Over the past few years there has been quite a bit of conjecture around the security market and how it will continue to evolve. Security professionals have started to find their own real success against hackers comes from using the same tools and techniques as hackers to turn the tides.

Increasingly, security products are adding in AI/machine learning to strengthen their offerings, so it’s not a stretch to believe that cyberattacks soon will be fought without human interaction as the primary force.
As AI continues to improve and better identify attack patterns, we must continue to place it in the forefront of our defenses as we move to a new frontier of cloud systems. And, with more organizations moving toward the cloud, cloud-based security is becoming more necessity than option.
There are a couple of approaches that can be taken to cloud-based security. The first is taking the functionality of the physical data center and emulating it for the cloud, virtual systems and hybrid organizations. This is a total redesign with the familiar objectives in mind but using AI/machine learning to improve the results.
This approach to cloud-based security takes into consideration what we’ve learned from securing the physical data center and transforms it to shape the new objectives to the evolved security stack.
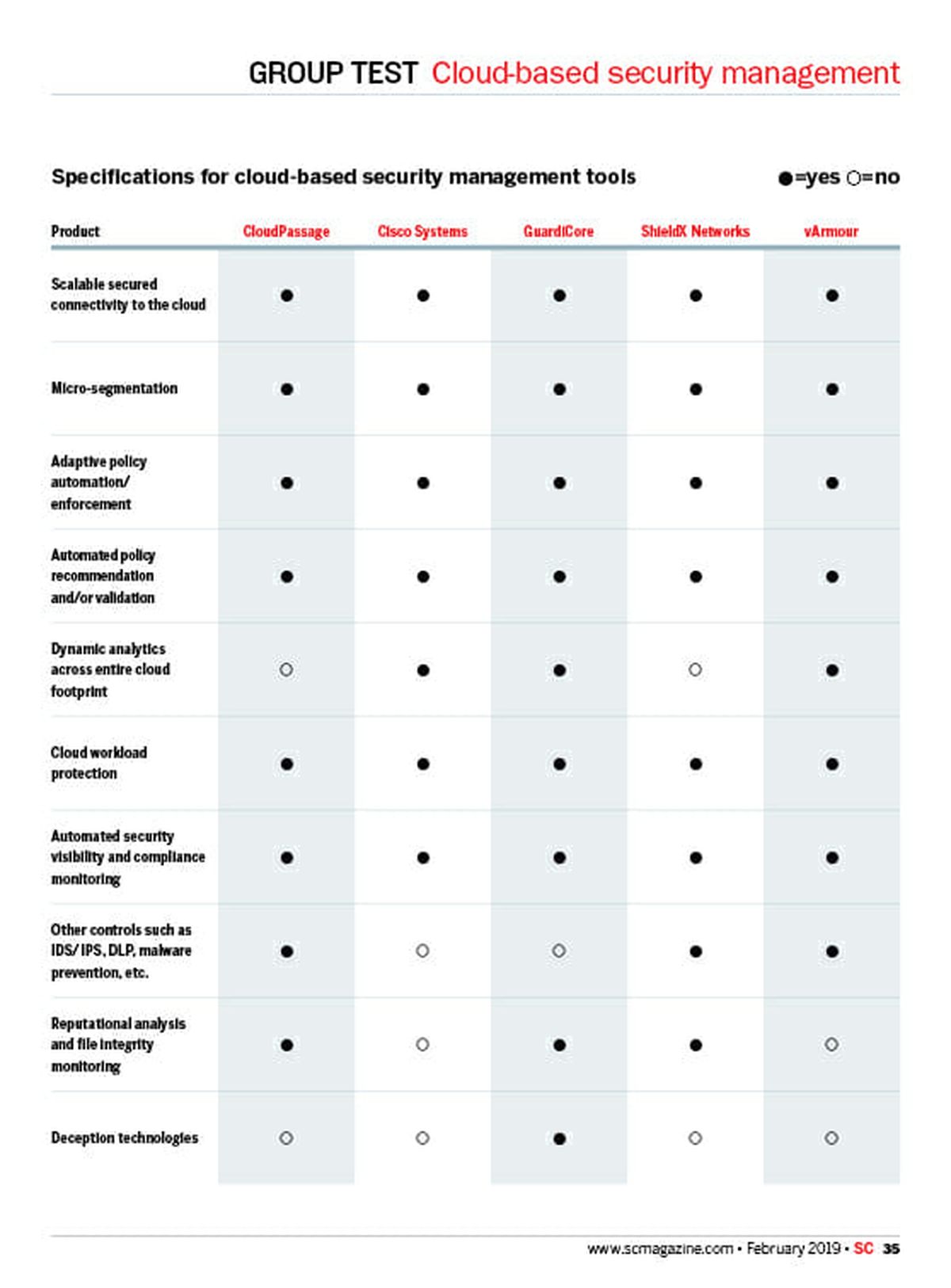
The other popular approach is to have multiple technologies that focus on specific areas of security that work together. As microsegmentation and containerization continue to become popular choices, this approach allows for better security.
Just as important, this approach provides far better performance since it splits up the cloud into smaller pieces of the overall infrastructure – such as individual workloads – rather than by systems which can quickly grow out of control.
As with any successful security infrastructure, there are some vital components in cloud-based security. These components must leverage AI/machine learning to handle large workloads in real time with no disruption to the organizational processes.
This AI must also constantly evolve to understand the normal functioning of the organization and detect the first signs of malicious changes. Finally, this system must be policy-based to streamline the deployment and provide coverage to a variety of system functions.
Next-generation AI requires advanced algorithms, ability to handle big data, rapid – practically real-time – response to change and a few other tasks that are emerging as the marketplace matures. Another is the ability to learn the state of the enterprise and sense malicious changes. Of course, any security system must be policy-based, operationally at least.
That means that whatever is going on under the covers, the results must be based upon policy drivers.
Finally, it cannot be constrained by enterprise architecture. Enterprises today are in the public cloud, private clouds, software-defined data centers, hardware data centers and hybrid architectures.
Looking over the last year’s results, we do not envy our predecessors’ task of looking into the next evolution of security toolsets.
Future security technology simply cannot be benchmarked against the tools we know so well. We haven’t the experience to know what questions to ask or even what particular features are truly unique.
All we can do is understand the challenges and hope the next generation of cybersecurity professionals already are crafting tools to protect the next-generation infrastructure and protect our information.