By Stu Sjouwerman, CEO, KnowBe4
If there is one thing that characterizes almost all phishing emails, it is the element of deception. And the most common way for bad guys to pull the wool over users' eyes is to employ social engineering schemes that leverage users' trust in well-known brands, prominent companies, popular websites, ubiquitous online services, and individuals known to users both inside and outside their own organizations. A relationship based on misplaced trust solves so many problems for malicious actors.

Trust is a funny thing, though. While trust often develops organically over a period of time, trust can also be generated or backstopped with some element of compulsion and authority. When you don't have much of a choice, trust can seem the easier path to take. And the best example of this dynamic is the relationship that employees enjoy with their organizations' HR departments. Whether your company's HR department is beloved, feared, or loathed, it is a center of power in most organizations that few employees can afford to ignore.
Although the bad guys have been spoofing HR departments (along with IT departments) for a number of years, HR-based social engineering schemes have never been as common as, say, spoofs of well-known online brands like Google, Paypal, Docusign, or large banks (Wells Fargo, Bank of America, etc.).
We suspect this disparity can be attributed, at least in part, to the difficulty malicious actors might have in understanding the relationships between HR departments -- a staple of Western business culture -- and the organizations they serve. IT help desks, by contrast, would be much easier for malicious actors to understand and spoof. Indeed, many of the shock troops prosecuting phishing campaigns may even have IT experience themselves.
Moreover, HR communication is largely internal to organizations, making it more difficult for bad guys to obtain ready-to-exploit, working examples of HR-themed emails. While standard Google email notices to users are relatively easy to obtain and spoof, believable HR email templates would need to be carefully fished out of compromised email accounts.
Over the past few months, we have observed a marked increase in HR-themed phishing campaigns, a rise we suspect is fueled by improved access to legitimate HR emails harvested from compromised corporate accounts. The HR-themed phishing emails now landing in users' inboxes are often very convincing and cover the full range of services that HR organizations provide to employees.
Let's take a look at some of the more common and noteworthy HR-themed phishes recently reported to us by customers using the Phish Alert Button (PAB).
- Codes of Conduct & Employee Policies
The most common HR spoofs reported to us over the past few months push employees to open and read codes of conduct and other policies governing expected employee behavior. This fairly typical example is marked by the suitably straightforward, if slightly stilted, language one would expect in such a corporate announcement, although it is still marred by minor syntax errors.
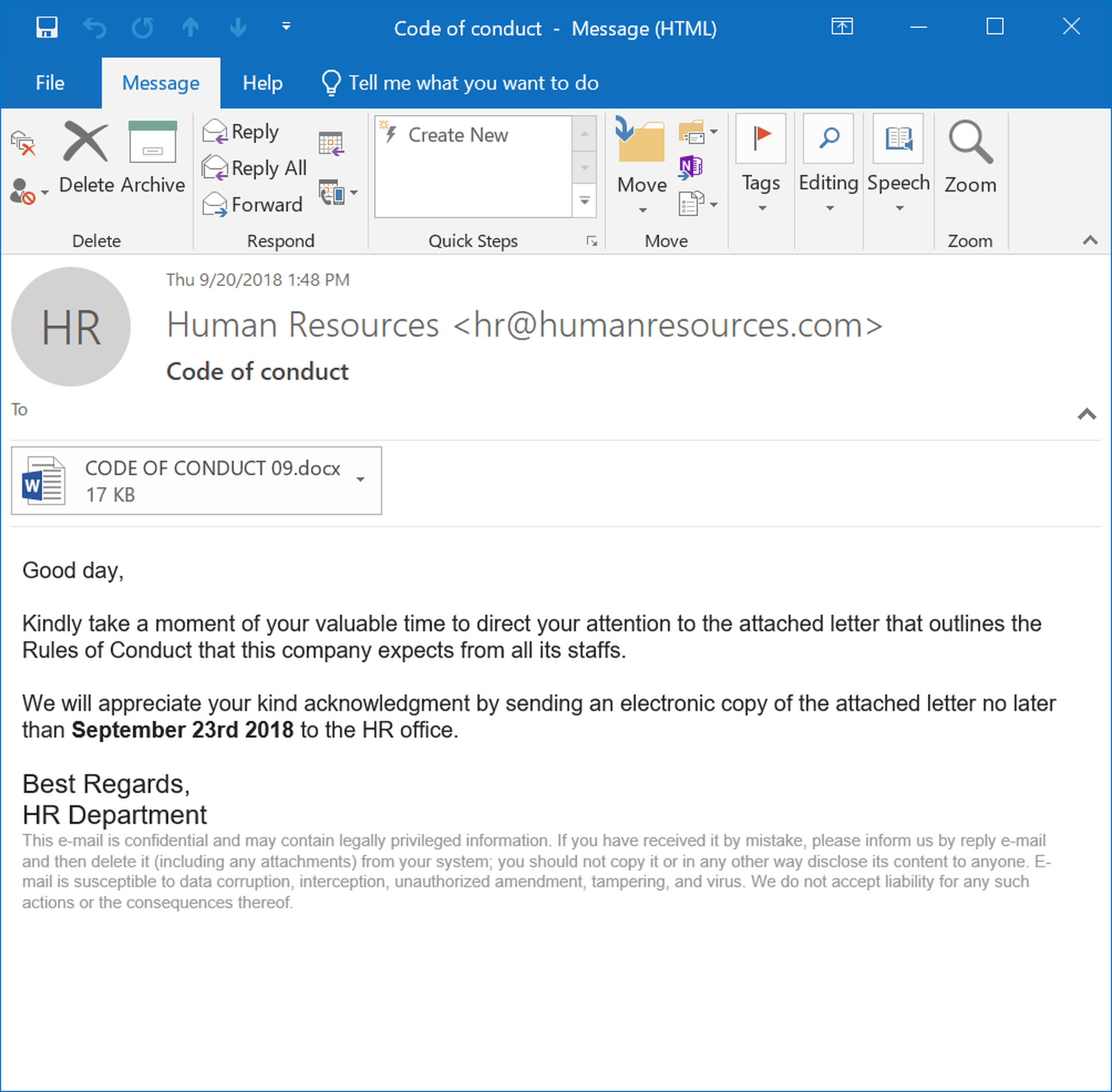
The email's attached word document is cleverly designed, providing a convincing preview of the letter's content while still requiring users to click through to a malicious external website.

While similar in many ways, this second example email declines to provide specifics, relying more heavily on the inherent authority of HR to compel users to click a malicious link.
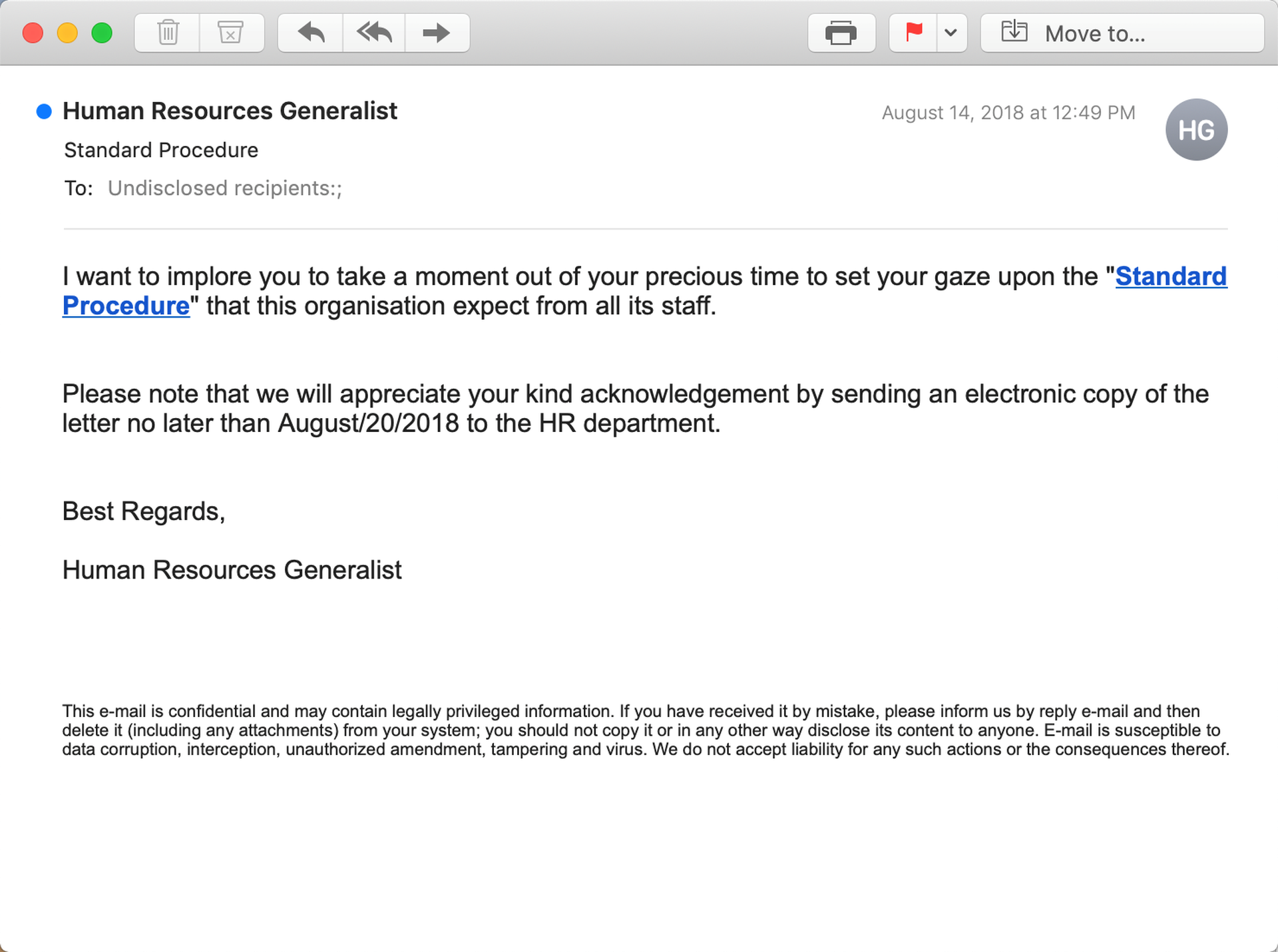
We continue to see numerous emails involving ethics standards, guidelines governing conflicts of interest, and employee handbooks, to name a few.
2. Time Cards, Paychecks, Pay Stubs & Benefits
Many of HR's core functions are good grist for effective social engineering schemes because they involve a subject of obvious compelling interest to most employees: payroll and other forms of compensation.
Despite the advantage of exploiting that most basic of human motivators -- money -- some malicious groups still struggle with the format and language of these emails:
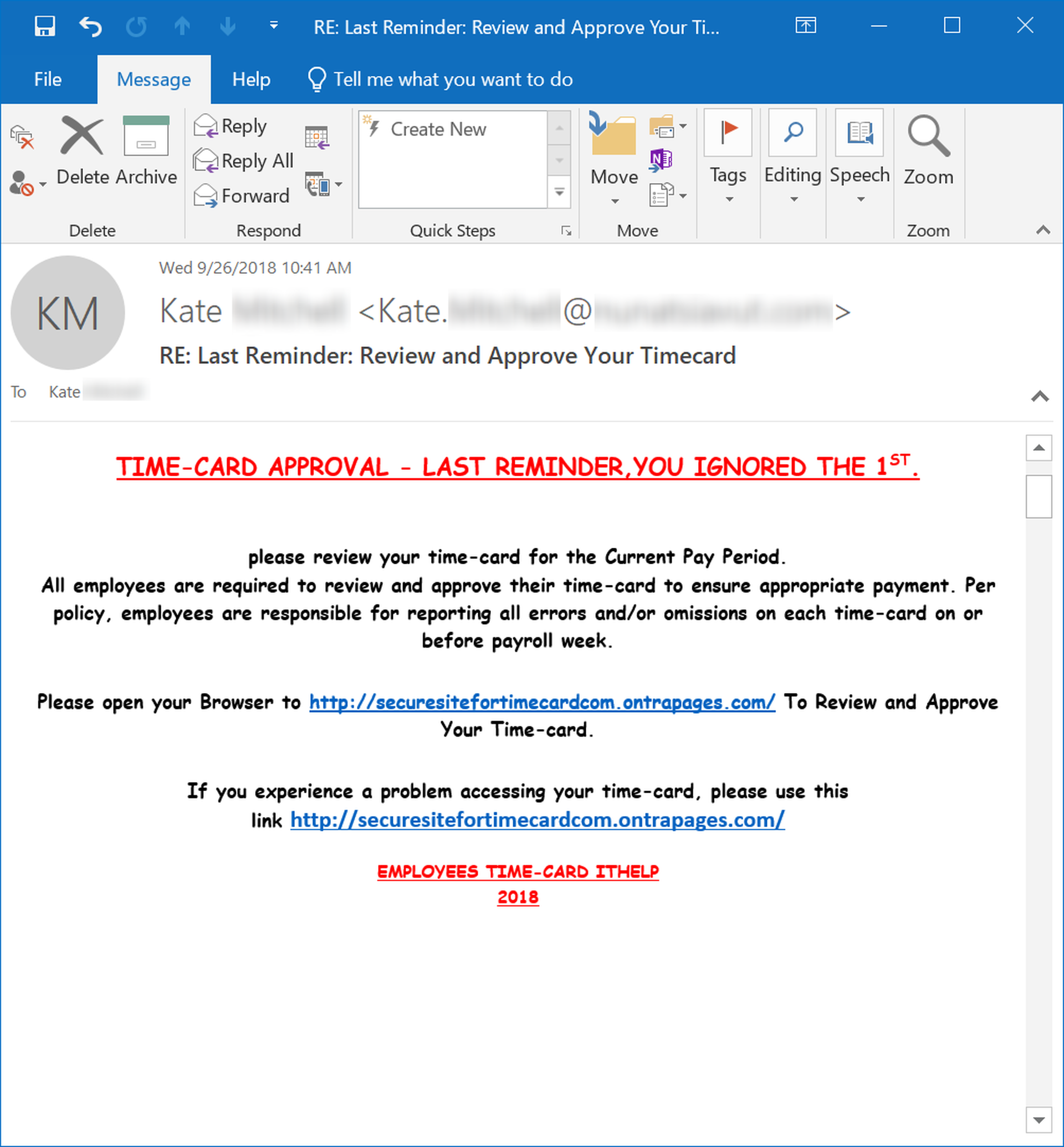
In standard business communication, though, less is often more than enough, particularly when that old reliable stand-by of scam artists the world over -- free money -- can be re-outfitted to push a malicious link that many users will find difficult to resist:
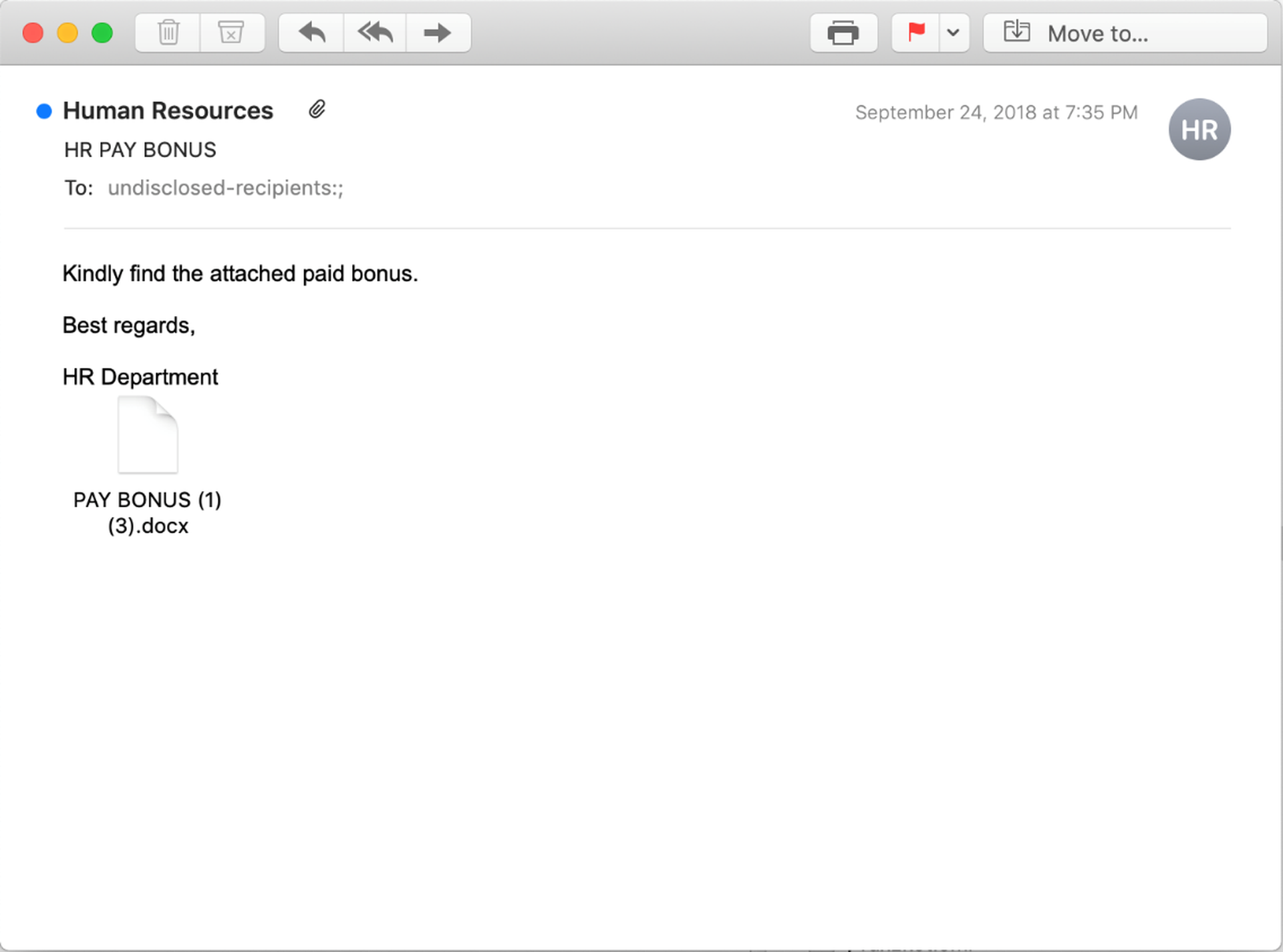
And when HR stands as a gateway to full compensation, the security of login credentials could well prove a secondary consideration to employees more interested in the security of their own health and finances.
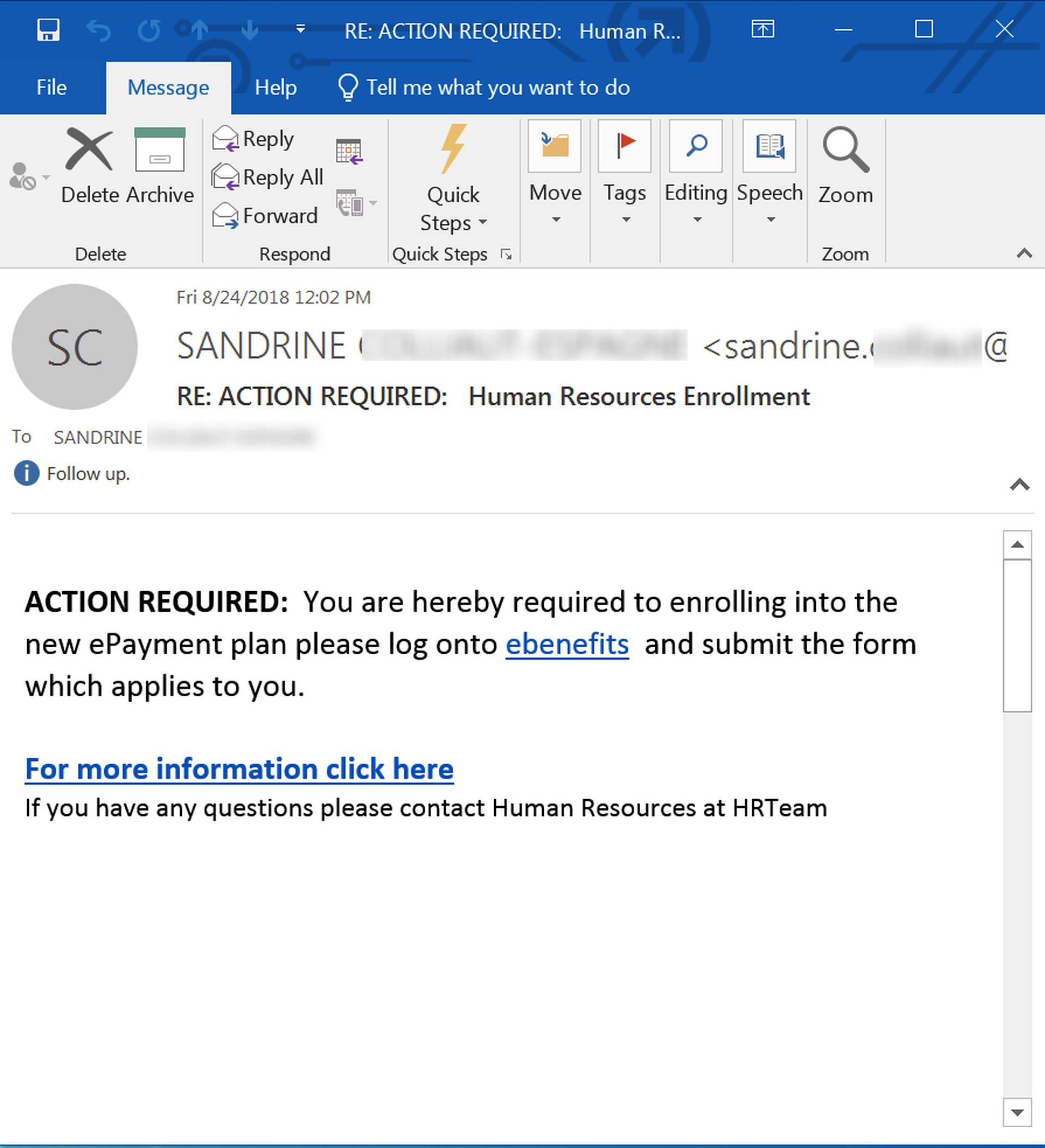
3. PTO, Vacation, & Sick Time
Like those governing employee standards and behavior, policies and processes surrounding employee attendance are core to HR organizations, and most employees will sit up when receiving emails announcing changes to an organization's handling of PTO.
This next example email, which was almost certainly pilfered from a compromised inbox, is notably sophisticated in its use of supplementary detail and suitably bureaucratic language to enhance its credibility and nudge users to click the embedded link.
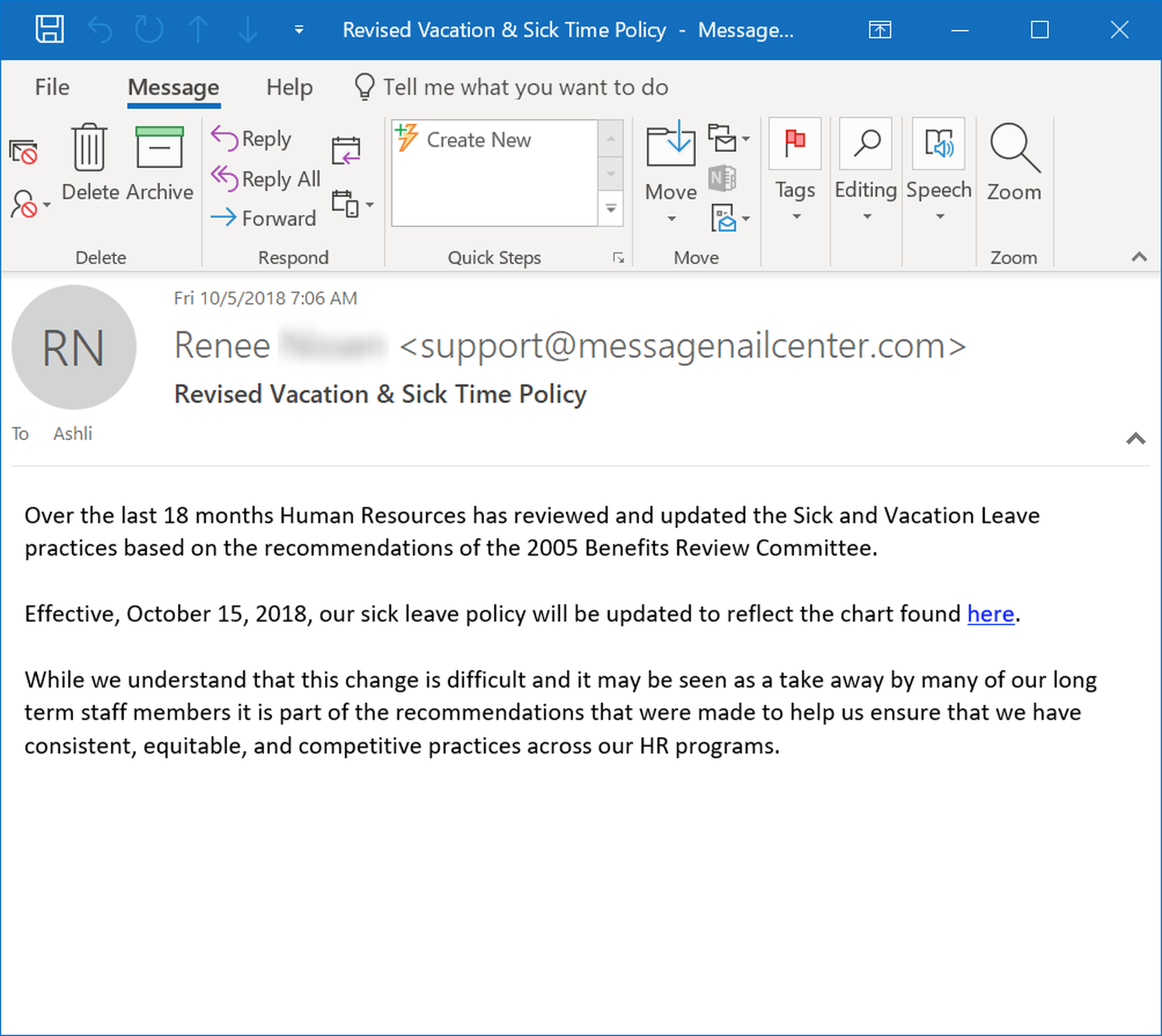
As with so many of these malicious examples, an email that seems routine and otherwise unremarkable is often the most dangerous.
4. Screenings & Evaluations
HR departments have a unique ability to generate fear and anxiety among employees -- both emotions that can put users on their back foot when confronted with a malicious email.
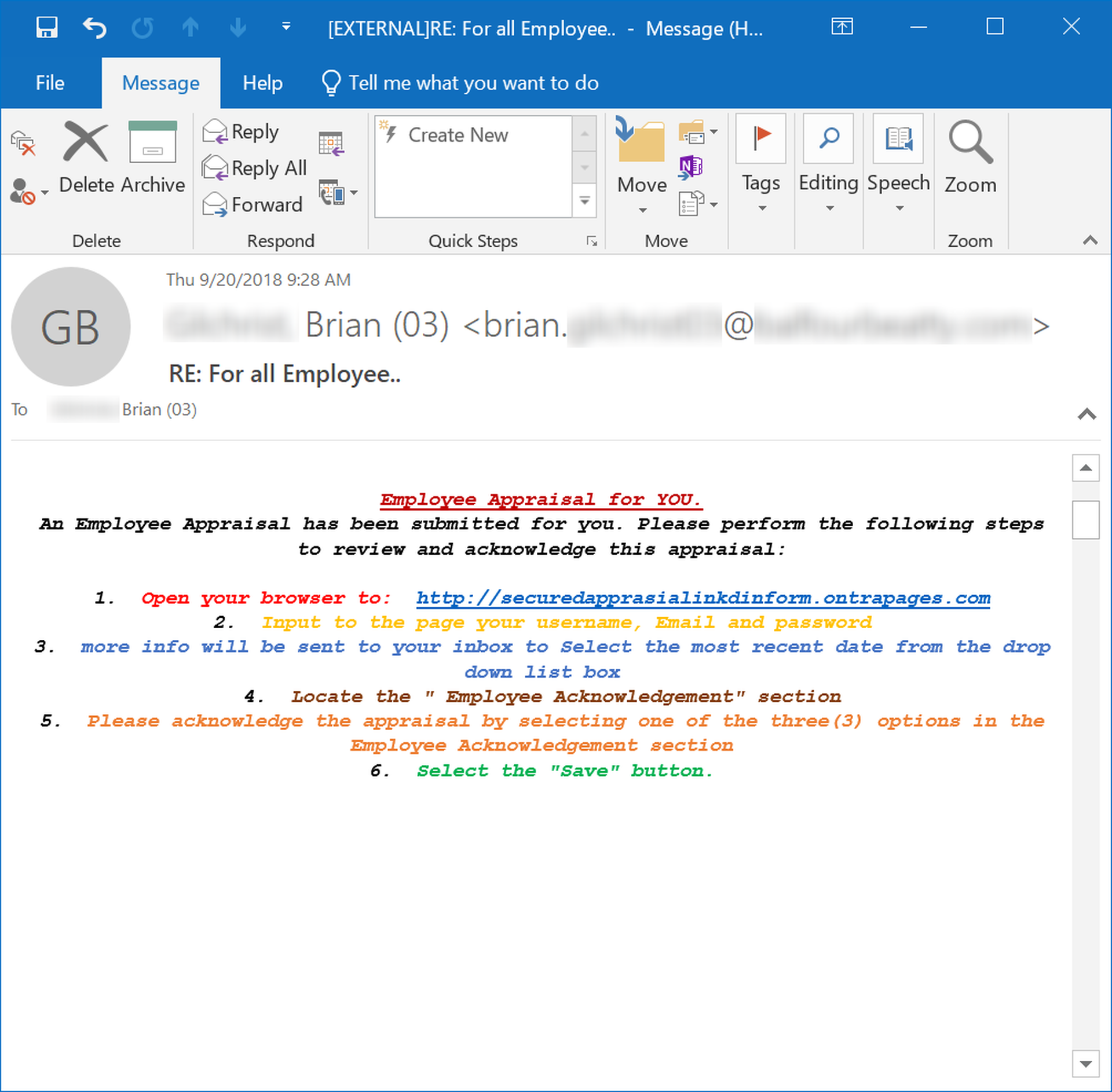
Note that the above email appears to hail from the same group that was behind that time card phish we looked at earlier. As before, the language and format of this email just might tip off attentive employees that something is amiss -- if they see past their own understandable concerns at undergoing an annual performance review process.
Performance reviews and evaluations also provide malicious actors an opportunity to target managers and supervisors within the organization (and don't think for a minute that it's beyond the bad guys to get their hands on your company's org chart).
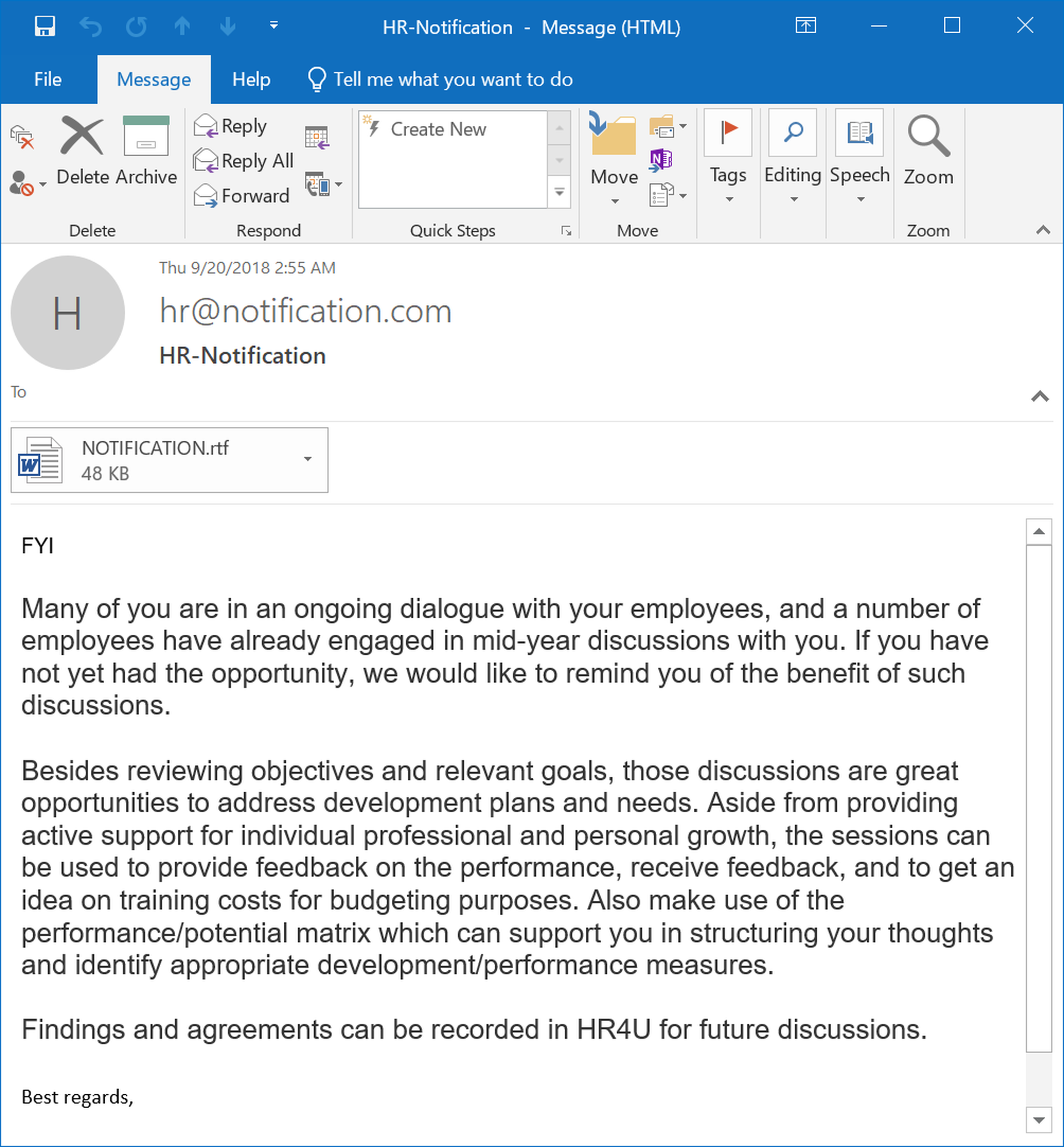
Once again the template for this rather convincing spoof was almost certainly pulled from a compromised account.
5. Surveys & Web Portals
Many HR organizations are taking steps to expand their engagement with employees, soliciting their feedback and input to make the work experience and environment more attractive. The bad guys have taken noticed and are perfectly happy to survey your employees for you.
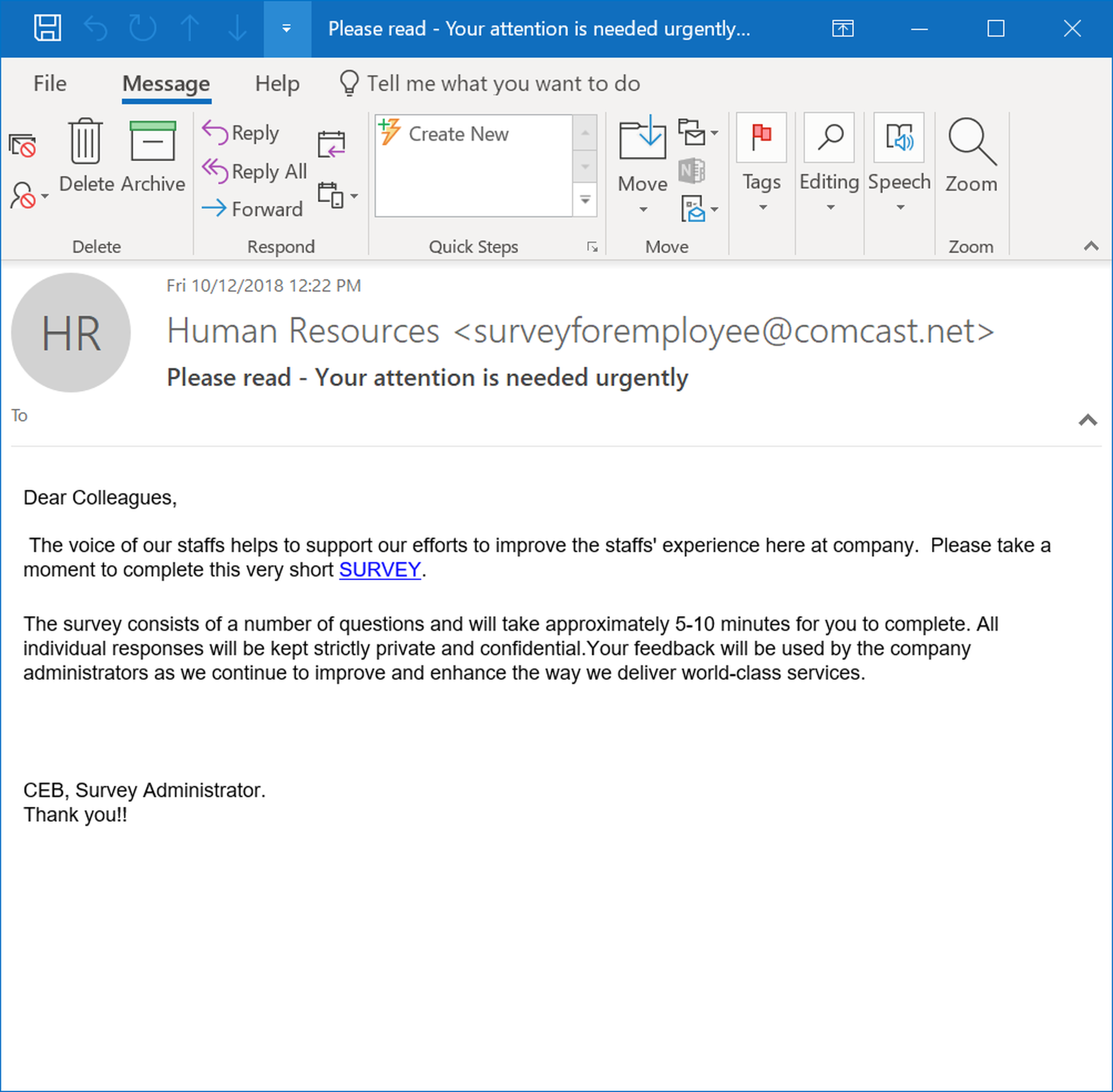
Of course, these employees will have to cough up their credentials before accessing what looks to be a fairly standard survey web page.
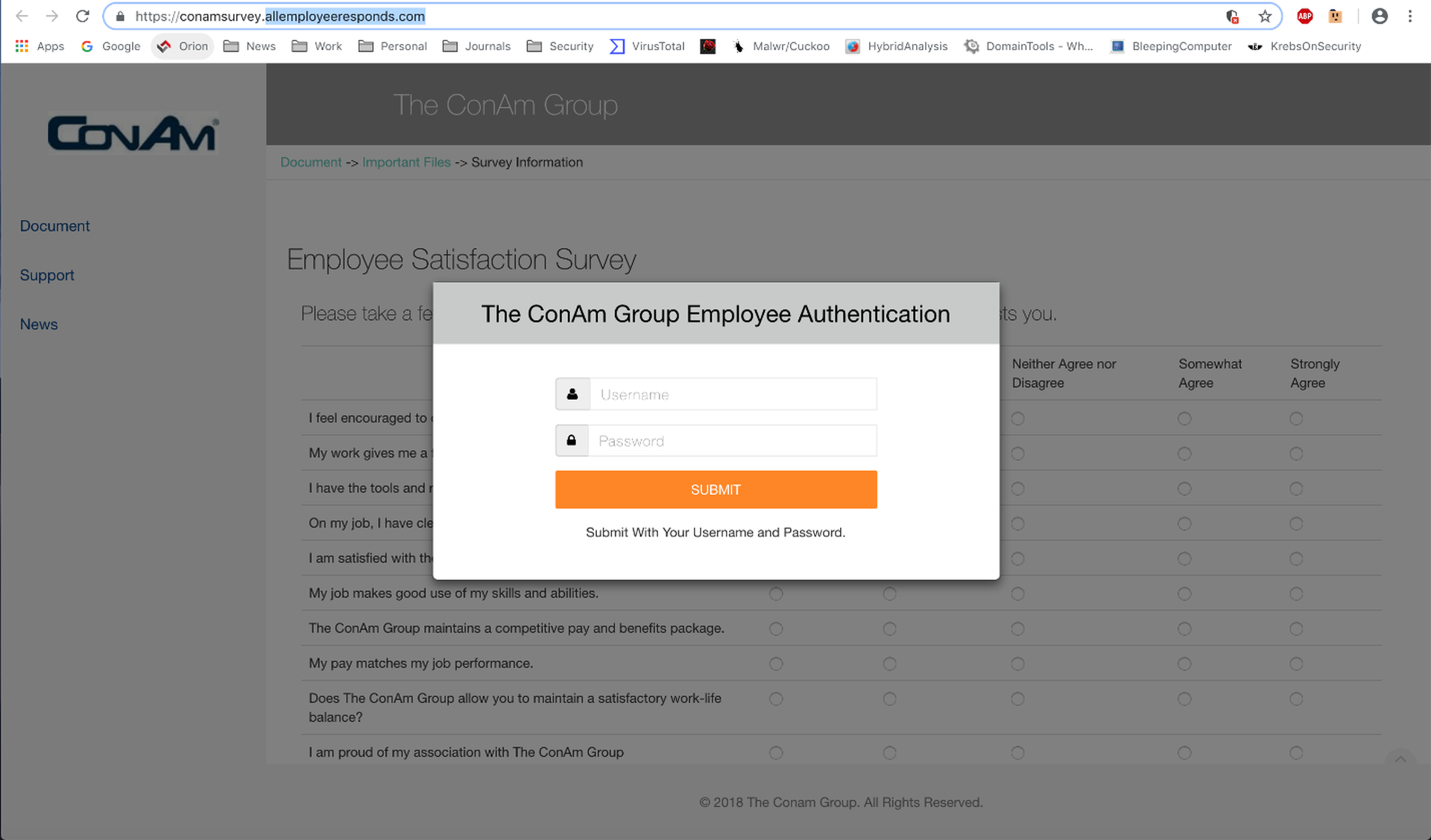
The bad guys are even savvy enough to know that many employees will appreciate a dedicated HR portal useful for handling tasks like scheduling PTO and managing benefits.
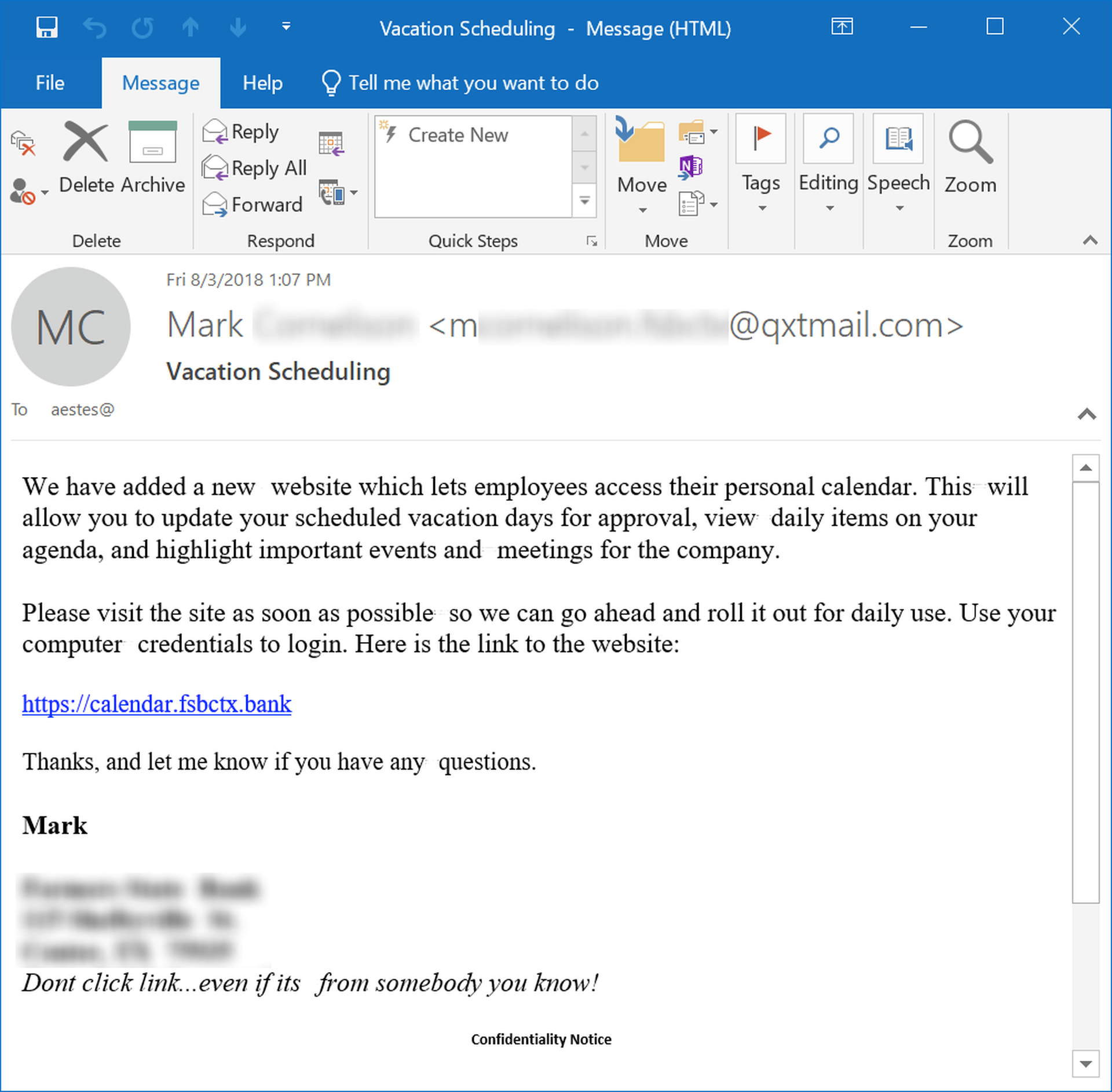
Again, the bad guys still have some catching up to do on this particular front. While malicious actors have been known to spoof similar emails involving ADP.
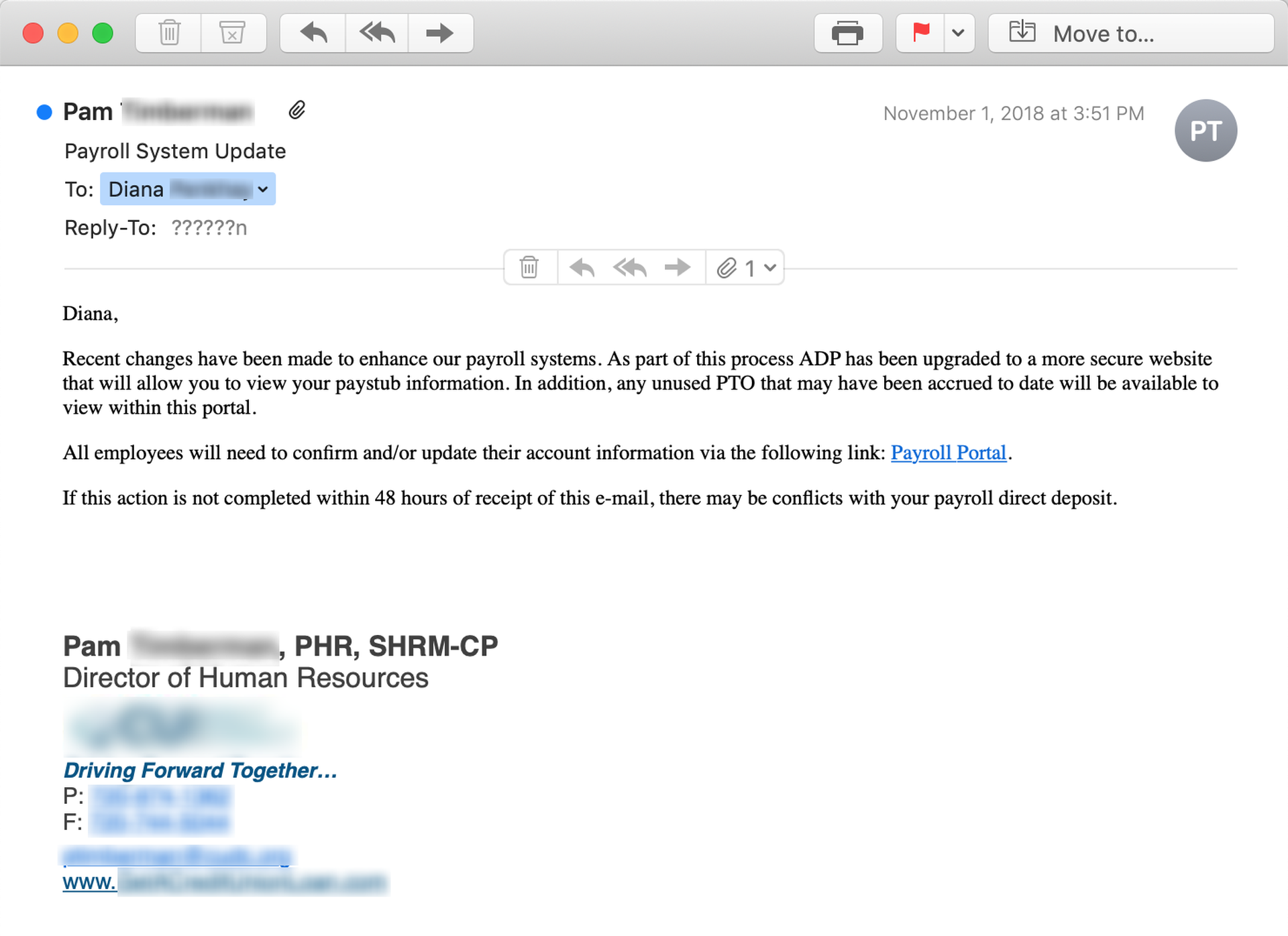
...they do not seem as familiar with other commercial SaaS offerings from other companies like Zenefits, BambooHR, or Gusto. As noted earlier, it's probably just a matter of time before convincing spoofs involving ADP's competitors begin showing up.
That malicious actors have become woke to the possibilities for leveraging the authority of HR within organizations should be very clear at this point, though. Here's an attempt to drag HR into what is otherwise a run-of-the-mill IT-themed phish.
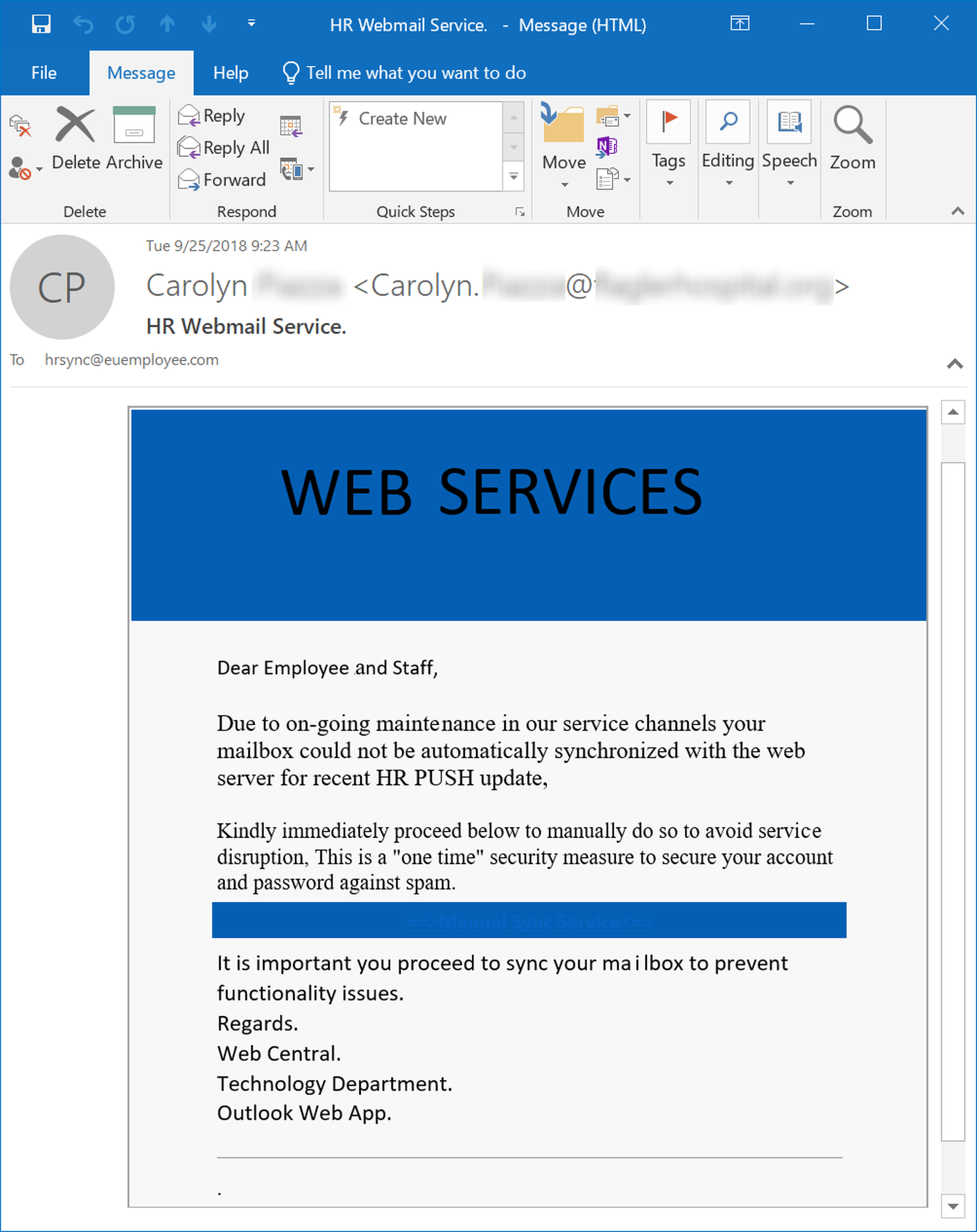
No one, of course, would want to be missing updates and notifications from HR.
Conclusion
Phishing emails have long had a reputation among end users for being linguistically crude, occasionally lewd, and frequently laughable -- a collection of foibles and follies that are all too easy to spot by anyone paying attention. Anyone who has been working in IT over the past five to 10 years, however, knows that such a reputation dangerously underestimates the increasing sophistication seen in social engineering schemes employed by malicious actors in today's phishing campaigns.
As the bad guys continue to compromise corporate email accounts and gain access to the routine communications that characterize everyday office life, they are becoming increasingly savvy about leveraging and exploiting the trust placed by employees in parts of the organization that lie beyond IT and the help desk.
While most employees will need little training or incentive to respond to the authority invested in HR, many will need help when confronted with malicious emails designed to exploit their regard for this authority and use it against them. Even naturally skeptical users will hesitate before sending what appears to be an email from HR to the trash. The links and attachments in such emails fairly demand to be clicked and opened.
As we noted at the outset, trust is a tricky thing. It can be earned and learned. It can also be misused, exploited, and broken. When malicious actors seek to abuse the trust your employees invest in HR, those employees are put in an understandably difficult spot.New-school security awareness training is designed to help your users navigate just these kinds of troubled waters, teaching them the fundamental skills necessary for spotting malicious emails and resisting the temptation to reflexively op



