Security practitioners across industries are taking too long to remediate vulnerabilities and are making snap decisions in response to high-profile threats that don’t always lead to an adequate defense. Those are just some of the takeaways in Immersive Labs’ 2022 Cyber Workforce Benchmark report.
The report is based on data from over 300,000 simulations completed by security teams in 2,100 organizations around the world. Immersive Labs took the data about completed exercises and mapped it against the MITRE ATT&CK framework. Specifically, the report covers:
- How cybersecurity teams develop the knowledge, skills, and judgment to defend against breaking threats,
- Which MITRE ATT&CK capabilities are most highly prioritized;
- How organizations are exercising Incident Response Teams for cyber crises;
- What human capabilities are being developed to ensure secure software; and
- Where the cybersecurity talent of tomorrow is most engaged
Key takeaways:
- Too much time between vulnerability discovery and remediation: The research revealed long lead times between vulnerabilities being reported and organizations developing the skills to defend themselves against them. Immersive measured the time taken by 35,000 people at 400 large organizations to develop the skills, knowledge and judgment to counter 185 cyber threats. Government advice is normally to have defenses in place within days – in Australia, the advice is to be ready in just 48 hours. However, the average from our data was over three months – or 96 days. The report found that critical national infrastructure providers performed the worst, taking an average of 137 days – more than four months – to be ready to counter new threats. The fastest sector to respond was entertainment and leisure with average times of 65.4 days.
- Log4j and the downsides of reactionary thinking: Four of the five fastest-developed skills in 2021 were linked to Log4j. While Log4j was a serious vulnerability with potentially wide-ranging impacts on systems, it was also very high profile. Accordingly, the research captured the innate human impulse to take immediate action when confronted with headlines and flashing red alerts. Unfortunately, this reactionary approach can result in poor decision-making based on assumptions influenced by previous experiences, which may prove irrelevant to a new threat. To counter this, Immersive said business leaders must develop cognitive agility – the ability to ‘think about thinking’ to remove inherent biases and remain open to new views.
- Strong bias to defend against the first steps of an attack: Immersive found that across all sectors, security professionals are much more interested in improving their skills on the left side of the MITRE ATT&CK framework – the early stages of an attack. For example, labs about how to improve skills, knowledge, and judgment to counter how malicious code is run were five times more popular than labs relating to data collection or exfiltration.
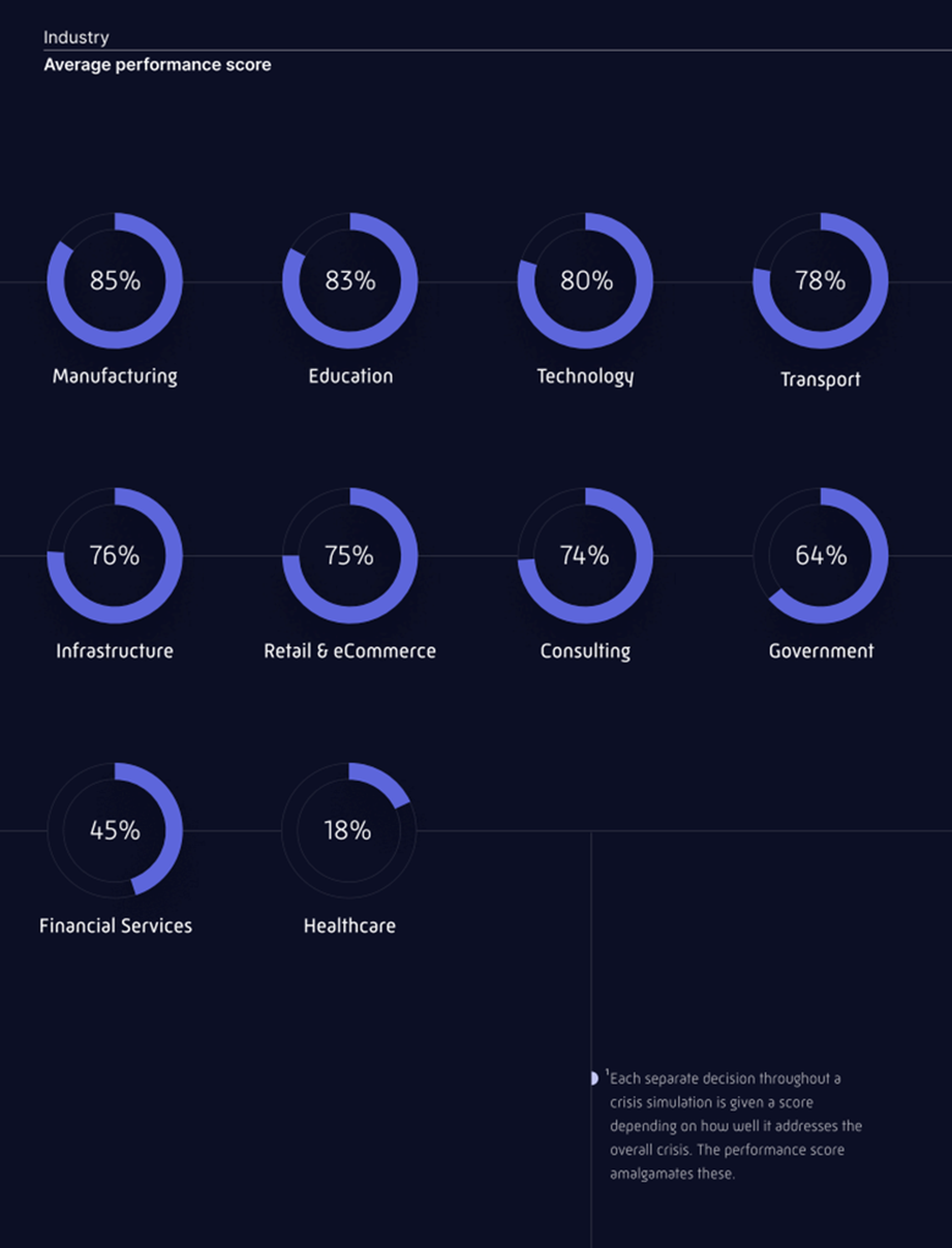
- Healthcare and finance struggling: The average performance score across all exercises analyzed was 68%. The score is an amalgamation of the quality of decisions made throughout the entire simulation and suggests companies across multiple industries have a long way to go. Healthcare is struggling the most, followed by finance and government:
The report also covers the persistent cybersecurity talent gap and difficulties security teams continue to have in dealing with ransomware, and outlines the steps needed to build more resilient security teams.




