patching process, recognizing the urgency in securing Confluence instances and mitigating the associated risks, said Jones.
“In essence, Confluence instances become more susceptible, raising the stakes for organizations in terms of data and system security,” explained Jones. “The identified vulnerability introduces a multitude of risks, primarily stemming from a template injection flaw within Confluence. Malicious actors can exploit this flaw to inject harmful code into Confluence templates, leading to unauthenticated RCEs on vulnerable systems. This essentially grants attackers comprehensive control over Confluence instances, posing a severe risk to critical data.”
John Bambenek, president at Bambenek Consulting, noted thatConfluence Data Center and Confluence Server endpoints are used by organizations that have sensitive content they don’t trust in the cloud that can include code, secrets, and architecture diagrams.
“If I wanted to see the building blocks of architecture for organizations to plan out crippling ransomware attacks, Confluence is my first stop,” said Bambenek. “The flaw allows for Confluence servers that are internet-facing to have direct access to run whatever they want on those servers, whether compromising the servers themselves, stealing information to plan further attacks, or lateral movement to burrow deeper into an organization."




