| Product: CyCognito Platform | Category: Attack Surface Management |
| Company: CyCognito | Review date: April 2021 |

This review is part of the April 2021 assessment of the Attack Surface Management (ASM) product category. If you haven’t read the category overview, you might want to check it out – it explains the category’s basics, use cases and the general value proposition. Our testing methodology explains both how we interact with vendors and how we tested these products. In short, ASM products aim to discover and manage an organization’s external digital assets. This approach extends far beyond assets with an IP address, however, including everything from certificates to S3 buckets to DNS misconfigurations.
Company background
CyCognito was founded in January 2017 by Rob Gurzeev, CEO, and Dima Potekhin, CTO. The company takes the tried and true approach of a US business headquarters (Palo Alto) with the tech team located in Israel (Tel Aviv). The company employs around 100 people globally. The CyCognito Platform was launched Nov. 19, 2019 and currently serves over 50 paying customers in the Global 2000, according to the company.
CyCognito has raised three rounds of funding, totaling $53 million. The latest round, led by Accel, was a $30 million Series B announced in mid-2020. Lightspeed Venture Partners, Sorenson Ventures and UpWest participated in the Series B and previous rounds.
Product summary
CyCognito has one of the most functional, mature and stylized user interfaces (UI) of all the ASM tools we tested. Maybe it just comes down to personal preference, but it seems like more security tools should embrace the dark mode trend. The UI isn’t all flash and no substance, however, as we explore in more detail in the Usage section of this report.
CyCognito is firmly in the category of ASM products that focus on risk analysis and prioritization. The platform gives an A-F letter grade and it is important that this grade isn't an average of all assets. The issue with averaging risk across findings is that a large number of non-risky assets could potentially raise the overall grade, giving a false sense of security. Even one risky asset could result in a breach, so it makes sense for the overall grade to resemble the biggest individual risk.
A key challenge in this space when attempting to perform risk analysis and identify issues are false positives. Making assumptions based on banner output or keyword searches are common techniques that have a higher tendency to produce false positives. CyCognito is one of the few vendors that perform some active security testing in an automated manner to increase confidence in findings (each finding scores a confidence level on a 100 point scale, in fact). This testing can validate whether an FTP service requires TLS, discover SQL injection, and identify exposed internal network devices, for example. This can cut down significantly on manual validation work, especially at larger scales.
Target market: CyCognito’s asset-based subscription pricing is flexible, but starts above what an SMB could afford. The company is currently targeting large enterprises, likely to meet growth goals and maximize the value from a long-ish sales cycle, if we were to guess. There’s no functional reason the product couldn’t move down market in the future – it’s more a question of the company reducing acquisition cost to the point where it starts making sense to go after smaller deals.
Time-to-value: Allow 30 minutes for initial account setup and team configuration. Initial results will be available after a few hours, with full results after a few days. Integrations could take anywhere from a few minutes to several hours, depending on whether any custom work needs to be done. A large enterprise should expect to spend 40-60 hours digging through initial results, which will vary depending on size of the organization’s external footprint.
Maintaining value: In a large enterprise, expect to spend 6-12 hours per week reviewing new findings, organizing them and validating issues.
Total cost: Pricing is an annual subscription based on number of Internet-exposed assets with tiered discounts as the number increases. CyCognito declined to share specific pricing information, but our guess is that the annual cost will be comparable to what a large enterprise typically spends on an annual penetration test. As for labor costs, in a large enterprise (10,000+ employees), we’ve estimated 24 hours of junior analyst time, 12 hours of analyst time and six hours of senior analyst time to do the initial analysis of CyCognito results, some tuning and integration work. Based on our average salary estimates, this labor totals $1,817.22. For ongoing analysis work, we’ve estimated six hours of junior analyst time per week, which totals $10,498.80 per year.
Strengths: Strong core ASM features. One of the strongest and most usable UI/UX in the ASM market.
Weaknesses: Stops short of validating many types of issues (software exploits, for example), though it does validate some issues with provided evidence.
Conclusion: One of the most comprehensive offerings in the ASM space and one of the most advanced in terms of seed discovery.
Deployment and configuration
As with many other ASM products, the initial seed values are entered by the vendor as the customer’s SaaS environment goes through initial provisioning. We found it initially surprising that CyCognito doesn’t appear to support native MFA. Then we realized that nearly 100% of their target market will likely be using SSO integrations, which will handle authentication (including MFA) outside the CyCognito Platform.
Initial tuning of the product is straightforward. To share an example, when first exploring the product, we noticed the default dashboard features a world map, showing the geo-location of IP addresses. To our surprise, the map was suggesting we have assets in Brazil and France? That didn’t seem right.
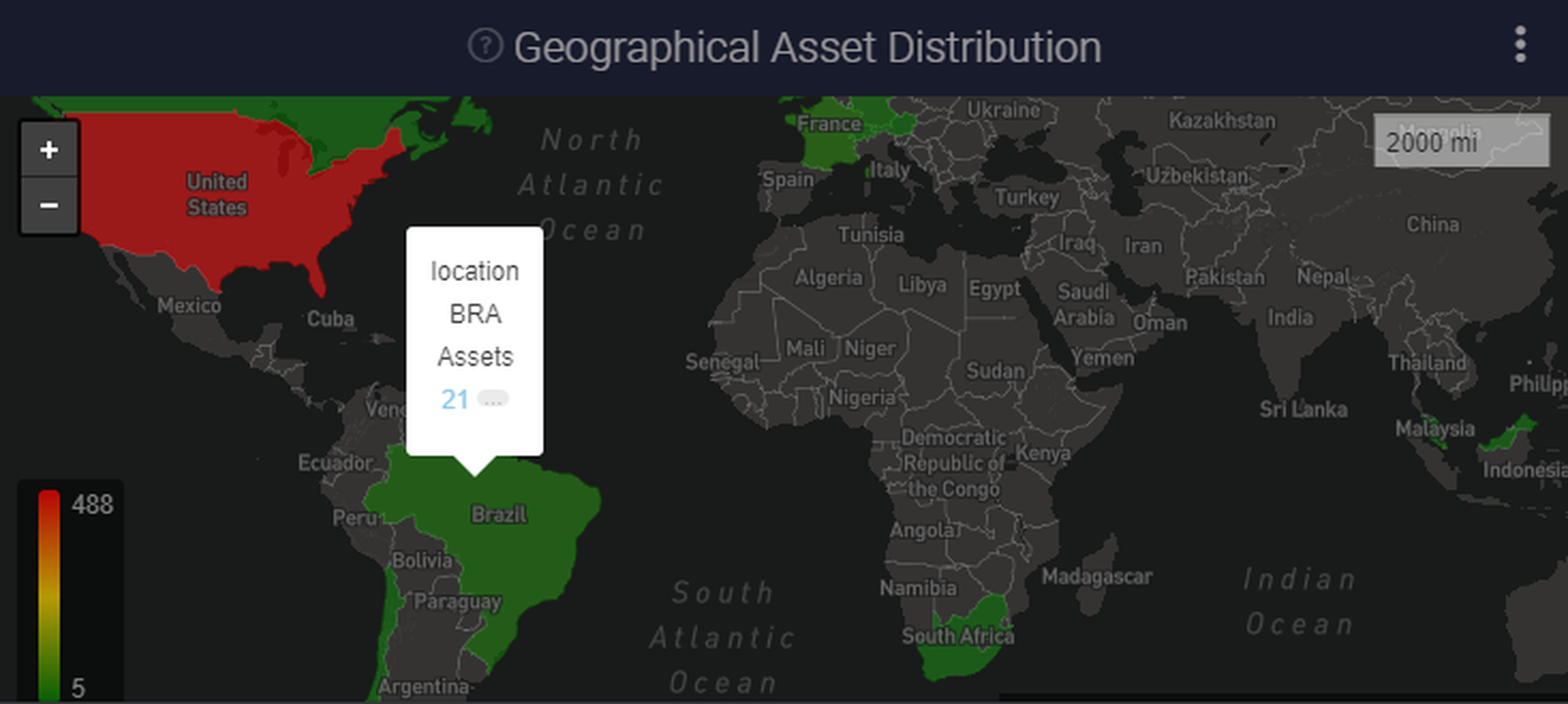
Selecting Brazil, it was easy to open 21 related assets in a new window. It quickly became clear that these were all Office365 resources - they nearly all have the 'autodiscover' CNAME and are helpfully tagged as "Microsoft Office 365" under Platforms.
While these aren't technically false positives, they're noise to me at the moment, so I want to filter them out. A quick filter (Platforms = Office 365) gives me 180 Office 365 assets, which I can then select and exclude from all future dashboards and queries. If I change my mind, it’s not a problem - I can either check the "show removed assets" option, or use the same process to bring them back into normal query results, reports and dashboards. The “Exclude asset” dialogue box even prompts to include a comment explaining why these assets are being excluded.
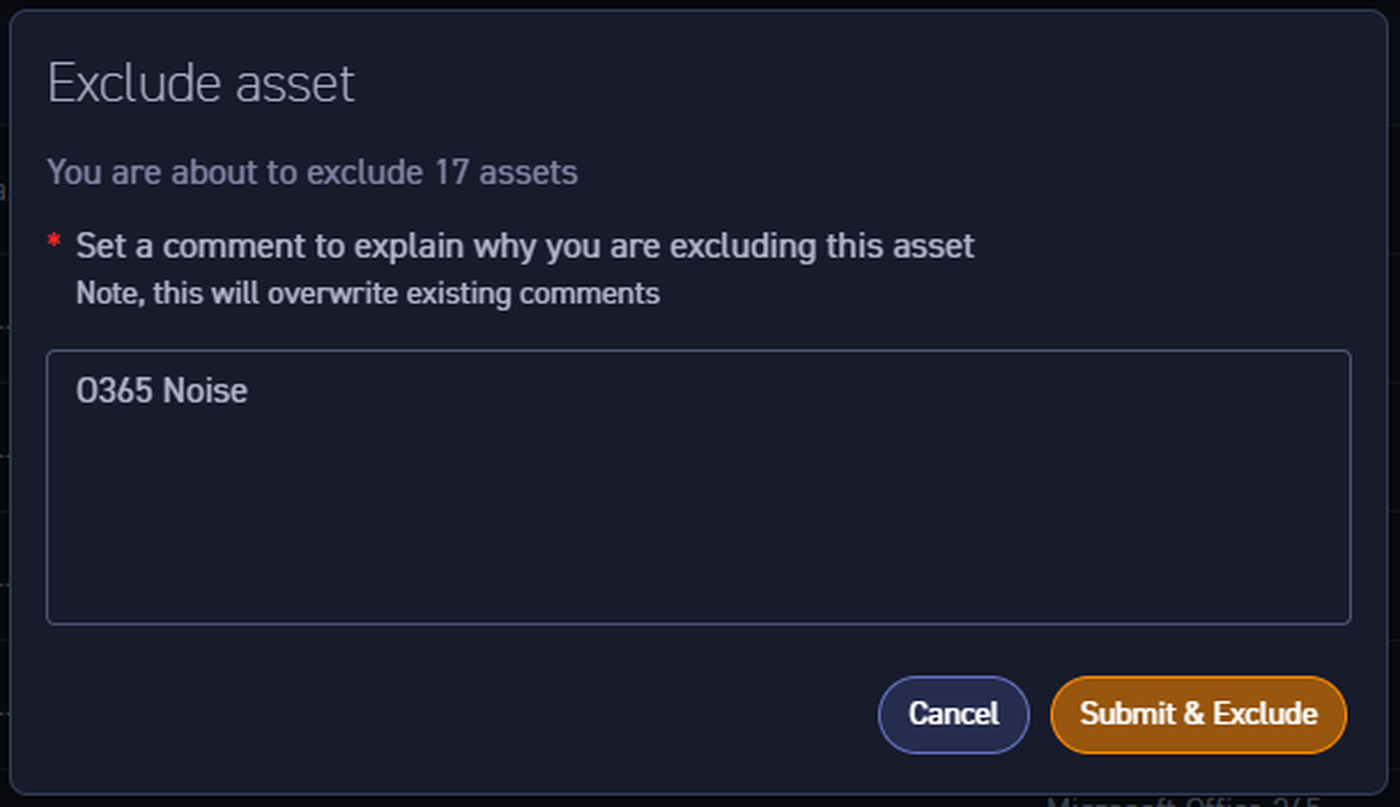
This is exactly how filtering should work in security tools. There’s almost always going to be noise and false positives in security tools, but when it does, it should take seconds to identify it in bulk and remove it from the analysis view. While it makes sense to try to improve scanning and detection engines to reduce that noise, the ability to easily search, filter and exclude results is table stakes.
Usage
CyCognito Platform defaults to the dashboard, which has some useful trending and summary widgets. However, if the default dashboard doesn’t do it for you, eight more dashboard options can be set as the default landing page.
All of CyCognito’s dashboards are dynamic and can be filtered by tag, organization or location. It’s also possible to pivot from specific elements in the dashboard to the detailed findings. Pivoting deeper into the data helpfully opens in a new tab, so your place on the dashboard isn’t lost. In general, CyCognito has one of the most functional interfaces. Large amounts of functionality and detail are baked into the SaaS product, while still supporting a natural, intuitive workflow.
The platform’s key app sections include assets, issues, ‘graph’, reporting and integrations. The assets and issues sections are where most of the work gets done. Both sport their own dashboards, which are also configurable.
Again, it's easy to pivot into the assets given a certain grade, right from the main dashboard (not to be confused with the asset dashboard, which helpfully breaks down asset grades by environments, protocols, technologies and a number of other variables).
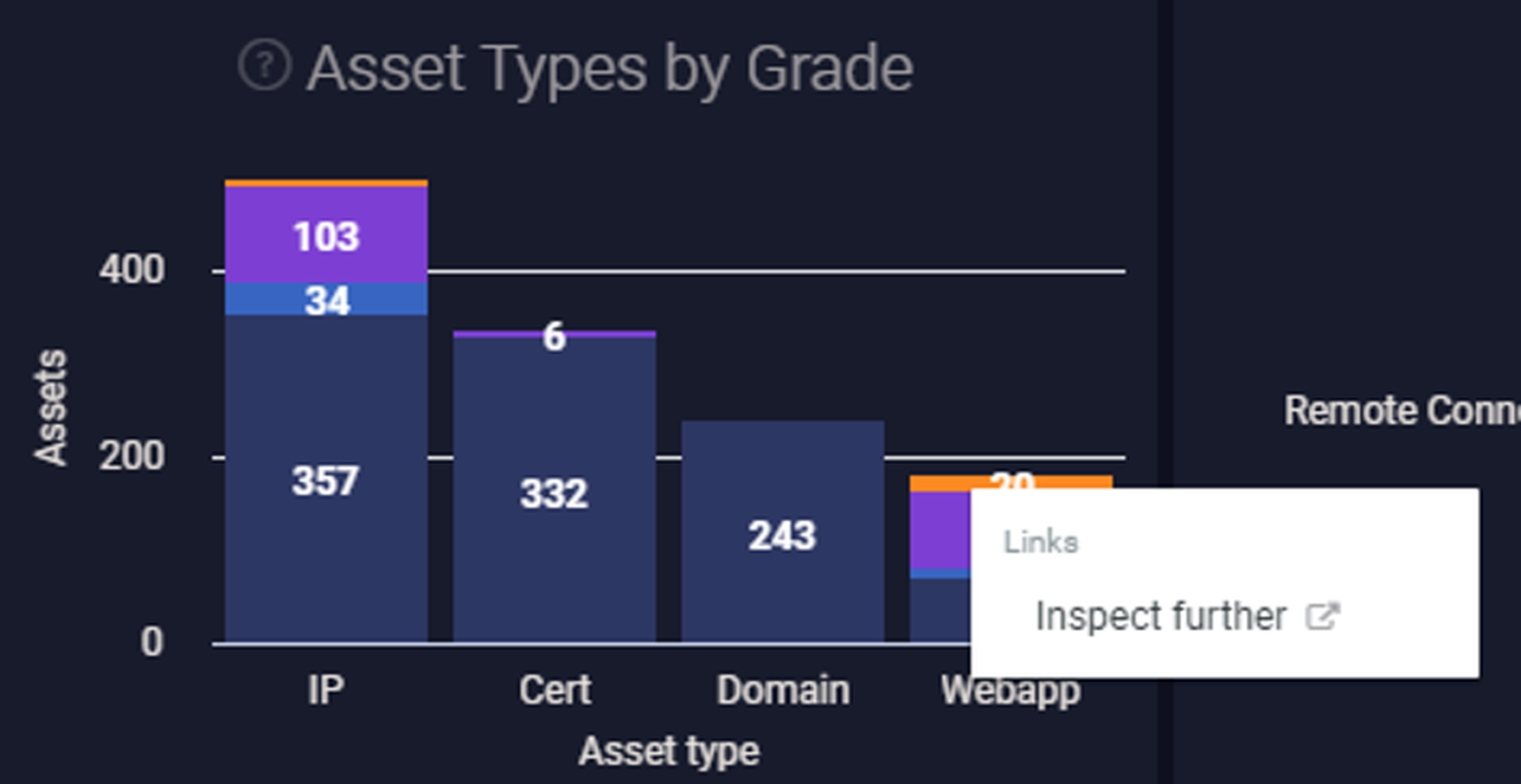
After pivoting, it became clear that most of the "D" grades here are due to another third party we don’t have control over, so I'll exclude those as well. It's worth pointing out that third parties aren't necessarily false positives - most organizations entrust data and even direct access to third parties and want to understand their security posture as well. When doing initial analysis, however, most analysts will likely want to focus on first party issues before they turn their attention to third party concerns.
Another excellent workflow design feature is making it easy to create an alert from any search query. It’s the ideal way to build out notifications in a new product – naturally creating alerts as discoveries are made during the analysis process. There’s no learning curve with a query language – the search bar will automatically create a dropdown that will show you all available options within this stage of the query. Also, no need to build out scripts or learn APIs to enable notifications – just a visual wizard that prompts to complete a few fields and the task is done.
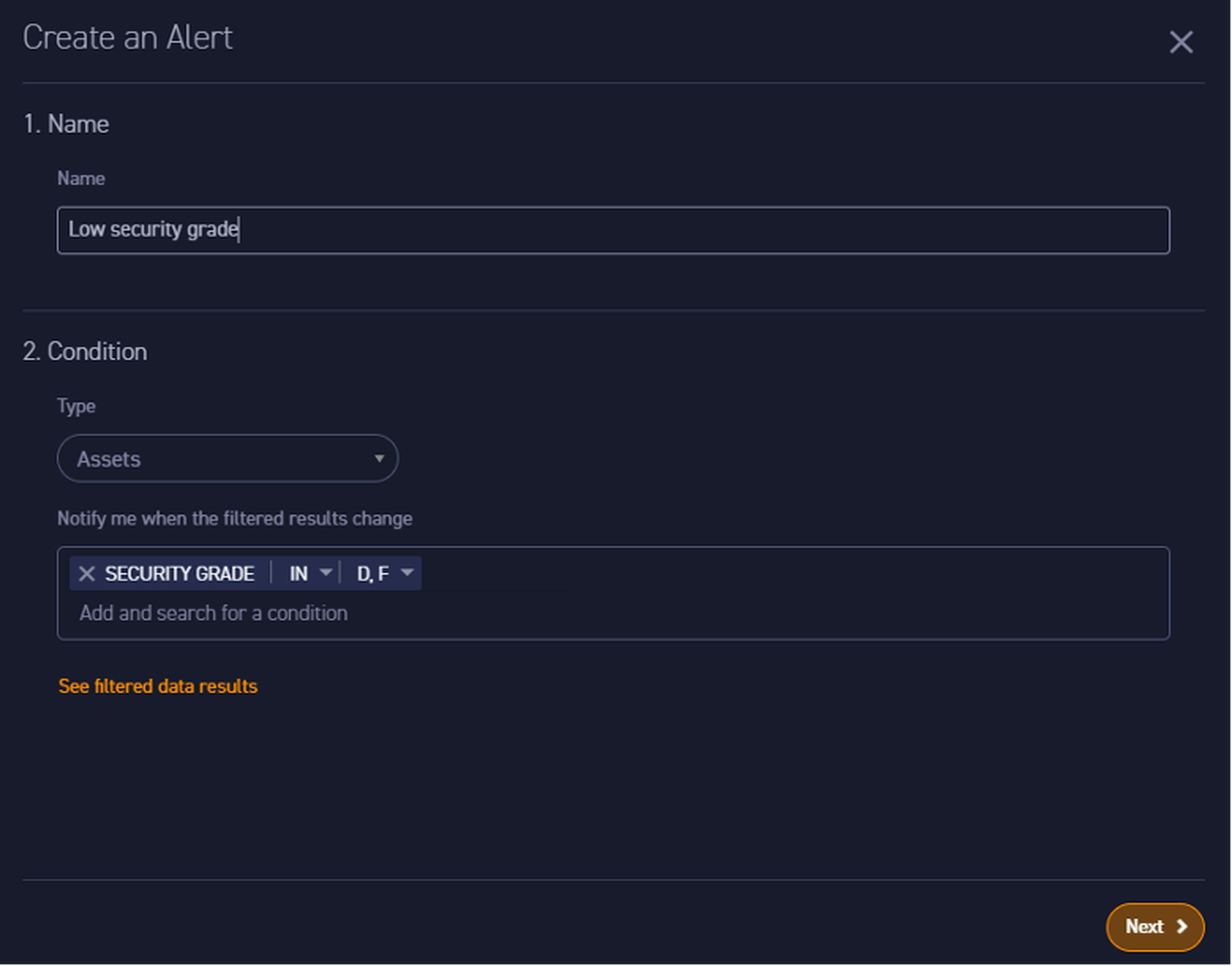
This alert can be delivered to an email address, or to an integrated ticketing system. Current options for self-service integrations include Service Now or Jira. Additional options can be requested right from the integration screen and the company says they also have out-of-the-box support for Slack, GSuite, Zendesk, Splunk, Microsoft Teams and Office365.
Getting into the details
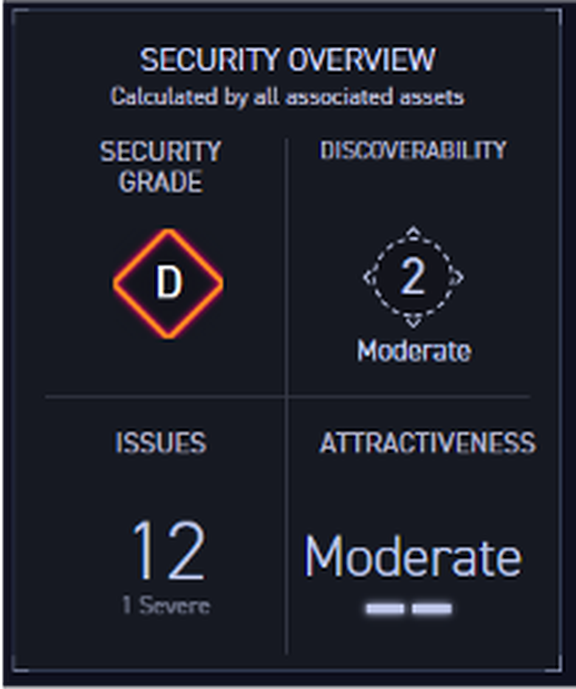
Diving into a specific asset (which happens to be a web application), there’s a wealth of information to consume. Basic asset details, a screenshot (for web assets) and a security overview with a grade, discoverability score, attractiveness score and total number of issues associated with that asset. Comments and tags can be entered and associated with the asset.
Further down the asset page, the discovery path details how this particular asset was discovered. These discovery paths can be fascinating – the path for this particular case goes 5 levels deep:
The asset page goes on to list all 12 of the issues associated with this asset. Finally, the asset page lists the root webpage for this asset, gives another security overview for the application layer components, details about the page and a list of URLs that lead to this particular page.
The detail view for issues is similarly comprehensive and structured. A particularly useful feature on the issue detail page are all the asset details necessary to determine context and attribution. Everything from open ports to ASN (IP ownership) and, of course, the discovery path, are available here without having to open another tab or leave this particular page. Something as simple as reducing the need to open additional tabs when analyzing findings can yield huge improvements to workflow speed and cognitive fatigue for the analyst.
Back to the big picture
There are number of different asset types and views available. They can be grouped by organization, environment, business units or platforms. Raw lists of assets can be viewed by IP address, web application, IP ranges, domain names or certificates. Finally, under assets, it is possible to manage seeds, inclusion lists, exclusion lists and view the rescan log (every asset and issue detail page includes a rescan option – helpful to check whether the fix you just put in place actually fixed the problem).
Viewing issues includes a dashboard view and views that filter by issue status (open, resolved or archived). Issues can additionally be filtered by ‘risk type’. Examples include vulnerable software, abandoned asset, security hygiene and certificate validity, to name a few.
The Graph view is still in beta, but offers some more visual ways of viewing asset and issue data. It starts off with a tree map of all organizations. Selecting a specific organization leads to a hierarchical chart that will be familiar to anyone that has ever seen an org chart or used Maltego. As with other analytical views, this one includes the same filtering and search capabilities, which applies to a graphical view instead of a table view in this case.
Reporting in CyCognito refers to a multitude of different ways to get data out of the platform. It is one of the few ASM products we tested capable of creating an executive summary PDF, suitable for passing up to executive leadership. The executive summary looks clean and strikes a nice middle ground between detail and verbosity. While alerts and exports can be created from nearly any view in the product, summaries of all active alerts and historical exports can be managed under the reporting section of the product.
Performance
For the first ASM group test, we’re not doing any formal performance testing, as there is little feature parity in this fast moving market at this point. Any performance results from this test would likely be invalid in just a few months.
With that disclaimer, we can share some anecdotal insights. In our testing, CyCognito found a significant number of domains and software concerns that other ASM products didn’t catch. While it’s true that nearly every product in this market made unique discoveries over competitors, CyCognito came up with more unique and significant findings than any other.
The techniques used to discover new seeds, which lead to new attack surface, are very important in this market. One clear lesson from past data breaches is that it’s often the assets organizations aren’t aware of that hurt them. Also, the discovery of unknown assets is arguably the flagship use case for the ASM market. The performance of an ASM vendor’s ‘discovery engine’ should be a key purchasing decision for any buyer in this market.
Specifically, CyCognito excelled at discovering outdated infrastructure and application software – from outdated javascript libraries and content management systems to outdated database services and administrative consoles.
Notable integrations
Roadmap
Support
CyCognito offers email and ticket-based support and has a dedicated knowledge base with answers to common questions, user guides, and tutorials.
Claims
CyCognito advertises it gives customers the ability to “Get the Advantage Over Attackers”. We’d buy that – it’s really the primary use case for the entire ASM market – improving visibility to the point where attackers don’t have an advantage due to ‘asset blindness’.
The company’s website also has a number of claims about eliminating the risk from shadow IT and remote workforce risks, which is partially true. While Cycognito can certainly discover some shadow IT risks, it isn’t able to discover shadow IT use of commercial or consumer SaaS (e.g. Evernote, Dropbox), which gets more into a CASB use case, nor does it search for some common shadow IT asset types that other ASM vendors will discover, like personal GitLab or GitHub repositories that contain company-owned code.
That really highlights the state of this market currently – every vendor gets you part of the way there, but no one gets you all the way there and some get you further than others. It’s early days – we anticipate nearly all ASM vendors will add more asset types in the coming months and years.
Security program fit
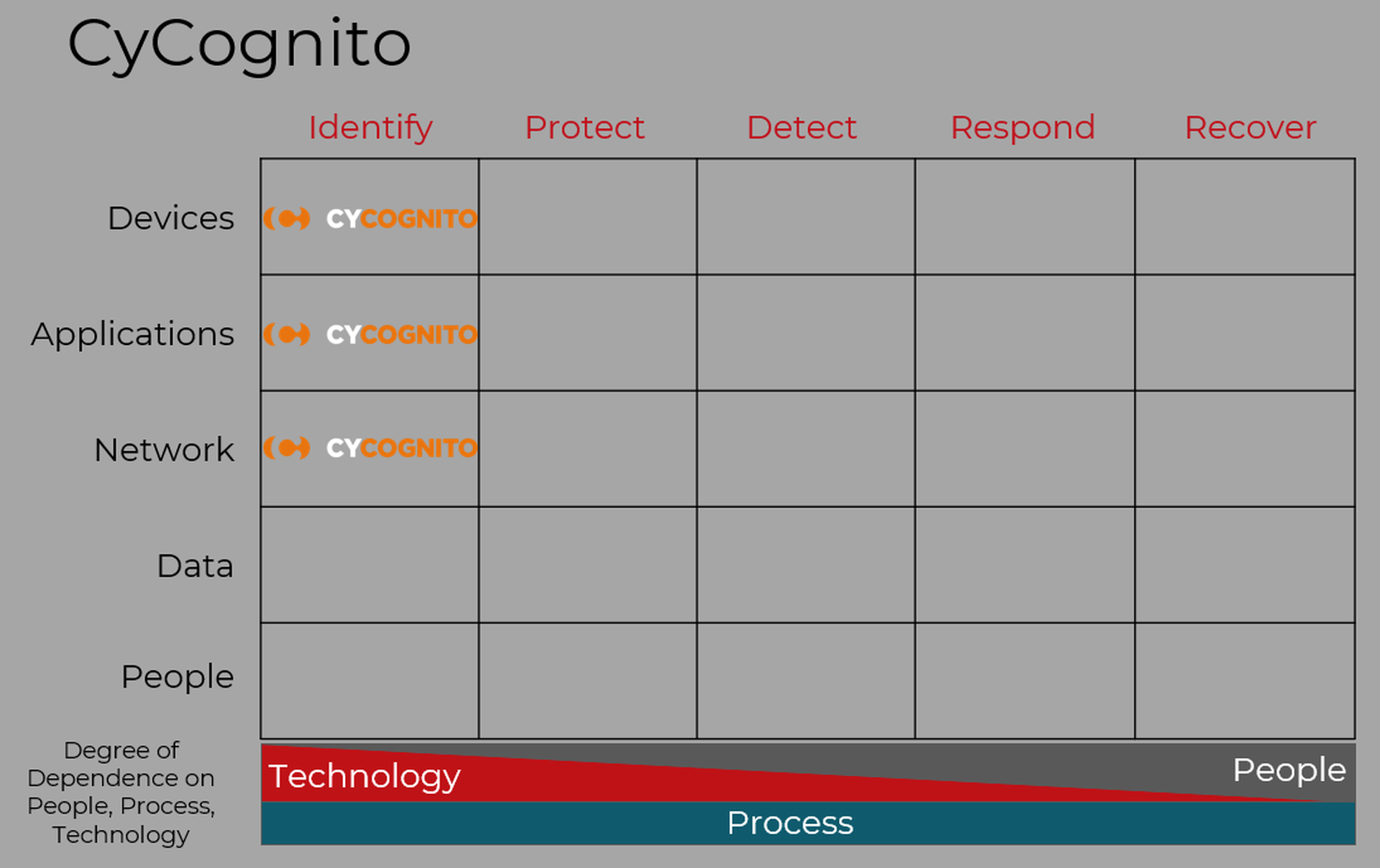
CyCognito Platform, like other products focused on discovering vulnerabilities and misconfigurations, fits solidly within the Identify column of the Cyber Defense Matrix.
Conclusion
CyCognito is one of the most exciting ASM products currently in this market. The combination of solid technology and user experience provides a solid base to grow and compete from. We can’t say enough about what a pleasure the product is to use – the effort put into design and usability is clear. We’d love to see the company grow its validation capabilities in the near future, perhaps adding attack simulations, human testers or both, depending on the path they choose.



