In late 2021, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) released the Federal Cybersecurity Incident and Vulnerability Response Playbooks, aimed at providing a standard set of procedures for responding to vulnerabilities and incidents impacting federal civilian executive branch networks.
The playbooks are intended to improve and standardize the approaches used by agencies to identify, remediate, and recover from vulnerabilities and incidents affecting their systems. But the value of the playbooks, developed in accordance with White House Executive Order 14028 for improving the nation’s cybersecurity, is by no means limited to government entities. Any type of organization looking to bolster its efforts in incident response (IR) and vulnerability management can benefit from the guidelines.
Two playbooks
CISA released two sets of playbooks: the Incident Response Playbook, which applies to confirmed malicious cyber activity for which a major incident has been declared or not yet been ruled out; and the Vulnerability Response Playbook, which applies to any vulnerability adversaries are actively using to gain unauthorized entry into computing resources.

“Building on lessons learned from previous incidents and incorporating industry best practices, CISA intends for these two playbooks to strengthen cybersecurity response practices and operational procedures” for the federal government as well as for public and private sector entities, the agency said.
Checklists and roadmaps
The playbooks contain checklists for IR, for IR preparation and for vulnerability response that can be adapted to any organization to track necessary activities to completion. They provide illustrated decision trees and detail each step for both incident and vulnerability response.
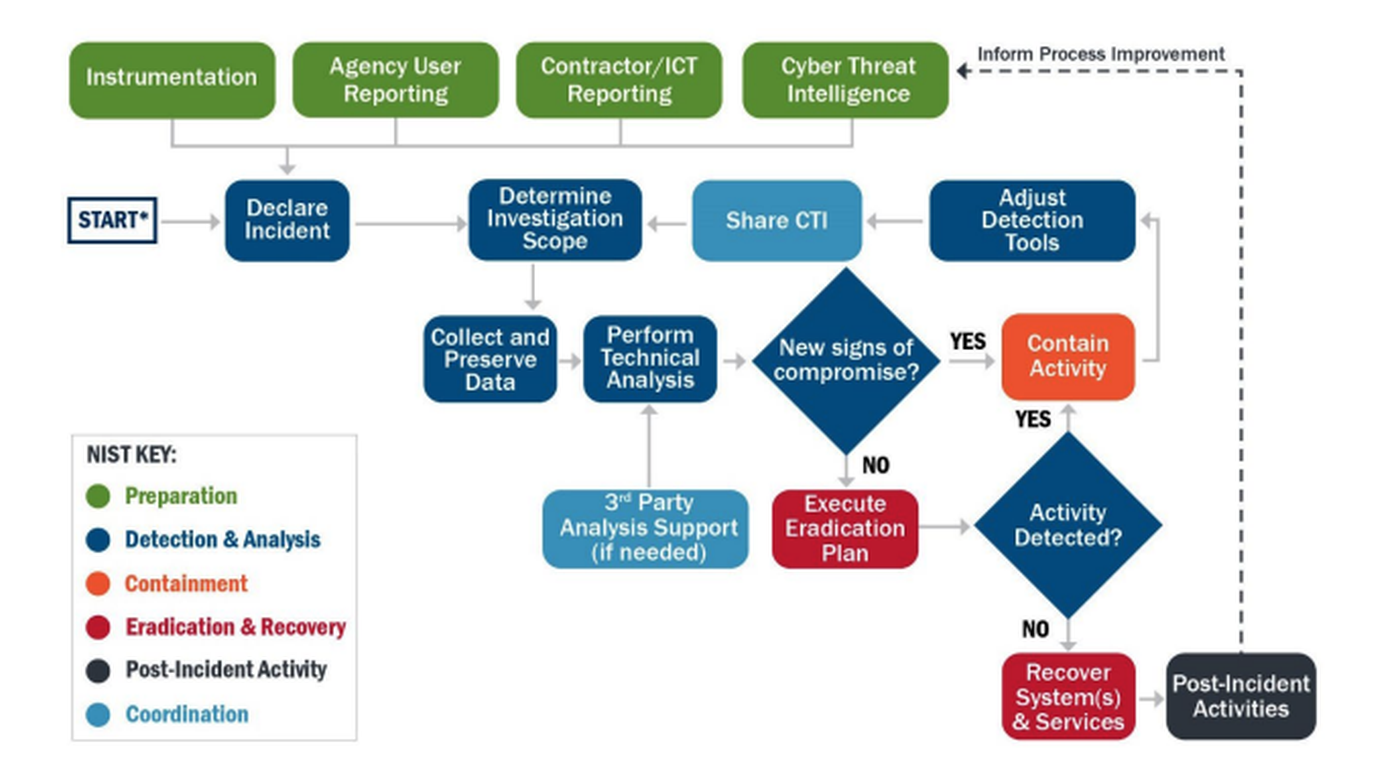
So what's the advantage? The standardized processes and procedures described in the playbooks:
- Facilitate better coordination and effective response among affected organizations
- Enable tracking of cross-organizational successful actions
- Allow for cataloging of incidents to better manage future events
- Guide analysis and discovery
Each playbook can provide a roadmap for organizations looking to strengthen their defenses.
Influenced by NIST
For example, the IR playbook provides a standardized response process for cyber security incidents and describes the process and completion through the IR phases as defined in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-61 Rev. 2, including preparation, detection and analysis, containment, eradication and recovery, and post-incident activities.
IR can be initiated by several types of events, the agency said, including but not limited to automated detection systems or sensor alerts; contractor or third-party service provider reports; internal or external organizational component incident reports or situational awareness updates; third-party reporting of network activity to known compromised infrastructure, detection of malicious code, loss of services; analytics or hunt teams that identify potentially malicious or otherwise unauthorized activity; or IR process.
CISA said organizations should use this playbook for incidents involving lateral movement, credential access, exfiltration of data; network intrusions involving more than one user or system; and compromised administrator accounts.
Preparing for major incidents
The IR playbook also includes instructions on how organizations can prepare for major incidents before they occur and mitigate any impact on the organization. Preparation activities include:
- Documenting and understanding policies and procedures for incident response
- Instrumenting the environment to detect suspicious and malicious activity
- Establishing staffing plans
- Educating users on cyber threats and notification procedures
- Leveraging cyber threat intelligence to proactively identify potential malicious activity
The playbook recommends that organizations define baseline systems and networks before an incident occurs to understand the basics of “normal” activity. Establishing baselines enables security teams to identify deviations. Preparation also includes having an infrastructure in place to handle complex incidents, including classified and out-of-band communications; developing and testing courses of action for containment and eradication; and establishing means for collecting digital forensics and other data or evidence.
“The goal of these items is to ensure resilient architectures and systems to maintain critical operations in a compromised state,” the IR playbook said. “Active defense measures that employ methods such as redirection and monitoring of adversary activities may also play a role in developing a robust incident response."




