Global spending on cloud security products continues to surge year after year, as organizations see the value of moving business-critical systems and data to the cloud. However, the rush to be ‘cloud-first’ has saddled many organizations with a disconnected hodgepodge of cloud security tools that produce almost as many problems as they solve – including a splintered view of the attack surface, excessive maintenance and administrative overhead, and information silos that undermine effective DevSecOps practices.
That’s where cloud-native app protection platforms come in.
What are cloud-native app protection platforms?
A cloud-native app protection platform, or CNAPP, brings together a varied set of tools into one convenient location. More specifically, it combines a full proprietary suite of cloud security tools into one software solution, making them accessible through a single user interface and shared source of truth.
By doing so, a CNAPP largely eliminates the hassle involved in drawing insights manually from an army of disparate point-solution products.
Who is a CNAPP for?
More organizations are going beyond ‘lift-and-shift’ and adopting a cloud-native approach that focuses on building applications from within the cloud to harness untapped speed and scalability. A CNAPP provides an ideal toolkit for organizations looking to scale up use of cloud-native technologies (such as containers, microservices, declarative APIs, and immutable infrastructure). A CNAPP also makes sense for organizations who are seeking to automate security testing and reduce manual efforts in reporting vulnerabilities or misconfigurations.
The risks of neglecting cloud native app protection
Organizations may put themselves at considerable risk if they dismiss cloud-native app protection. There are many variables in cloud security to consider:
#1: Low visibility = low awareness
Lacking a unified platform, security risk managers must divide their attention among a growing library of point solution products, resulting in information silos and blind spots that offer easy prey for attackers. And recent studies back that up: 37% percent of respondents in a 2022 survey by CyberRisk Alliance said their organization had experienced a cloud-based attack or breach within the last two years.
#2: Product overload
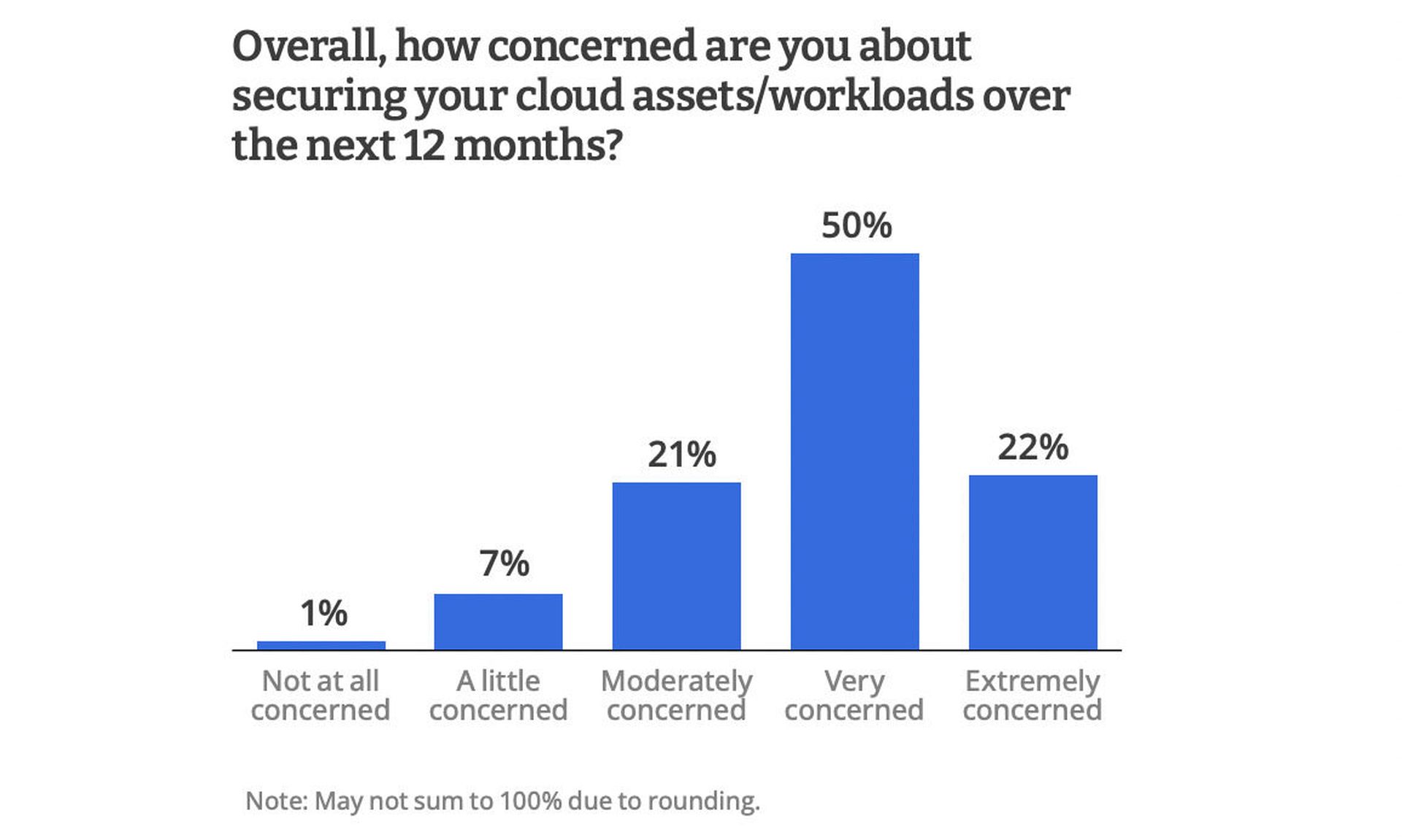
Organizations face pressure to secure a rapidly growing inventory of cloud assets. The CRA survey found that 55% of respondents were running up to 50 assets and workloads or more in public cloud environments, and 72% of respondents were ‘very’ or ‘extremely’ concerned in the ability of existing security tools to protect these assets in the next 12 months.
#3: Infrastructure misconfigurations
Organizations that move to the cloud will find that traditional configs and change controls used for on-prem data centers are static and ill-suited for the dynamic change expected of the cloud. Attackers are prowling for faulty configurations, like exposed cloud networking paths or publicly facing databases, to target their exploits. Based on trending data, Gartner predicted that 50% of organizations would have infrastructure as a service (IaaS) storage, network segments, applications or APIs directly exposed to the public internet in 2021 as a result of misconfigurations alone.
#4: False positives and errors
Piecemeal security solutions are a breeding ground for false positives. Dev teams lacking unified, consistent visibility of the network may find themselves waylaid by false positives and low-risk vulnerabilities, diverting their attention and efforts away from solving higher-magnitude problems.
#5: Delayed or reactive remediation
Effective cloud-native app protection takes advantage of automation to give developers proactive security scanning capabilities that facilitate continuous integration and development. Absent these tools, devs are more likely to find themselves on the defensive, putting out fires that could have been prevented earlier in the pipeline.
CNAPP: Key features and benefits
Why should organizations consider implementing a cloud-native app protection platform? Here are just a few of the key solutions and features that a CNAPP packages together for easy access:
- Cloud workload protection program (CWPP): Helps defend a wide range of cloud infrastructure workloads from attack, including Virtual Machines, APIs, serverless functions, containers and Kubernetes apps. A good CWPP will also suggest remediation paths to correct vulnerabilities and maintain smooth production.
- Cloud security posture management (CSPM): Typically used for public clouds, CSPMs help organizations discover and automatically remediate threats, misconfigurations, misuse and compliance violations in public clouds. They ensure that cloud activities adhere to regulations and mandates, and alert security teams to non-compliant resources so they can be addressed. However, many CSPMs are largely reactive since they only detect misconfigurations after the resource is deployed, not before.
- Infrastructure-as-Code scanning (IaC): To address misconfigurations before they reach deployment, more and more security leaders are turning to infrastructure-as-code, which ditches manual maintenance of cloud infrastructure in favor of code automation. Qualys, for example, has built a security automation solution for IaC that can read Terraform, CF, and ARM files and flag misconfigurations identified in resources using AWS, Azure, and GCP. It’s also versatile: IaC assessment can scan throughout the pipeline – on the source code when it enters the repository, during the integration phase, and before deployment. This enables DevOps teams to receive immediate feedback and apply proactive fixes much earlier.
- Cloud infrastructure entitlement management (CIEM): Managing permissions and rights across the cloud can be difficult, especially in multi-cloud arrangements. CIEM is another core provision of CNAPP that can help enforce Zero Trust policies and the principle of least privilege, in that it helps identify and remove unnecessary access, permissions or privileges that exceed desired boundaries. Oftentimes, such access is granted by default or by accident. CIEMs are useful for flagging these instances so that no one is granted more access than their role requires.
The bottom line
Each of these features contributes to better cloud security, but deploying them separately under manual methods can create unnecessary complexity and frustration for DevOps teams. A CNAPP is the recommended tool for bringing these disparate solutions under one roof, ensuring that developers have full visibility of their cloud infrastructure, a single dashboard source of truth, proactive remediation mechanisms, and access to analytical insights that would otherwise get lost in the noise.




