Third-party relationships have expanded exponentially as companies seek outsourced services and software to perform optimally and backfill talent amid the ongoing pandemic.
However, the spike in third-party dependencies has also granted threat actors a larger launchpad to target weaker vendors with strong market penetration and quietly surveil or paralyze web apps containing sensitive data.
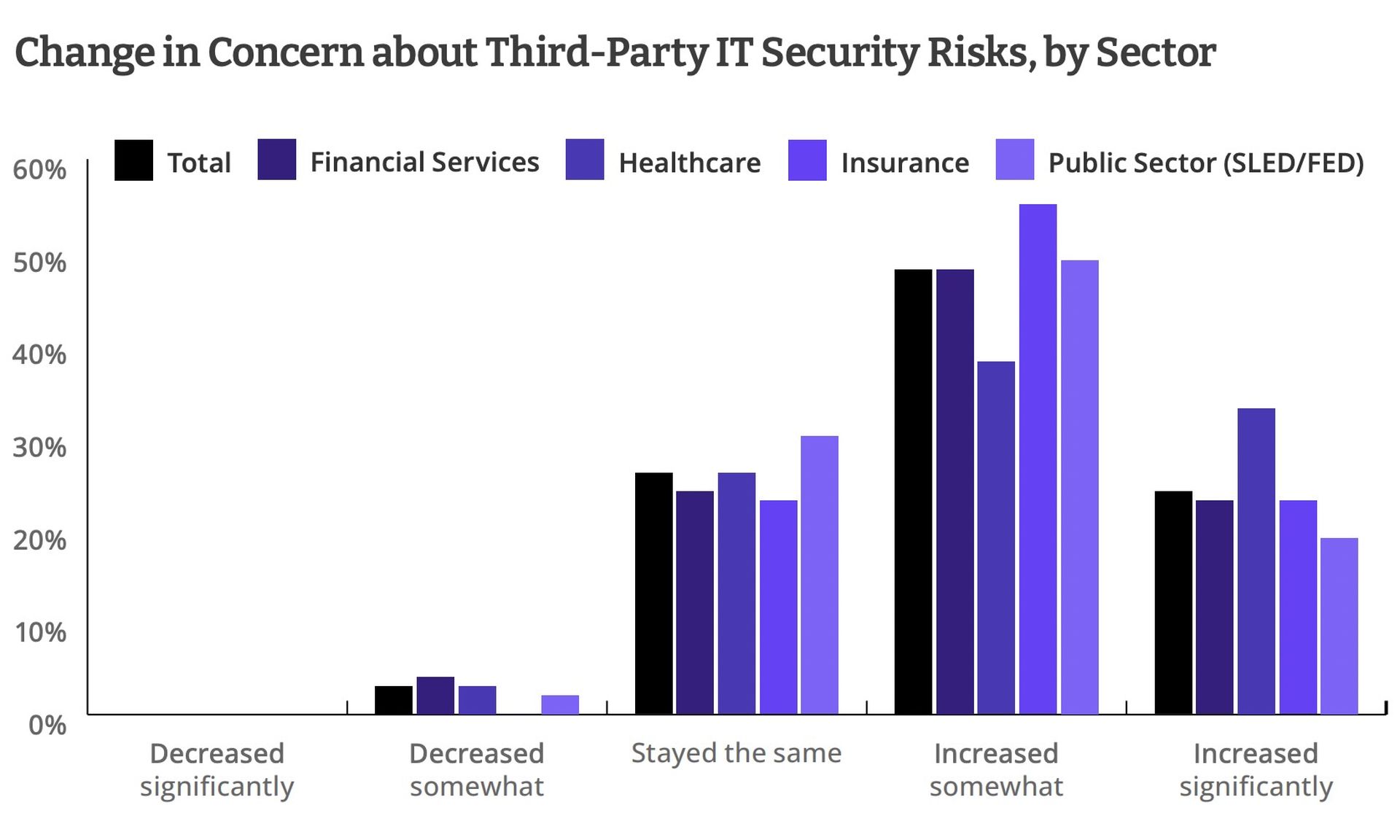
Recent studies suggest a grim future is ahead for organizations who neglect to enforce baseline security controls on third party providers. In a 2021 survey of 250 IT security professionals, 91% of respondents reported experiencing a security incident in the past 12 months that tied back to a third party. 67% said their organizations had seen a ‘significant’ increase in third-party-related security events during the past year.
With such concerns abounding, it’s clear that many organizations find it challenging to secure third-party services. But why?
How third-party dependencies increase risk
Like it or not, organizations that accept the services of a third party vendor also accept the responsibility of making sure those services are secure. And such services – when not properly vetted -- introduce their own risks, as listed below.
- Expanded attack surface: Third-party services can expand an organization’s attack surface by introducing dependencies with other libraries and scripts beyond the organization’s initial purview. In many cases, the third party needs to be able to read and react to the primary organization’s data so it can perform its intended function. Attackers can exploit this trust by breaching third party components in order to gain access to the primary organization.
- The changing ecosystem: Most apps don’t exist in a vacuum but in a constantly shifting ecosystem of endpoints and updates. Even a secure app can be undone when interacting with third-party assets (in CSS files, packages, scripts) that carry their own vulnerabilities. Like any other software, these assets can change over time as new updates or features become available. Attackers can take advantage of this fact, embedding malicious code in a third party script that the app reads as a routine fix.
- Data in the crosshairs: Millions of users entrust apps with keeping their information safe: financial records, medical and health records, professional credentials, passwords, private appointments, the list goes on. In turn, organizations entrust third parties to be responsible stewards of this data. Attackers know that isn’t always the case, and they're scanning for any detectable weak links among the community of third-party providers.
Mitigating third-party risk
Given the risks, one might recommend reducing or eliminating third party dependencies altogether. But the reality is that organizations benefit from the capabilities such suppliers provide: expense reporting, email services, data storage, and managing industrial control systems are just a few of the many important tasks that third party software vendors can fulfill, thereby permitting the host organization to redirect its IT talent to focus on pursuits more relevant to the goals of the business.
Indeed, third-party dependencies show no rate of slowing down. According to research by CyberRisk Alliance, more than a third of organizations represented in the study had 100 third-party relationships or more. Some sectors, like healthcare and government, reported working relationships with 500 or more vendors at any given time. The COVID-19 pandemic accelerated matters, as organizations contracted with third parties to meet the needs of an increasingly virtual work environment and remote workforce.
A high volume of third-party services can certainly raise the risk profile of an organization, but it doesn’t have to be that way. Organizations can institute several best practices to ensure they have secure, working relationships with their vendors.
Best practices for managing third-party risk
#1: Identify third-party assets and dependencies. As the saying goes, you can’t protect what you can’t see. Organizations are swimming in data, but oftentimes the app infrastructure governing how that data is used is itself a conglomeration of third-party services. And while some of these dependencies are known, many more fly under the radar and are accepted prima facie. The Open Web Application Security Project, or OWASP, recommends organizations use automated tools to identify and analyze third-party dependencies as early as possible in the development lifecycle.
Software composition analysis, dynamic application security testing, and static application security testing can all perform automated scans of code to identify hidden vulnerabilities, cross-check against known CVEs, and help catalog an app’s dependencies on third party assets. More contemporary, next-gen security solutions even combine dynamic security testing with interactive security testing, or IAST, to show vulnerabilities that are only detectable when the app is running. These tools can even assign severity ratings and recommended treatments so that developers can focus on resolving higher-order vulnerabilities in third-party code.
#2: Continually assess third-party risks. Identifying third-party assets and dependencies is just the beginning. Organizations need to continually exercise vigilance by holding third-party software to the highest standard. That means asking the right questions about revealed vulnerabilities, such as:
- How severe is the vulnerability?
- What level of effort is required to resolve it?
- Is this an isolated dependency? (Will fixing it impact other third party services?)
- How relevant is the affected service in question? (Do we need it, or is it just nice to have?)
By weighing the risks, organizations can determine their next steps in reporting the vulnerability to the third party and collaborating on a solution.
#3: Zero Trust risk mitigation. The Zero Trust security approach says organizations should never extend blanket trust to anyone, not even their most privileged users in the organization. Zero trust denies access by default, and asks for verification across every endpoint within the network --- yes, including third parties. Organizations can adopt Zero Trust risk mitigation measures by forcing third parties to comply with Zero Trust practices. To further mitigate instances in which trusted third parties might fall short of the mark, organizations can use the services of a cyber ratings platform that continuously monitors and reports “trusted third-parties” for breaches.