Organizations can use a cloud-native app protection platform, or CNAPP, to bolster their security processes.
It is not uncommon for organizations to bite off more than they can chew by procuring various point-solutions to beef up their cloud security. However, these tools (which may come from different vendors) often target specific security issues in their respective silos. These silos block information exchange, making it much more difficult to identify threats and prevent attackers from embedding across multiple cloud services.
A CNAPP aims to fix this by combining disparate cloud security functions (e.g. CSPM, CWPP, KSPM, CIEM, IaC) into one proprietary software solution, offering a platform-level view of the entire attack surface. CNAPP configurations can also include infrastructure-as-code automation, which allows for earlier discovery of faulty code and misconfigurations in the CI/CD pipeline. In other words, it grants DevOps teams greater visibility, ease of control, and speed in resolving cloud security issues as they emerge.
How to deploy a CNAPP
So, let’s say you’ve decided to invest in a CNAPP. What do you need to keep in mind to get the most out of it?
Consider the purpose of deploying a CNAPP: It is designed for consolidating cloud security and reducing complexities in the management of security tools. With that in mind, there are several important items that security leaders should consider as they identify a CNAPP that works for their cloud needs.
Checklist for deploying a CNAPP
#1: Strategize before diving into the deep end. Before pulling the trigger, organizations should consider how a CNAPP will work for their business needs.
- Do they have a hybrid cloud model that spans on-premise, private, and public cloud environments?
- Do they have contingencies for securing all (not just some) artifacts across the dev cycle, including source code, containers, VM files, IaC scripts, APIs and cloud configuration files?
- Will they need to shift responsibilities and feedback loops to accommodate the platform approach?
The right CNAPP strategy should be flexible in addressing instances across all these spaces and more. It’s worth taking time to understand how a CNAPP might reveal gaps in the architecture and what needs to be done to address them.
#2: Be clear in communicating to vendors your requirements. As the CNAPP market is still relatively young, it’s worth negotiating one to two year contracts with a vendor in case new features become available elsewhere. Gartner recommends requiring CNAPP vendors to only charge for licenses-based modules that your team actually uses, rather than jumping all in on the full set of integrated capabilities (as the latter could take several years to fully adopt). Organizations can also require that vendors scan containers already in development and provide features like infrastructure-as-code scanning, Kubernetes security posture management, and runtime assessment using APIs to get the most bang for their buck.
#3: Keep the focus and the priority on developers. A CNAPP can help developers create a more secure environment with better visibility. However, implementing new technology may still present some challenges. Taking a platform approach to cloud-native security could necessitate a shift in how teams work together, structure and report their findings, and configure and test new features. Organizations should provide time and resources for devs to familiarize themselves with the CNAPP’s offerings, such as improved threat scanning, the ability to automate cloud configurations, and proactive controls for fixing code in development rather than at runtime.
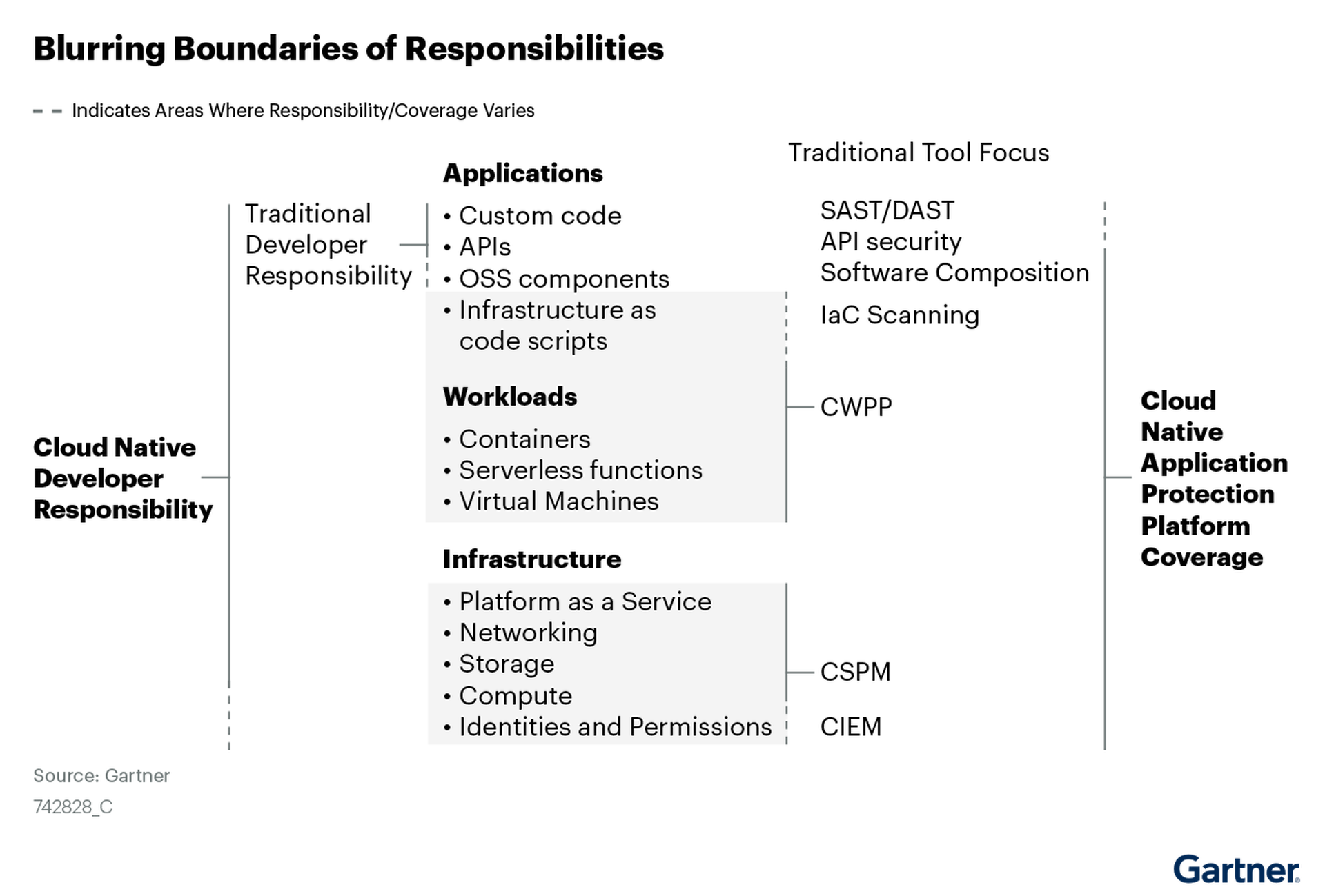
#4: Treat security and compliance as a continuum from development to production. The added value of a CNAPP includes consolidated insights from the development lifecycle. By integrating solutions, a CNAPP platform builds shared context for security and development teams to analyze for future improvements. Unifying functions, tools and oversight into a single platform gives DevSecOps greater visibility throughout the development process. With infrastructure-as-code automation, a CNAPP platform helps developers see and correct problems before they lead to an incident. Overall, this results in fewer bugs and more expedient production.




