Secure access service edge, or SASE for short, is a modern model of secure networking that discards the older perimeter- and data-center-based models and applies cloud- and software-based principles to move the security "center" closer to the edge user, no matter where that user may be. With a SASE (pronounced "sassy") framework, your organization can reach and protect authorized users in any location and on any platform.
The origins and advantages of SASE
The term SASE, and the concept, were coined by Gartner analysts in a 2019 white paper titled "The Future of Network Security Is in the Cloud". In an accompanying blog post, Gartner's Andrew Lerner explained SASE thus:
"SASE combines network security functions (such as SWG [secure web gateway], CASB [cloud access security broker], FWaaS [firewall as a service] and ZTNA [zero trust network access]), with WAN capabilities (i.e., SDWAN [software-defined wide area network]) to support the dynamic secure access needs of organizations. These capabilities are delivered primarily aaS [as a service] and based upon the identity of the entity, real-time context and security/compliance policies."
That's a lot of acronyms, but it all means that SASE uses software virtualization to deliver relatively local secure networking to geographically scattered users. These users no longer need to tunnel their network traffic to a remote data center via a VPN, then back out to the internet from the data center. Instead, they can use SASE to securely connect to regionally dispersed points of presence (POPs) without the need to "hairpin" traffic through a far-off physical data center.
"Rather than relying on your data center security, traffic from your users' devices is inspected at a nearby point of presence (the enforcement point) and sent to its destination from there," said Zscaler in an explanatory blog post. "This means more efficient access to applications and data, making it the far better option for protecting distributed workforces and data in the cloud."
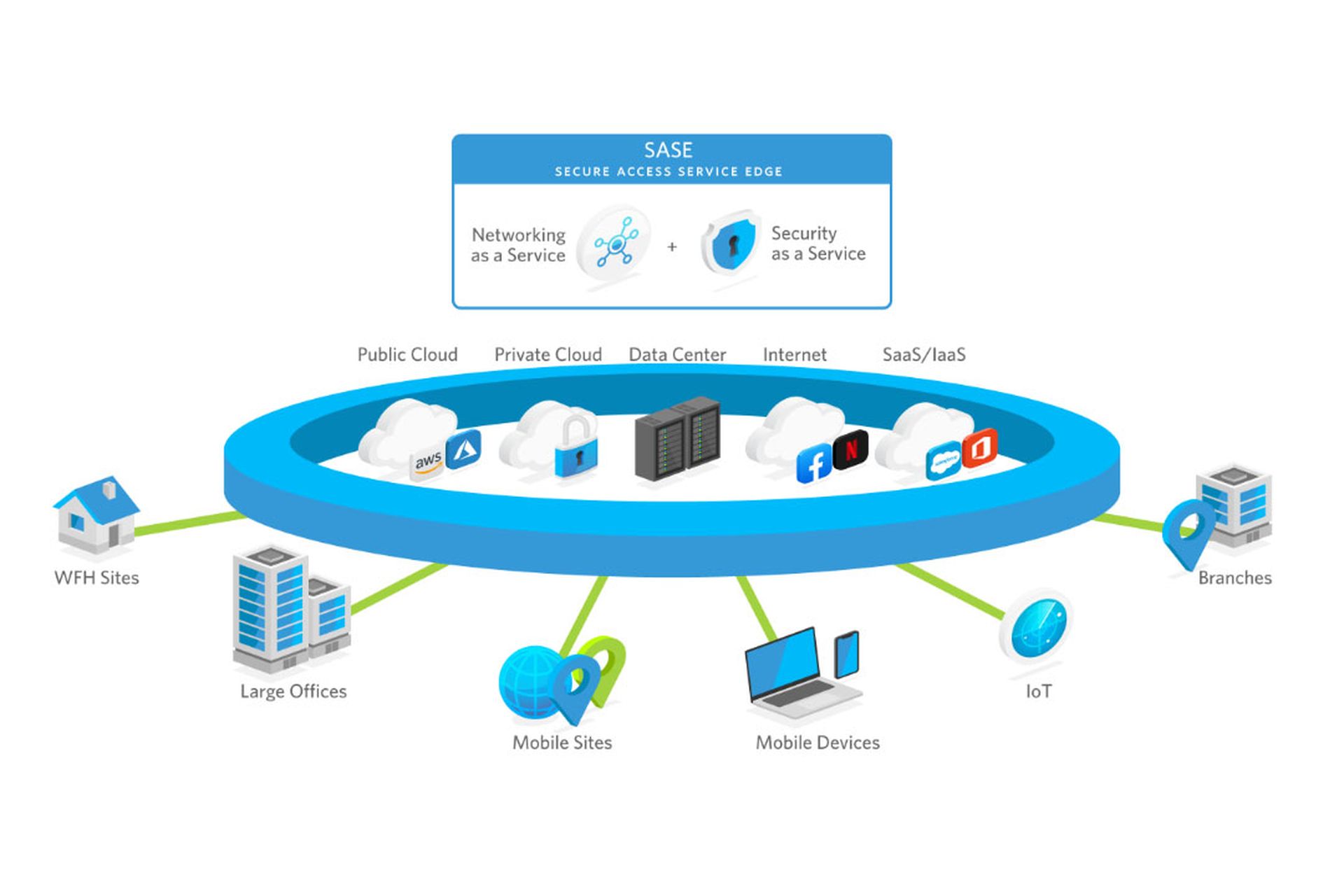
This new model is necessary because with the spread of remote work — a phenomenon accelerated by the COVID-19 pandemic that quickly followed the release of the Gartner white paper — many organizational staffers are rarely, if ever, on-premises. It doesn't make sense for staffers to need on-prem data centers and security hardware to securely get online.
"The traditional network security perimeter has vanished," explained Infoblox. With SASE, "the burden of managing and securing a network moves from labor-intensive, server-based appliances in the data center to virtual and containerized applications in the cloud."
The abandonment of the perimeter model means a shift to identity-driven access and authorization, as exemplified by the zero-trust network-access model, but it also means that an organization's virtual WAN and security systems will gain the flexibility and responsiveness of the cloud.
"SASE empowers organizations to see, secure and connect users from one place," states an explanatory video clip produced by Cisco. "This makes it easy to verify users and devices, so users can work from anywhere and always have access to their must-have resources. SASE can even simplify identifying, investigating and resolving security or connection issues. Plus, with cloud-based networking and security, scaling up or down is easy and much more affordable."
The components of SASE
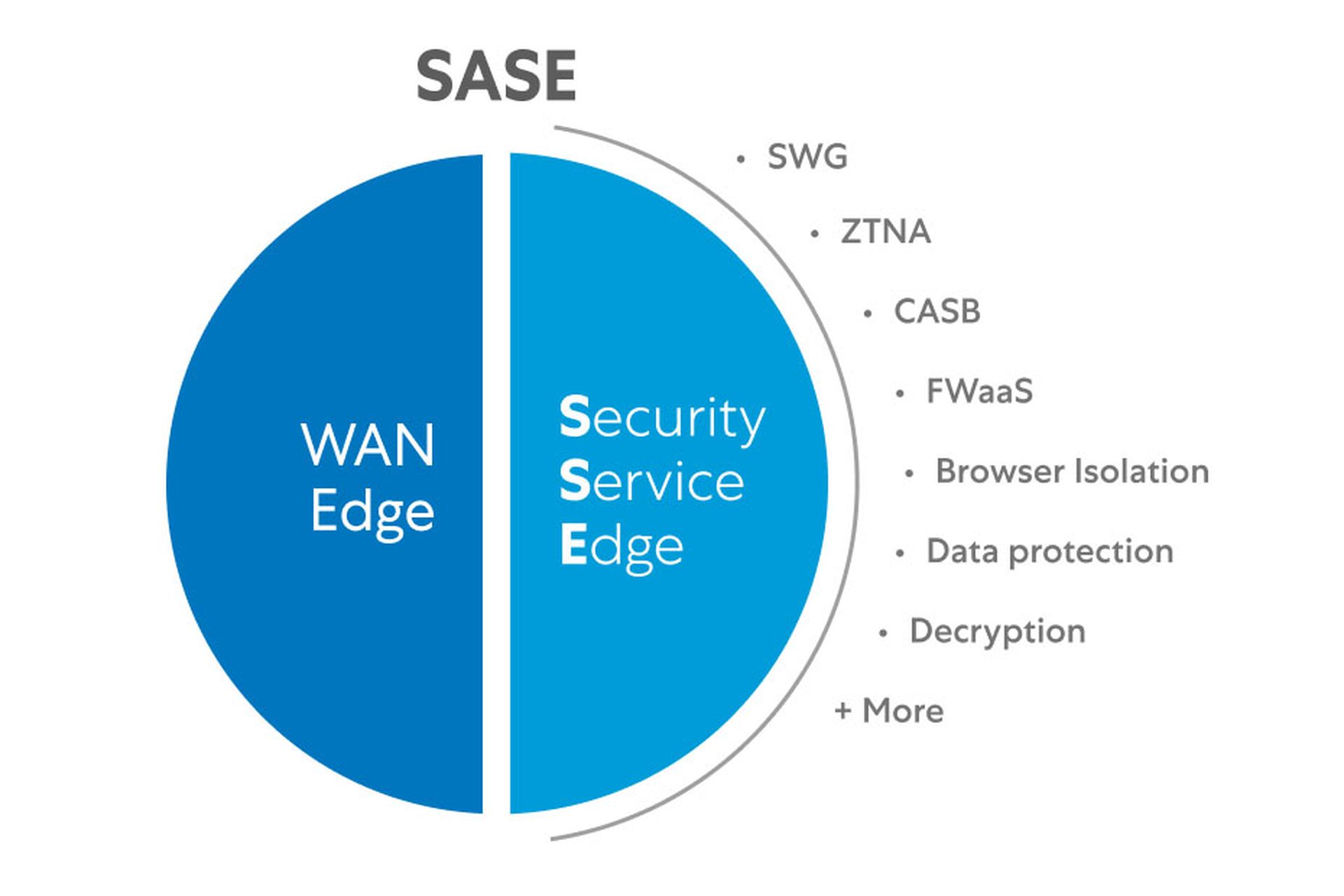
As explained by Gartner, SASE is not a silver-bullet single solution, but a framework made of up of distinct parts working together. These parts generally include:
- A software-defined wide-area network (SD-WAN), an overlay to securely tie together the far-flung branch offices, data centers and work-from-home users of a geographically dispersed enterprise
- A cloud-access security broker (CASB) to monitor and control traffic between an organization's users and its cloud instances and applications, and may also control user access
- A secure web gateway (SWG) to monitor, inspect and log each user's inbound web traffic and block malware and intrusions
- Zero-trust network access (ZTNA), a framework that verifies users and devices, no matter where they are physically, and treats every access request individually
- A firewall-as-a-service (FWaaS), cloud-based software that blocks network traffic according to the organization's rules and may include DNS security and an IPS/IDS system (see below)
SASE also may include as stand-alone functions:
- A data-loss-prevention (DLP) system to block exfiltration of data
- Domain-name-system-layer (DNS-layer) security to block connections to malicious or unwanted servers
- An intrusion-prevention or intrusion-detection system (IPS/IDS) to block network intrusions
All these features except the SD-WAN are sometimes collected together in the related concept of security service edge (SSE), which groups all the security-first aspects of SASE. Ideally, a working SASE system would control all these various aspects from a single console.
Sprechen Sie SASE?
Gartner's white paper considered SASE to be a work in progress, with no vendors offering all-encompassing SASE solutions when the paper was written in late 2019. However, the company projected that 40% of enterprises would be using some form of the SASE model by 2024.
As of today, many familiar names, including Cisco, Netskope, Palo Alto Networks, VMware and Zscaler are touting umbrella SASE packages incorporating some or all of the features listed above.
Whether or not your organization should adopt SASE depends on the structure of your workforce. Does everyone come to work in the same building, or do many of your staffers work from home part or all of the time? If it's the latter, you may want to consider SASE, as it delivers the same benefits of cost, flexibility and scalability as other cloud services.
But even in 2019, Gartner's Andrew Lerner had some buying advice for SASE shoppers.
"Software architecture and implementation really matters," he wrote. "Be wary of vendors that propose to deliver services by linking a large number of features via VM service chaining, especially when the products come from a number of acquisitions or partnerships."
Lerner added, "We recommend short-term SASE contracts of one to two years maximum, as licensing models are in flux."




