In the past several years, the zero-trust security model has become the dominant paradigm for enterprise security, replacing the perimeter-defense security model.
The basic tenets of zero trust are simple: No user, whether human, device or program, should be extended permanent, implicit trust at any time, but instead should be continuously challenged to verify their identity. No user should receive more system privileges than necessary to carry out their role. Access to assets should be based mainly upon identity.
This contrasts with the perimeter-defense model, in which a user within the perimeter of the organizational network is allowed free rein until the user exits the network. Remote-access virtual private networks (VPNs) grant users working from elsewhere controlled access into the network perimeter. Access is based primarily on a user's location relative to the network perimeter, whether physically logging in from an internal endpoint or logically tunneling into the network via VPN.
The zero-trust security model makes more sense than the perimeter-defense model when applied to modern workplace environments that have many employees working from home, and when most organizations have migrated assets from on-premises data centers to the cloud. Most organizations do still have local networks and on-premises data centers, but the zero-trust model can be applied to those as well.
The innumerable pillars of zero trust
It still takes some effort to sell the idea of zero trust to C-suite executives and other stakeholders who aren't well versed in information security. To streamline those explanations, various "pillars" of zero trust have been proposed by analysts, security vendors and experts. Each pillar represents an essential element of a zero-trust implementation.
Yet there's no clear consensus on just how many pillars of zero trust there are, and what they might be.
Forrester Research, whose former analyst John Kindervag came up with the zero-trust security model in 2010 (the idea of "zero trust" is older), insists there are seven pillars. So do the U.S. Department of Defense (DoD) and the National Security Agency (NSA), although their pillars are bit different from Forrester's.
The NSA's civilian counterpart, the Cybersecurity and Infrastructure Security Agency (CISA), disagrees. It counts only five pillars of zero trust. Forrester rival Gartner, which has its own concept of "zero trust network access," also states there are five pillars, but they're not exactly the same as CISA's.
Meanwhile, the American Council for Technology-Industry Advisory Council (ACT-IAC), a nonprofit trade association, counts six pillars of zero trust. Microsoft's own explanation of zero trust names three pillars, but a study written by Microsoft's governmental arm and published by FedScoop lays out six, which only partly overlap with ACT-IAC's list of pillars and not at all with those of the other Microsoft explanation.
To cut through the fog, we asked Check Point Head of Security Services Product Management Aviv Abramovich how many pillars of zero trust he thought there might be. His response: three.
Abramovich cited least-privilege access, along with its corollary of no implicit trust, as the first pillar.
"You only get access to what you need, and it's not because you're in the right location," he explained.
The second pillar is continuous user verification.
"The fact that I trusted you two minutes ago doesn't mean I trust you now," Abramovich said. "Maybe something has changed. Maybe you, in those two minutes, managed to get malware on your laptop, or wherever you're accessing, and now I have to take that trust away."
"The third pillar I would say is the visibility and monitoring of everything," he added. "Being able to understand who has access, who has trust, to where, what, where did they log on to and how they logged on to it."
Abramovich told us he could get "more granular" and name up to 10 pillars of zero trust, but he wanted to keep the concept simple.
"If you look at Forrester's definition, they will tell there are seven things that you need — devices, identities, data and so on," he said. "And of course there's management and all that stuff. But I believe threes are easier to remember than sevens."
Other pillarization schemes
Microsoft's zero-trust explanation page comes close to Abramovich's list, citing:
We can presume that "assume breach" leads to total monitoring and visibility.
Forrester's report says the pillars of zero trust are:
The NSA/DoD lists these (re-arranged to better correspond with Forrester's version):
If you equate "workforce" with "user" and add "application" to "workload," you can see that the two lists match up fairly well.
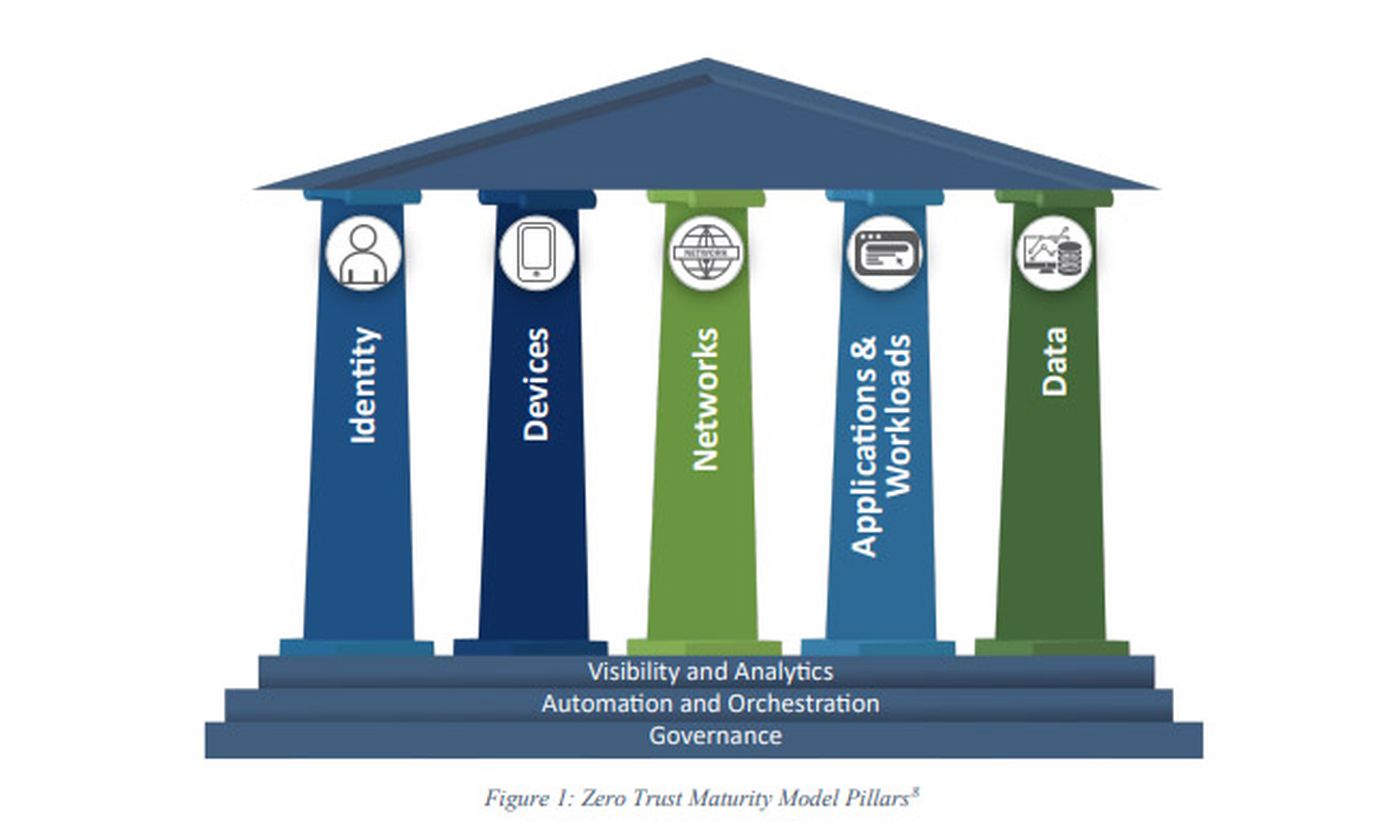
CISA has only these five pillars (again re-arranged):
But CISA provides a nice classical-looking illustration of how these pillars support the roof of the temple of zero trust, and how the pillars in turn rest on three stacked horizontal platforms of "cross-cutting capabilities": Visibility and Analytics as well as Automation and Orchestration, which correspond to Forrester's and the DoD's models, and also Governance, which is uniquely CISA's.
Gartner's list of five is similar to CISA's:
ACT-IAC has:
… as well as its own charming pillar image, which CISA credits as an inspiration, and which has "Data" as a cross-pillar floor.
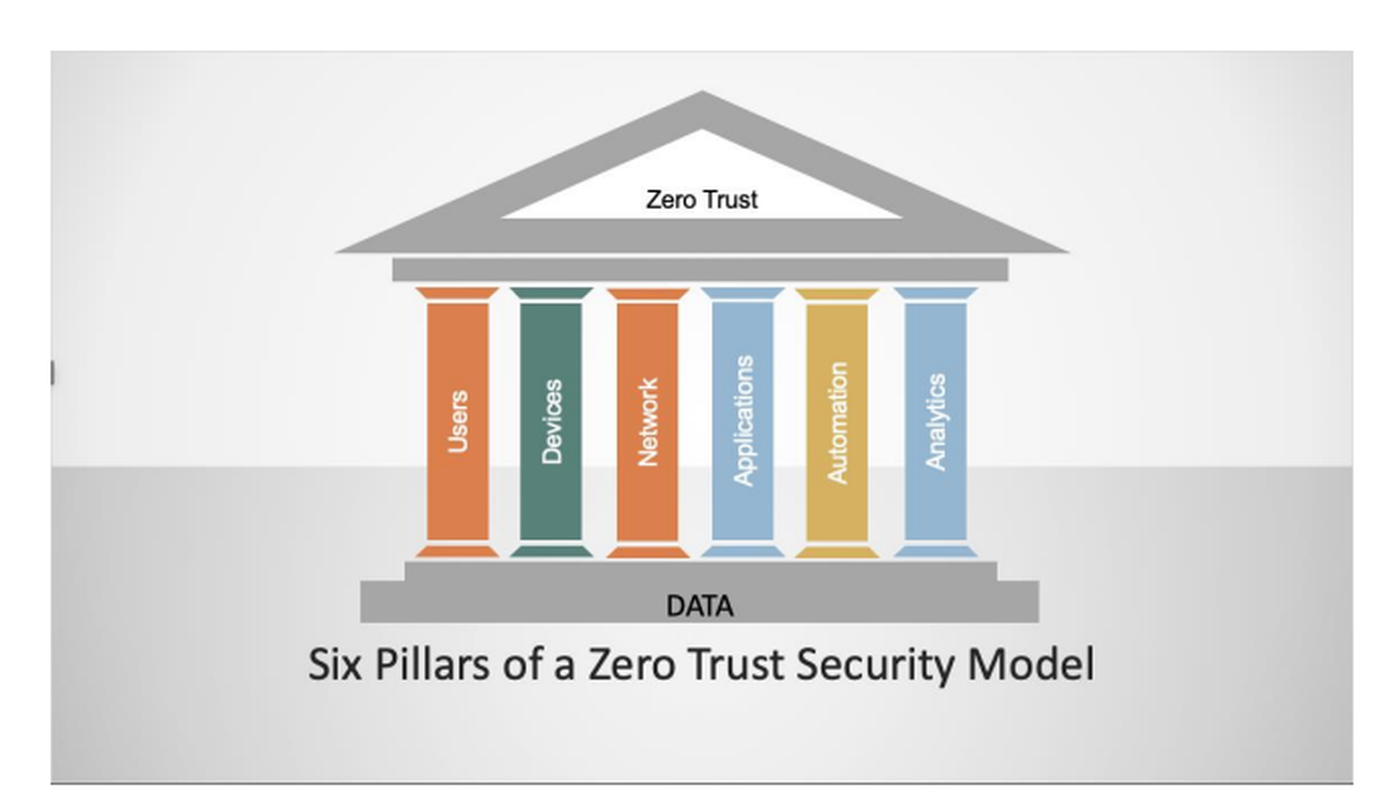
And finally, the Microsoft/FedScoop report lists these six:
What each pillar stands for
How do these concepts of the pillars of zero trust match up with Abramovich's? His "visibility and monitoring pillar" corresponds pretty well to the "visibility and analytics" component of some of the other schemes. But "least privilege access" and "continuous verification" both fold into the other lists' "Identity" or "User" pillars.
The identity part is perhaps easiest to define. Strong identity and access management (IAM) is central to a zero-trust security model. As Abramovich pointed out, an organization that doesn't claim to be using zero trust may be implementing some of it anyway if it's using a modern IAM solution that continuously challenges, verifies and monitors its users, even within a perimeter-based network.
"If you've implemented security in the sense that you require authentication before access, you do validation, and you monitor the application," Abramovich told us, "maybe without even knowing or meaning to do it, you've kind of already implemented some of the zero-trust principles."
Likewise, the visibility and analytics part is essential to zero trust because the system needs to know exactly where each user is going and what the user is accessing, and to be able to log it all. Or, as the ACT-IAC explanation of its "Analytics" pillar states, "You can't combat a threat you can't see or understand."
The other pillars that Abramovich didn't list are part of best security practices in general and are not unique to zero trust. While each greatly aids the zero-trust security model, it's debatable whether any is necessary for zero trust.
"Network" is probably the most important "other" pillar. Let's take it to mean that the network should be properly segmented and monitored, with even the most privileged users challenged to verify their identities when moving from one segment to another. Zero-trust or not, this concept is essential to modern information security.
"Devices" can be interpreted to mean endpoint security, which covers a vast range of defense techniques ranging from device-specific antivirus software to automated endpoint detection and response and even "extended" detection and response that goes beyond endpoints. As with network segmentation, a modern organization should be implementing EDR with or without zero trust.
But "devices" also refers to device authentication, which aids in user verification, especially context-sensitive multi-factor authentication, and more properly falls into Abramovitch's "continuous verification" pillar.
"Applications and Workloads" or "Apps and APIs" also cover a lot of ground, from secure application development (DevSecOps) during the software development life cycle to web-application firewalls to cloud-workload protection to a cloud access security broker tool (CASB). The CASB is perhaps the feature most important to zero trust, as it enforces access policies between users and cloud assets. Again, however, it's something any cloud-using organization, especially one using a secure access service edge (SASE) model, should have.
"Data" has aspects of asset management, in terms of inventorying and categorizing all existing data. Categorization and classification of data make it easier to isolate and protect the most sensitive data, and to restrict access to it. That's very important to zero trust but is also an important part of information security in general.
"Automation and orchestration" is part of a sea change occurring in information security that incorporates machine learning (ML) and automation. It's especially prominent in security orchestration, automation and response (SOAR), which automatically organizes a multi-tool response to a security incident. It also refers to the growing use of artificial intelligence in security tools, which promises to revolutionize incident-response time and efficiency.
Most zero-trust models will use automation for routine authorization and verification of users, and will use ML to analyze where, when and how a user is logging in and decide whether to ask for a second factor of authentication.
FedScoop/Microsoft's "Infrastructure" overlaps with both "workloads" and "networks" and involves anomaly detection, configuration management and incident response to protect servers, cloud workloads, containers and micro-services. These aspects of information security are helpful to a zero-trust security model but are not an essential part of it.
A question of risk
When all of the components that aren't explicitly zero trust are boiled away, what's left standing are Abramovich's three pillars of zero trust: continuous verification, least-privilege access and (near) total visibility and monitoring.
"It's a philosophical question of what is the definition of zero trust, really," Abramovich told us. "As long as you put security to mitigate risk, that's the core foundation of zero trust. Just mitigate your risk."
Read Check Point's solution brief for more on its approach to zero trust.




