Incident response (IR) is one of the key components of a strong cyber security program, but it does not work well when fragmented and disjointed. This is especially true in emerging remote and hybrid work environments, where security teams must track many more endpoint devices and deal with much greater complexities and threats than in the past.
Modern cybersecurity typically involves coordination among many different components, including processes, policies, tools, services, and people. Incident response must follow that same approach to effectively prevent or defend against compromises that may happen across the enterprise.
For that to happen, integration among the various IR components is vital. There can be no silos among different solutions and data sources when interaction and information sharing is necessary for good security.
To ensure that organizations implement the best possible incident response program, Sophos recently released a guide with 10 key steps security teams must take. The guide is designed to help practitioners:
- Define the framework for their cybersecurity incident response plan,
- Learn the 10 main steps such a plan should include, and
- Understand the role managed detection and response (MDR) services play in supporting the plan.
The 10 steps are captured in this chart:
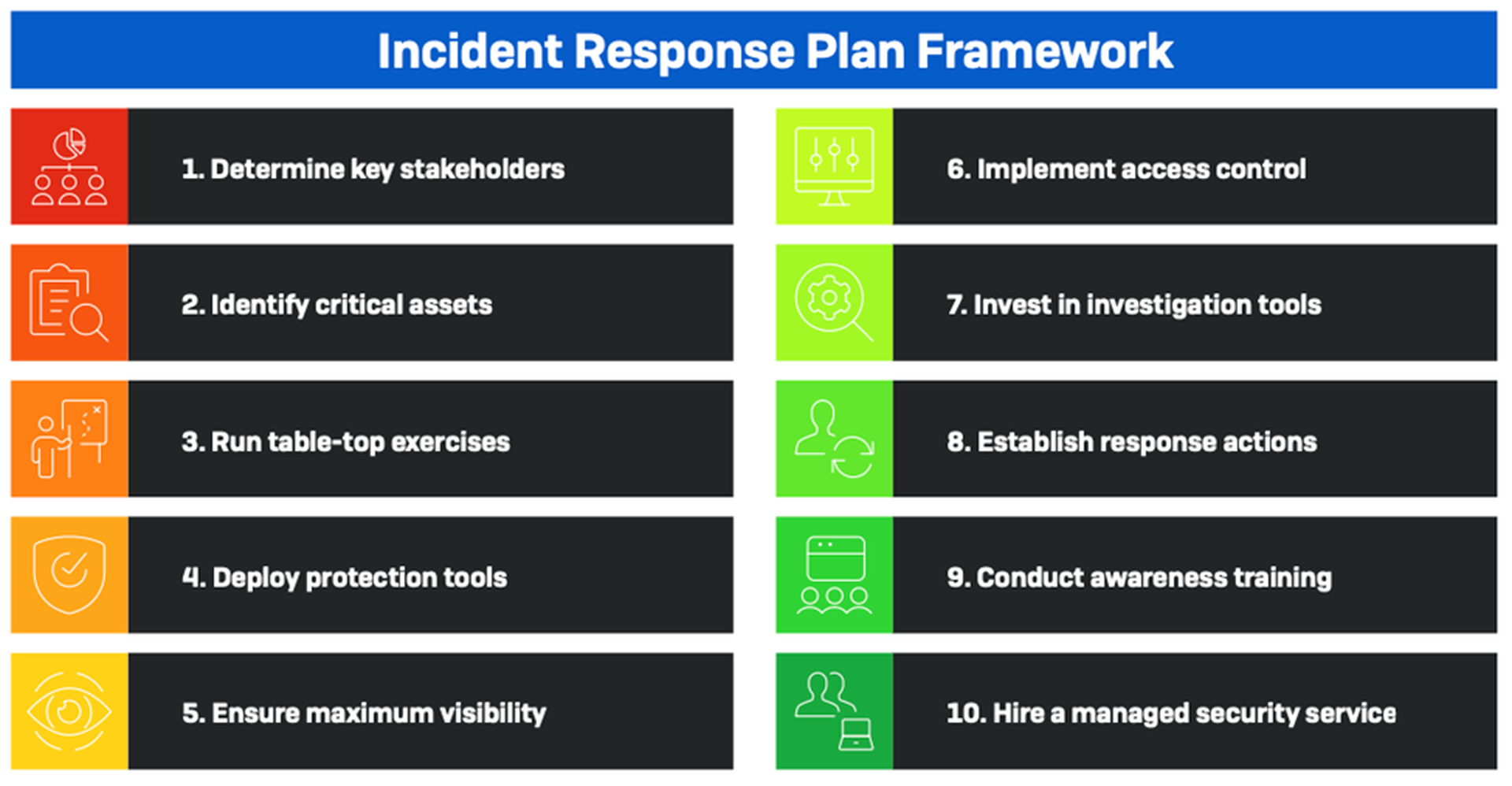
For detailed explanations of each step, download the full report here.




