Your company's website or mobile app doesn't need every new account holder to create a username and password. Instead, you can allow "bring your own identity," or BYOI, in which credentials managed by a third party, such as Google or Facebook, grant access.
BYOI is convenient for the site visitor and app user, may add a degree of crucial identity proofing for the service owner, and adds more security and privacy for both. Here's how BYOI beefs up security and how it relates to customer identity and access management (CIAM).
What is BYOI?
Bring your own identity is the process whereby login credentials issued by a third party grant a user access to multiple online services. With BYOI, the user logs into a credential provider, which then transmits an access token (but not the actual credentials) to the service provider or website.
Social login, which uses a Google, Facebook, LinkedIn or other social media password to log into other websites, is the best-known form of BYOI. BYOI credentials can also be provided by banks, government agencies, mobile networks or stand-alone services.
A potential downside of BYOI is that it creates a single point of failure that could affect multiple accounts.
"Should the user's password and login ID become compromised," said Iriana Chizek of Wells Fargo in an undated article in the PA Times, it would create a "cascading effect that ensues on all shared sites."
If social media credentials are used, the user's social media account can be used as a form of weak identity proofing — assuming the social profile is real.
What identity proofing is
Identity proofing ties an online account to a real person, often by having the user scan and upload a government-issued identity document such as a driver's license or passport.
It's different from authentication, which only checks that a person logging into a website is the same person who created the account. Identity proofing verifies the person's legal name and (sometimes) address.
"Identity proofing should be part of any customer-identity strategy," Jordan Griffith, product marketing manager at Ping Identity, told us. "It's very common in financial services, and it's tying a real person to the digital identity."
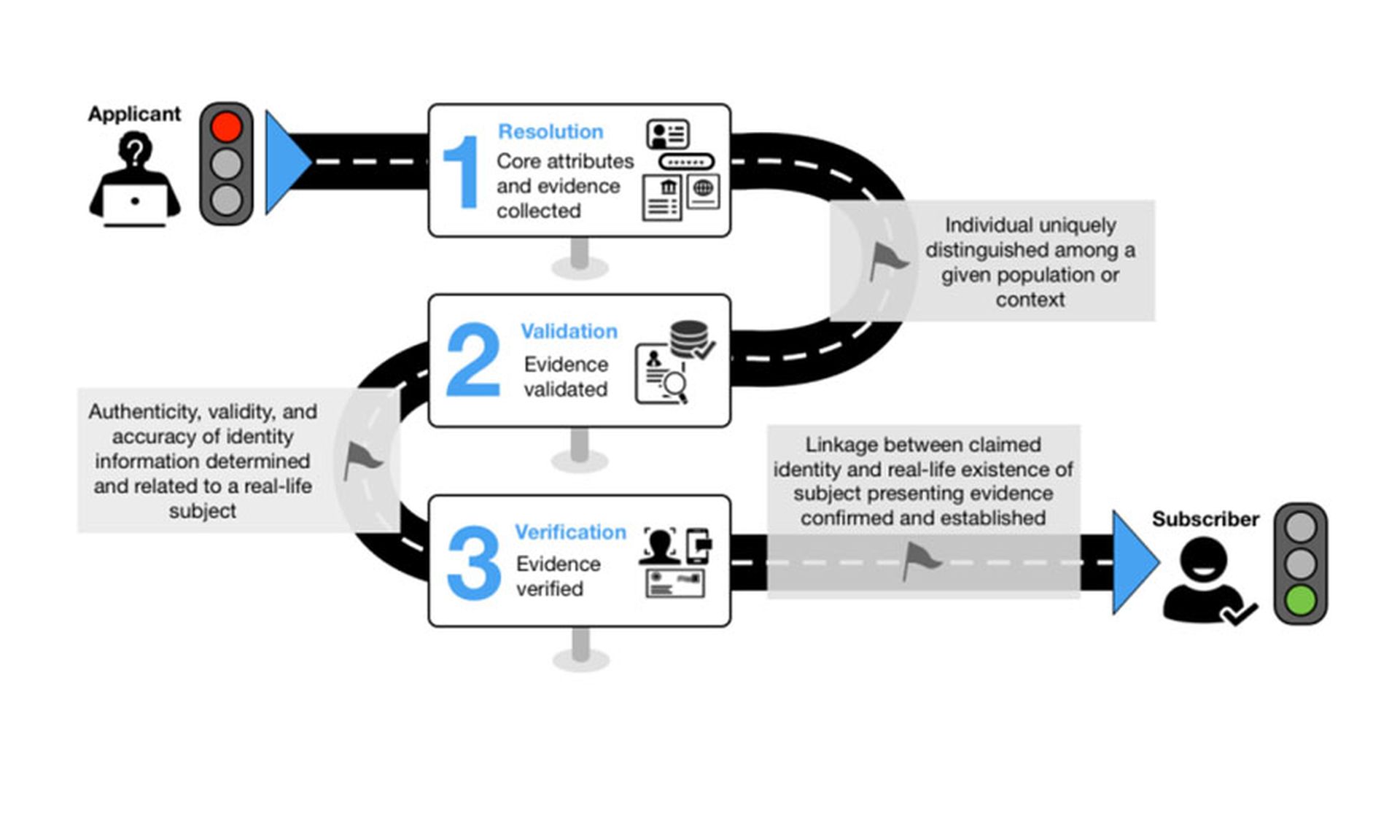
The U.S. National Institute of Standards and Technology (NIST) lays out guidelines for federal agencies using identity proofing in Special Publication 800-63A, defining three identity assurance levels (IALs).
IAL1 demands "no requirement to link the applicant to a specific real-life identity." For example, a Twitter account requires only a working email address, and a Google account only a working mobile phone number.
IAL2 demands some form of government ID, directly or not. When you create an online bank account, it's most frequently tied to an account that you created in person at the bank and for which you provided strong proof of identity.
IAL3 is the most stringent and demands some form of physical presence. Registering an online account with the U.S. Internal Revenue Service requires not only scanning a government ID, but a videoconference with a representative of the identity-proofing company contracted by the IRS.
Smartphones have made IAL2 and IAL3 identity proofing easy. A video made by Entrust shows a woman first verifying her device (an iPhone), then scanning her driver's license with a smartphone app, and finally taking a selfie to make sure her image matches the one on the driver's license.
How BYOI and identity proofing intersect
Social logins fall under NIST identity assurance level 1. But, as Megan Rees of Expert Insights said in a March 2022 article, "more secure methods of BYOI can include bank IDs, government-issued IDs, credentials provided by digital identity companies, and more."
These require, Rees said, "more rigorous identity checks, and often, the physical presence of the user."
Most Swedish citizens for example use BankID, a form of ID that uses a cryptographic certificate kept in a smartphone app, a smart card or a computer's hard drive. Users must present official government ID in person at a bank branch before registering with BankID.
Once approved, BankID users can use their smartphone or computer as a BYOI tool to sign contracts, access medical records, log into government websites and make mobile payments.
A BYOI implementation like BankID that uses NIST IAL2 or IAL3 can pass along a fair degree of identity proofing to your website. For example, you'll know that users have given you their real names. There's less assurance with Google or Facebook credentials, which are IAL1, but you will at least know that those users are tied to real accounts.
How BYOI and identity proofing tie into CIAM
Customer identity and access management (CIAM) solutions streamline the process of account creation and personal-data handling for customer-facing online companies. A good CIAM platform will let users bring their own identities by offering at least social login.
"BYOI has to be a table stake for any CIAM solution," said Griffith. Social logins are the most common method, she added, but "if third platforms are using open standards like SAML or OAuth, then it would be possible to integrate them into CIAM solutions."
Not every BYOI implementation will necessarily "capture" user data from social logins. But those that do will need a CIAM on the back end. And the CIAM solution should also be able to perform some kind of identity proofing, which is a functionality increasingly build into platforms.




