Email was never meant to be secure, which is why it's so often used to attack organizations. From phishing to ransomware to business email compromise (BEC) attacks, the lack of native authentication for email messages causes billions of dollars in losses to criminals every year.
Fortunately, there are a few tried-and-true methods for beefing up your organization's email. Here are the best ways to secure your email.
The trouble with email
Email doesn't provide verifiable proof of a message sender's identity. It’s easy to "spoof" an email message so that it seems like it's coming from the White House instead of some kid down the block.
Sender spoofing is at the heart of many email-based attacks. A phishing email may spoof your bank's domain name to get you to visit a fake login page. A ransomware attack might begin with a booby-trapped invoice that seems to come from a longtime supplier. BEC attacks often involve emails "from" company CEOs or CFOs ordering money transfers to unfamiliar bank accounts.
"While we do run training sessions and communicate about fraudulent emails, people still click on things they shouldn't, open up emails or attachments when they shouldn't," an information-security manager told SC Media. "If they don't get a big red warning from the security systems, they just don't think about every email they touch."
Email spoofing is not the same as email spam, and spam filters may not stop spoofed messages. And not all malicious emails require spoofing — we've all seen phishing emails that seem to come from well-known companies but have sender addresses like "[email protected]."
But sender spoofing makes email-based attacks less obvious and more effective. A phishing email really might seem to come from your bank, and an immediate payment order may genuinely appear to come from your boss.
Those last scenarios, BEC attacks, are especially commonplace and harmful. A 2022 survey of CISOs and other information-security managers by CyberRisk Alliance, detailed in a recent white paper, found that half the respondents saw up to 25 BEC attacks every day, and 78% rated protection against BEC attacks to be very important.
The FBI cited $2,395,953,296 in BEC losses in 2021, a 26% jump over 2019's losses and by far the costliest category of online crime. By comparison, ransomware resulted in $49,207,908 in reported losses despite its much higher public profile.
"A couple months ago our accounting [department] got a strange email saying our sales VP authorized this payment invoice when it was an email just pretending to be from our sales VP and sent to our accounting," a CISO of a large manufacturing company recently told SC Media. "Our accounting people almost made a payment."
Spoofing also makes all email messages inherently suspicious. Your messages will be treated as guilty until proven innocent. The email authentication methods described below are now so commonplace that if your organization does not implement them, messages sent from your domain may be flagged as risky, shunted into spam folders, or rejected outright by the receiving email servers.
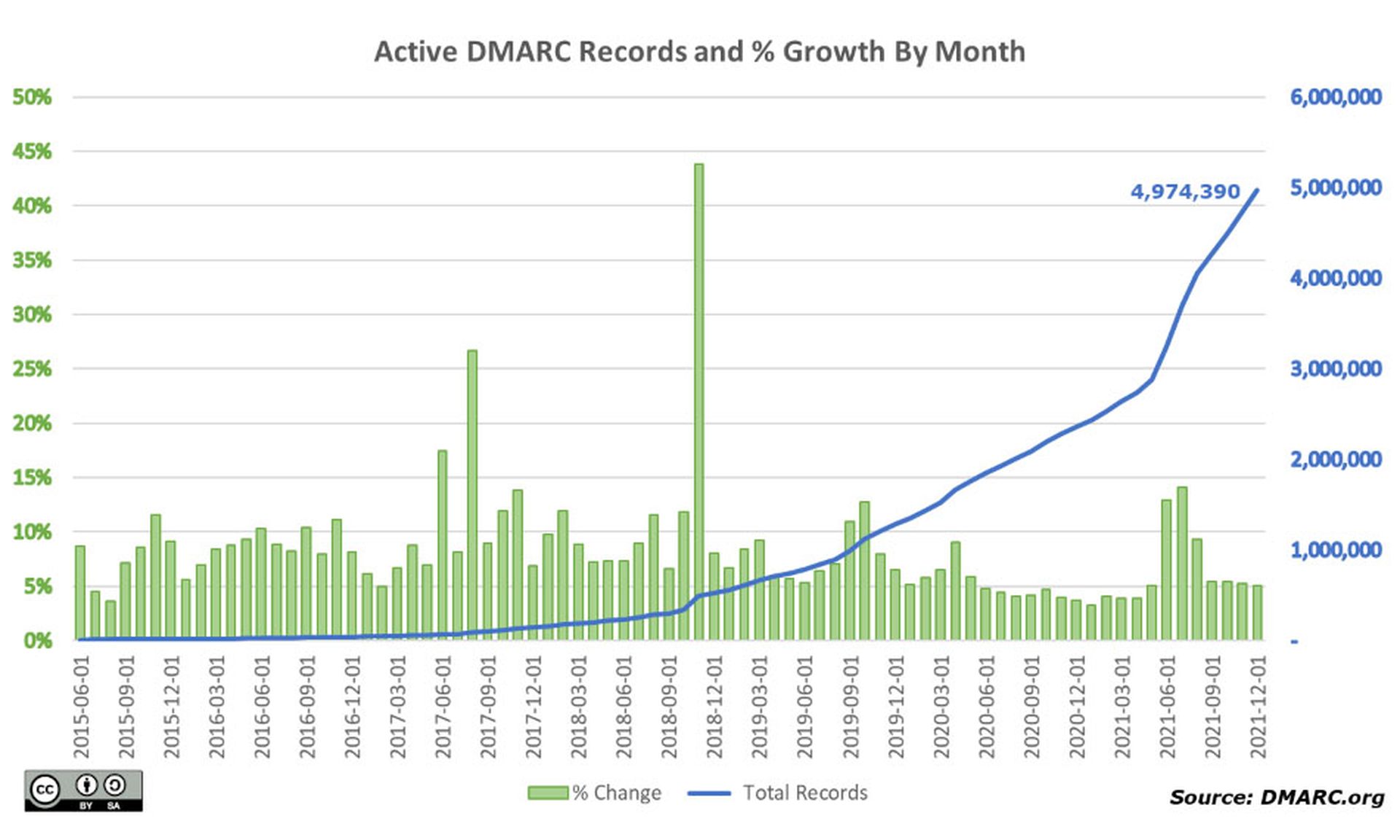
"Sending emails without monitoring the email authentication status is little more than a shot in the dark," said email-reliability provider Dmarcly in a recent blog post.
Technical ways to secure your email
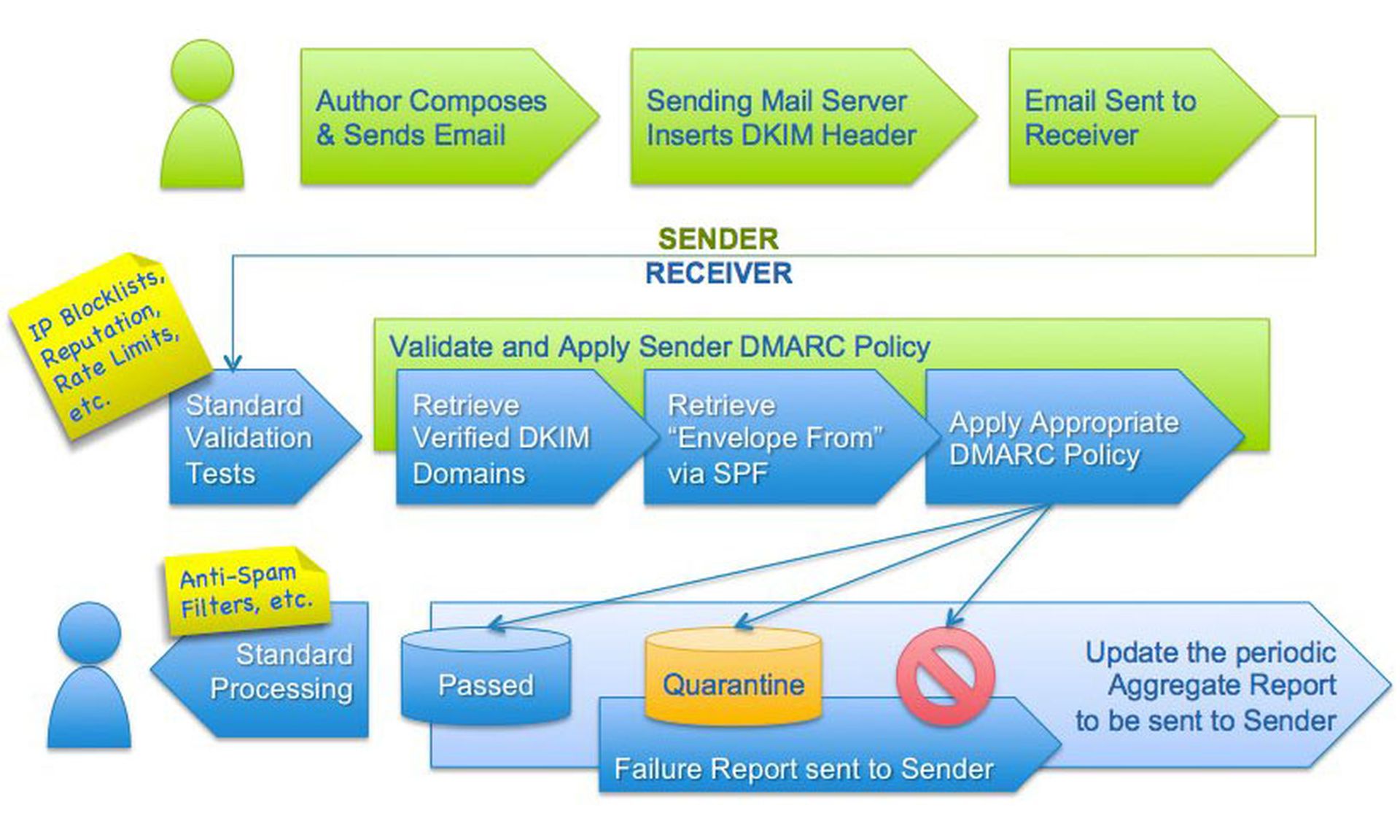
The most reliable technology for securing email is DMARC (Domain-based Message Authentication, Reporting and Conformance), which has sending and receiving email servers indirectly communicate to verify the authenticity of messages.
DMARC builds on two older technologies: Sender Policy Framework (SPF) and DomainKeys Identified Mail (DKIM). All three use records listed in the public Domain Name System (DNS), and DMARC needs SPF, DKIM or both to be set up in order to work.
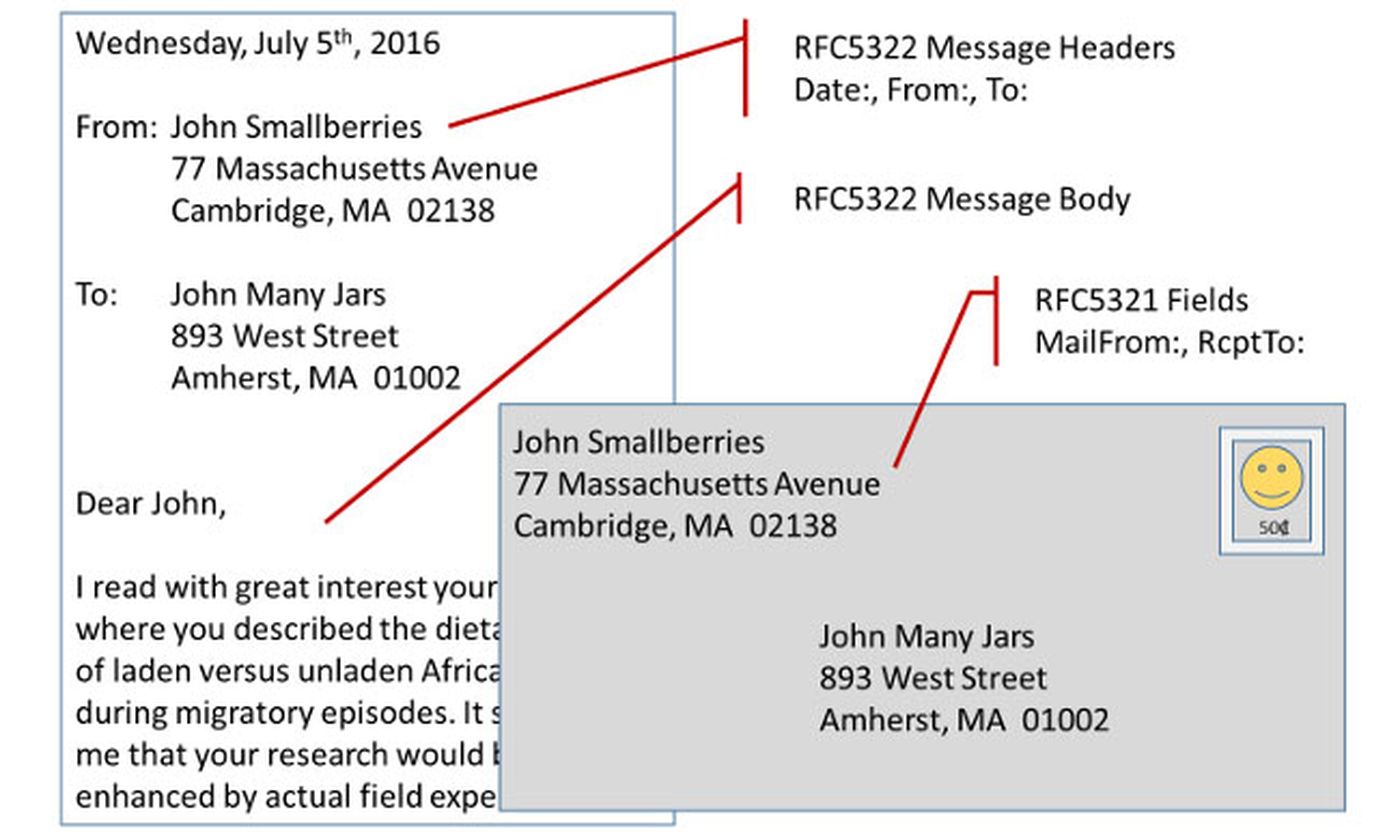
There are two ways to spoof a sender's email address. The more obvious method is to alter what the recipient sees: the sender's address in the "From" header content of the message. In a typed business letter sent via postal mail, this address would be in the "From" field found at the top of the page. But what's in the From field doesn't need to be true.
DKIM deals with header spoofing by having the sending server embed a hidden cryptographic signature right in the email message. The receiving server can then verify this signature by checking the sending server's public cryptographic key in DNS.
DKIM is not perfect. Because some mail servers still don't use DKIM, a verification failure doesn't always result in a delivery failure. Furthermore, a malicious server could "borrow" the cryptographic signature embedded in a legitimate email message to spoof the domain name and fool DKIM until the signature is changed.
The other way to spoof a sender's address is in the "MAIL FROM" field in the "envelope" of the message, the routing part that the email user usually doesn't see. Even to the receiving server (as opposed to the email recipient), a spoofed envelope MAIL FROM field will seem to come from the spoofed domain.
SPF stops this by matching the IP (Internet Protocol) address of the MAIL FROM domain against the IP address listed by the purported sending domain in its DNS records. If there's no match, then the message is flagged, quarantined or bounced outright, depending on the receiving server's configuration.
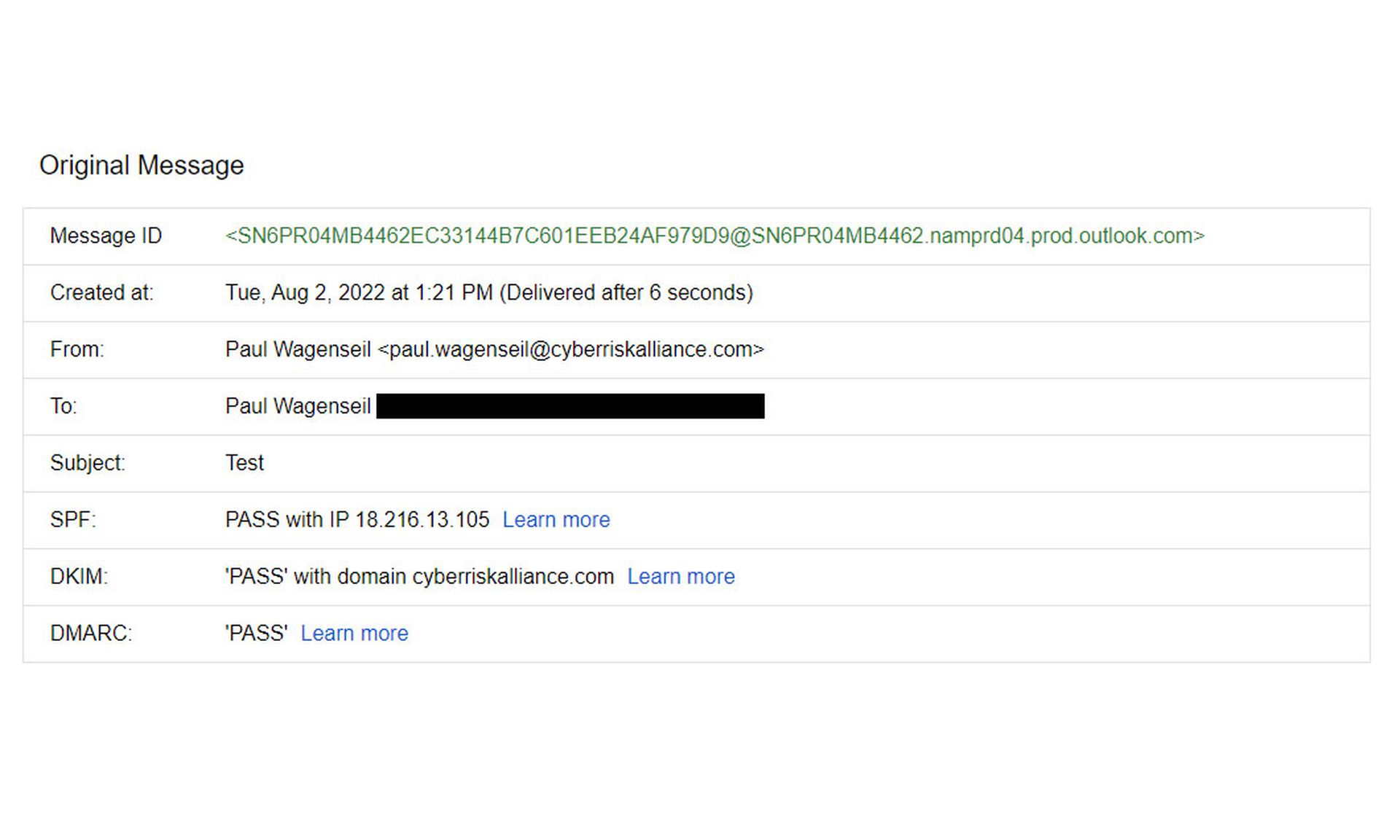
(You can see some of these parameters in Gmail by opening a message and choosing "Show original" in the three-dot options menu.)
SPF isn't perfect either. It lets messages with spoofed From addresses slip through if their MAIL FROM addresses are real, leaving recipients open to phishing attacks. It can also interfere with forwarded messages or with messages routed through mail exchanges. Many receiving servers mitigate this issue by having whitelists of known good mail exchanges.
DMARC expands upon SPF and DKIM by letting sending mail servers specify in their DNS entries whether they use SPF, DKIM or both. It also introduces the concept of "alignment" to check whether the MAIL FROM field, From field and DKIM signatures in a given message all match.
Significantly, DMARC lets sending domains have a say in how their messages are treated by setting a policy advising receiving servers whether to quarantine, reject or accept messages that fail alignment. Finally, it reports back to sending domains whether email messages have been properly delivered.
This still doesn't quite fix the issues with mail exchanges and message forwarding, especially since DMARC adoption is not universal. A newer system called Authenticated Received Chain (ARC) lets exchanges and mail forwarders borrow a sender's SPF or DKIM records to make sure DMARC validation is possible on the receiving end.
How to implement DMARC, SPF and DKIM
Setting up your domains and mail servers to use DMARC, SPF and DKIM can be complex, but there are some basic steps. You'll have to go through these steps for every domain you own, and even parked domains should at least get SPF records.
1. Set up SPF by modifying your domain's DNS listing with your domain hosting service.
2. Set up DKIM with your email delivery service, which will generate DKIM records — you'll need two — or manually on your own mail server. Then add the DKIM records to your DNS listings.
3. Wait 48 hours for the SPF and DKIM records to propagate throughout the DNS system.
4. Generate your DMARC record and add it to your DNS listing. Set your DMARC policy to "none" to indicate that no emails sent from your domain should be rejected due to misalignment.
5. Create an email address to receive DMARC reports. You'll get a lot of reports, so you may want to subscribe to a DMARC analysis service to handle them all.
6. After a few days, begin to analyze your DMARC reports, both aggregate (to provide an overview) and forensic (to spot and diagnose problems).
7. Use the reports to identify and fix DMARC issues, especially delivery and alignment issues.
8. One month after all your DMARC issues have been resolved, set your DMARC policy to "relaxed" to indicate that misaligned emails should be sent to quarantine.
9. If quarantine mode creates no major issues, then wait another three months and change the DMARC policy to "reject". This tells receiving servers that misaligned emails sent from your domain should be bounced.
10. Keep monitoring those DMARC reports and keep fixing what needs it.
Google has more detailed guides here:
Help prevent spoofing and spam with SPF
Increase security for outgoing email with DKIM
Increase security for forged spam with DMARC
The best defense is between your ears
The most reliable way to stop email spoofing from succeeding may be by training your workforce to spot bogus emails. No amount of technology can completely stop phishing emails, but a well-educated and well-practiced employee will spot them most of the time. Combine this stance with DMARC, DKIM and SPF and you'll be as safe as you can be.
Likewise, proper workforce training will educate staffers who manage the company's money about the different tricks used by BEC scammers. (You could also require that more than one employee sign off on large money transfers.) Ideally, employees should participate in dynamic scenarios that simulate common BEC scams.
"Many [employees] are not capable of using email and so the ability to recognize fraudulent emails is nil," an information-security manager in the education field told SC Media. "The good news is that mostly these users just delete all email."
Want to learn more? Read the full research report on email security: ATTACKERS ON HIGH GROUND AS ORGANIZATIONS STRUGGLE WITH EMAIL SECURITY




