Many organizations would like to move to converged cloud-security solutions such as secure access service edge (SASE) and security service edge (SSE). Yet according to a recent survey, the adoption rate is low, and the concepts remain unclear to many.
CyberRisk Alliance (CRA) interviewed 300 information-technology professionals about converged cloud security in the fall of 2022. Of the respondents, 77% considered it to be "very important" or "extremely important."
"As large of a company as we are, it is embarrassing that we do not have [a converged network-security solution]," said one respondent from the health-care sector. "Regulators will kill us, I think, if we do not achieve this soon."
There is a recognized need for converged cloud security, but only 10% of survey respondents said their organizations had implemented SASE or SSE. Nearly half (46%) admitted they didn't completely understand what the terms meant.
What exactly are SASE and SSE? How do they differ, and how might they benefit you? Here's what you need to know.
SASE: More than the sum of its parts
SASE is something Gartner analysts came up with in a 2019 white paper titled "The Future of Network Security Is in the Cloud" (paywalled). An acronym-heavy Gartner blog post explained the concept thus:
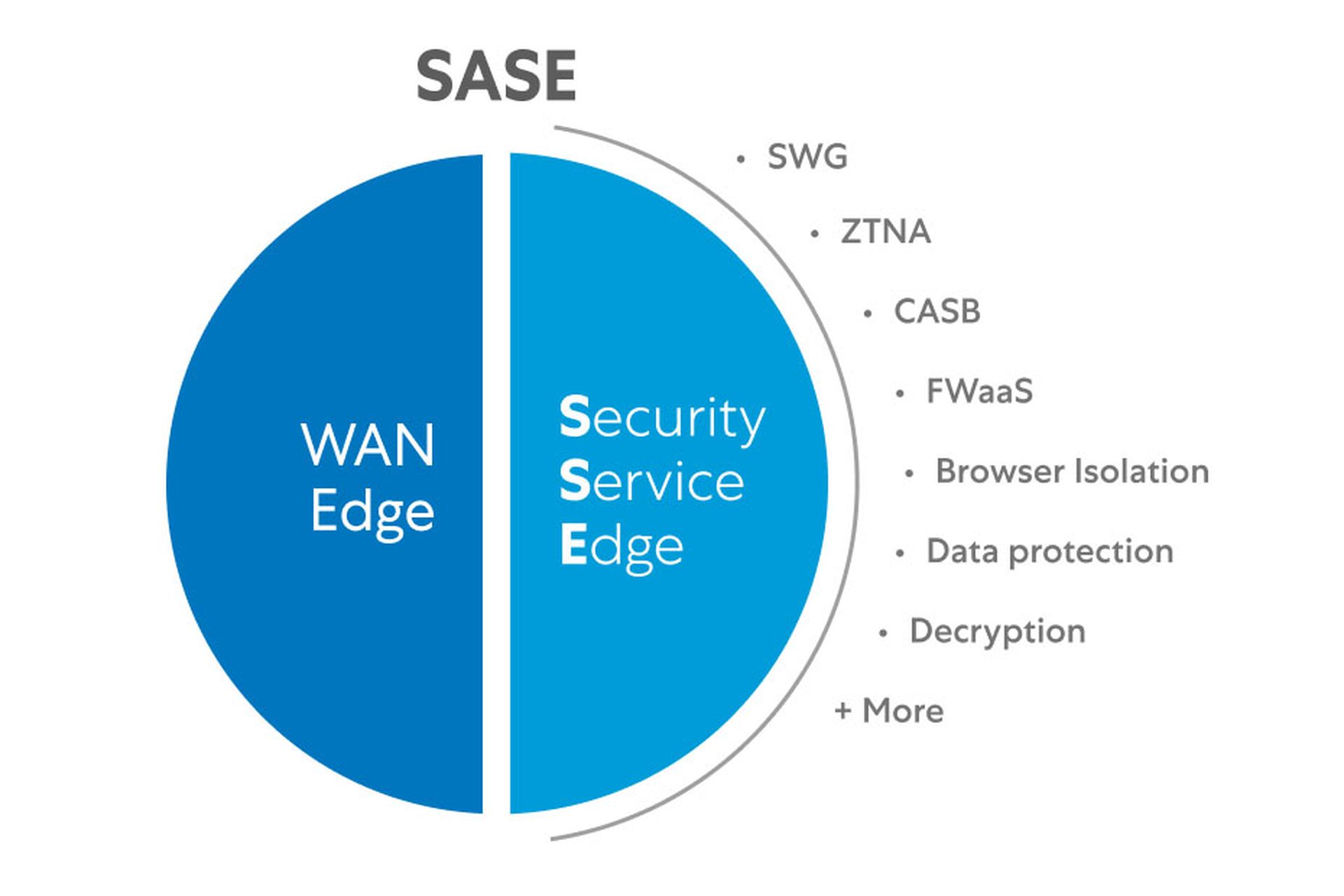
"SASE combines network security functions (such as SWG [secure web gateway], CASB [cloud access security broker], FWaaS [firewall as a service] and ZTNA [zero trust network access]), with WAN capabilities (i.e., SD-WAN [software defined wide area network]) to support the dynamic secure access needs of organizations. These capabilities are delivered primarily aaS [as a service] and [are] based upon the identity of the entity, real-time context and security/compliance policies."
In plain English, SASE uses a software-based virtual network to create regionally distributed points of presence (PoPs) that provide nearby secure networking and cloud-based security functions to branch offices and remote users. SASE brings security and networking geographically closer to users, cuts down lag and latency, eliminates the need for a company VPN, abolishes the obsolete perimeter model and lets organizations shift from on-premises to cloud-based security solutions.
"What makes SASE stand out from point solutions and other secure networking strategies is that it's both secure and direct," explained Zscaler in a glossary listing. "Rather than relying on your data center security, traffic from your users' devices is inspected at a nearby point of presence (the enforcement point) and sent to its destination from there. This means more efficient access to applications and data, making it the far better option for protecting distributed workforces and data in the cloud."
SASE has five essential components:
- A cloud access security broker (CASB) to monitor and control traffic between an organization's users and its cloud instances and web applications. A CASB may incorporate aspects of identity and access monitoring (IAM), endpoint detection and response (EDR) and data loss prevention (DLP).
- A cloud-based firewall-as-a-service (FWaaS) to filter network traffic according to the organization's rules, often using next-generation firewall (NGFW) functions such as intrusion prevention/detection (IPS/IDS) or domain-name-system (DNS) security.
- A software-defined wide-area network (SD-WAN) that can securely link branch offices, data centers and remote users. The SD-WAN may overlay the public internet, may use a private backbone to link to PoPs, or may do both.
- A secure web gateway (SWG) to monitor, inspect and log users' web traffic and block malware and intrusions. It can also filter content and block specific URLs according to organizational policy and may include browser sandboxing.
- Zero-trust network access (ZTNA), which verifies and authenticates each user upon access, even if the user is on-premises. Lateral movement can be restricted by additional authorization requirements.
Combining these different cloud-based solutions makes it easier to manage an organization's overall security and lowers costs as legacy hardware is phased out and subscriptions are consolidated.
"The whole converged solution concept is about reducing complexity," said Boaz Avigad, senior director of product marketing at Perimeter 81. "You want something that is simple and easy to use and can be managed from a single pane of glass. You want a single agent running on the edge devices to deliver all of the services."
However, SASE is still more of a framework than an actual product. Few vendors can offer a comprehensive SASE package. In most cases, an organization will need to piece together a SASE solution from various parts, often over a period of months or even years before it can achieve full implementation. "You have vendors that have almost everything, and vendors that have less, but you have no single vendor that offers all of what Gartner defines as part of SASE," said Avigad.
SSE: For organizations that don't need the full SASE
In 2021, Gartner noticed that many organizations weren't adopting the entire SASE model, but instead implementing only its security aspects. So Gartner came up with a new concept: security service edge, or SSE.
"Security service edge (SSE) secures access to the web, cloud services and private applications," reads the Gartner definition. "Capabilities include access control, threat protection, data security, security monitoring, and acceptable-use control enforced by network-based and API-based integration."
SSE is a subset of SASE, eliminating the SD-WAN but retaining the CASB, FWaaS, SWG and ZTNA functions. It also retains PoPs, which can be connected over the internet using ZTNA policies rather than via an SD-WAN.
"Some companies don't need SASE," said Perimeter 81's Avigad. "If you are a cloud-borne company, you have no use for SD-WAN. [SASE is] for companies that have both branch offices and people working from home."
SSE, which Avigad calls "hardware-less by definition," may also be better for organizations that choose to retain their existing networking infrastructure. Furthermore, adopting SSE instead of SASE means that networking and security teams don't have to combine duties, a practical consideration that organizations may struggle with.
"While I had to work with a networking team when I was a CISO, I never had responsibility for networking," said Frank Kim, CISO-in-residence YL Ventures and a SANS Institute fellow. "SSE makes a lot more sense for a CISO because it just focuses on security."
Is SASE or SSE better for your organization?
The choice between SASE and SSE is best made after a thorough assessment of your organization's abilities, needs and goals. As mentioned above, a fully remote company can likely opt for SSE over SASE because it can replace SD-WAN with ZTNA over the internet.
For much more along these lines, please read our guides:
How to determine if your IT environment is ready for SASE
Buying SASE: Questions to ask vendors before you commit
How to determine SASE needs specific to your IT environment
It may even be advantageous to wait until the converged-cloud-security industry consolidates itself and more vendors are able to offer full-package SASE or SSE solutions.
"My organization is most likely to consider purchasing an [SSE] solution that is a one-platform, comprehensive network security solution," said one respondent in the CRA survey. "This approach is more efficient and cost-effective than purchasing individual solutions for each aspect of network security."




