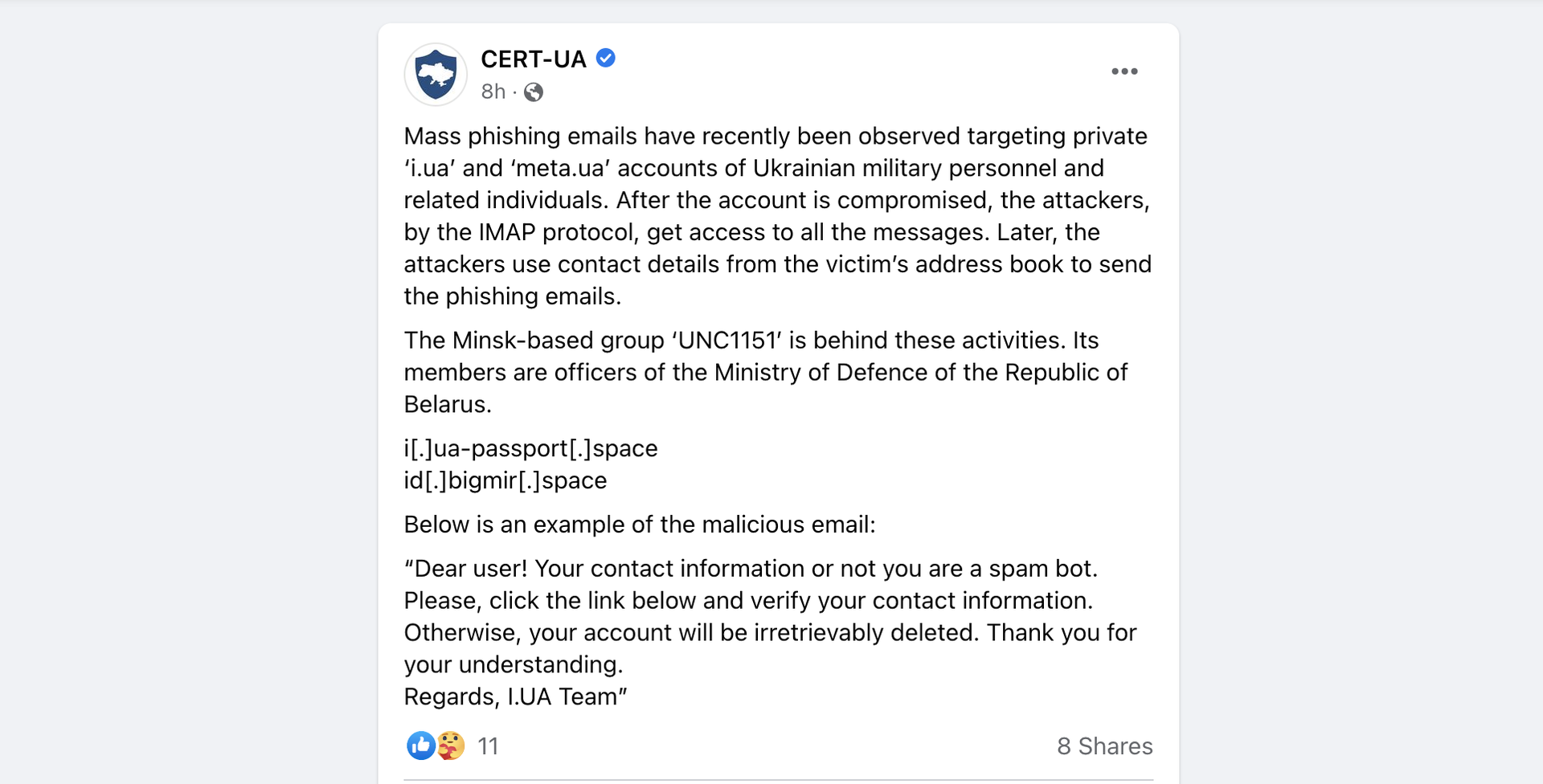
Ukraine’s Computer Emergency Response Team (CERT-UA) wrote a Facebook post early Friday about a cyber espionage group targeting Ukraine’s military personnel with phishing attempts, with threat research firm Mandiant confirming that the domains referenced are indeed attributable to a group with ties to the Belarusian government.
Mandiant specifically confirmed that the infrastructure reported by CERT.UA has ties to UNC1151, a suspected state-sponsored cyber espionage actor that the threat intel company has previously reported to engage in credential harvesting and malware campaigns. But the team has not seen the phishing messages directly.
Mandiant Director Benjamin Read did note, however, that this does match a patter of UNC1151, which has targeted Ukraine and especially the Ukrainian military extensively over the past two years. These actions by UNC1151, an "uncategorized" threat group versus one confirmed to be an advanced persistent threat (APT) or financially motivated (FIN), open the door for personal data of Ukrainian citizens and military to be exploited in an occupation scenario. "And UNC1151 has used its intrusions to facilitate the Ghostwriter information operations campaign,” explained Read, referencing a wide-ranging influence campaign that has used both hacking and influence operations to target at least 30 countries over the past several years.
“Leaking misleading, or fabricated documents taken from Ukrainian entities could be leveraged to promote Russia and Belarus-friendly narratives,” said Read. “Ghostwriter has previously targeted the NATO alliance, seeking to erode support for the organization. I wouldn’t be surprised if similar operations were seen in the near future.”
John Hammond, senior security researcher at Huntress, added that Belarus has been involved in the Ukraine/Russia conflict by enabling attacks from Russia and participating in the armed battle – so seeing phishing attempts or other malicious cyberattacks from an actor linked to Belarus is unfortunately no surprise.
“While a phishing attack offers initial access, the next threats may be data exfiltration, cyber espionage, and other efforts in information ops or continued compromise to gain even more access,” Hammond said. “While we can't say for certain, it's not unrealistic to think there will be more disruptive or degrading effects that follow.”
Rick Holland, chief information security officer and vice president of strategy at Digital Shadows, said the ubiquity of technology, including mobile devices and social media platforms, means that war now gets televised in real-time. Holland added that despite OpSec requirements, the modern soldier has become highly interconnected, which presents another avenue of attack for adversaries.
“Compromising personal accounts of the Ukrainian military can disrupt and demoralize the troops, providing additional challenges in an already mismatched campaign against Russia,” Holland said. “You could expect the 2015 Office of Personnel Management stolen data weaponized similarly in a future conflict with China.”




