Anyone well versed in cybersecurity is familiar with the parameters of incident response. Following a data breach or other incident, the attack vector and affected systems are identified, the holes are plugged, and a forensic examination takes place.
If it's a major incident that makes headlines, say a data breach at a Fortune 500 company or a top U.S. government agency, then some of the big guns in incident response — Mandiant, CrowdStrike, etc. — may be brought in to investigate.
Less glamorous, but arguably just as important, is the post-incident response. This isn't about better defending the targeted organization, remediating flaws or preventing future incidents.
Instead, it's about determining what kind of data may have been stolen or compromised, especially personally identifiable information (PII) and personal health information (PHI). It also involves compiling lists of the affected parties, clients and individuals to be notified.
"We operate in a niche space in breach response," explains Stephen Kennedy, Director of Client Services, Managed Review, and Cyber Incident Response Services at Conduent, provider of digital business solutions and services spanning the commercial, government and transportation spectrum. "Typically, we come in after the breach has been contained, identified, and mitigated. We handle the human element of the response."
It's not quite cybersecurity
Conduent's post-incident response services touch upon cybersecurity, but the company is adamant that it's not in the same line of work as the forensic experts who try to figure out how attackers penetrated a network.
"We swim in that same ecosystem, but we would never market ourselves as a cybersecurity company," says Kennedy. "If you said to me, 'Steve, here's a system. Go look at and tell me how these guys got in,' I wouldn't even pretend to know where to go with that. That's not what we do."
Conduent was spun out of Xerox's Business Services division in 2017, and its core mission is still providing digital services, especially data-processing services, to organizations in a dozen different industries, including banking, government and healthcare.
The post-incident response team is part of Conduent's Legal, Compliance and Analytics division. One of the division's core competencies is eDiscovery, or electronic discovery — the process of sifting through mountains of electronic data to find evidence pertaining to litigation, investigations or other legal matters.
"What we bring to the table that other companies don't," Kennedy says, "is a bespoke solution informed by the business that we've been in for decades, which is eDiscovery."
What post-incident response is
While eDiscovery is a core part of litigation preparation, the process is also tremendously helpful if you're trying to determine which of the thousands or millions of documents and other electronic records compromised in a cybersecurity incident might contain sensitive or personal data — Social Security numbers, health records, credit-card numbers, and so forth.
That process is the greater part of post-incident response.
"Data culling, minimizing data, reducing what a review team would look at in traditional litigation -- those same techniques can be applied here," says Kennedy. "Eliminating the white noise, eliminating documents, things that are not going to contain PII, PHI, other sensitive information."
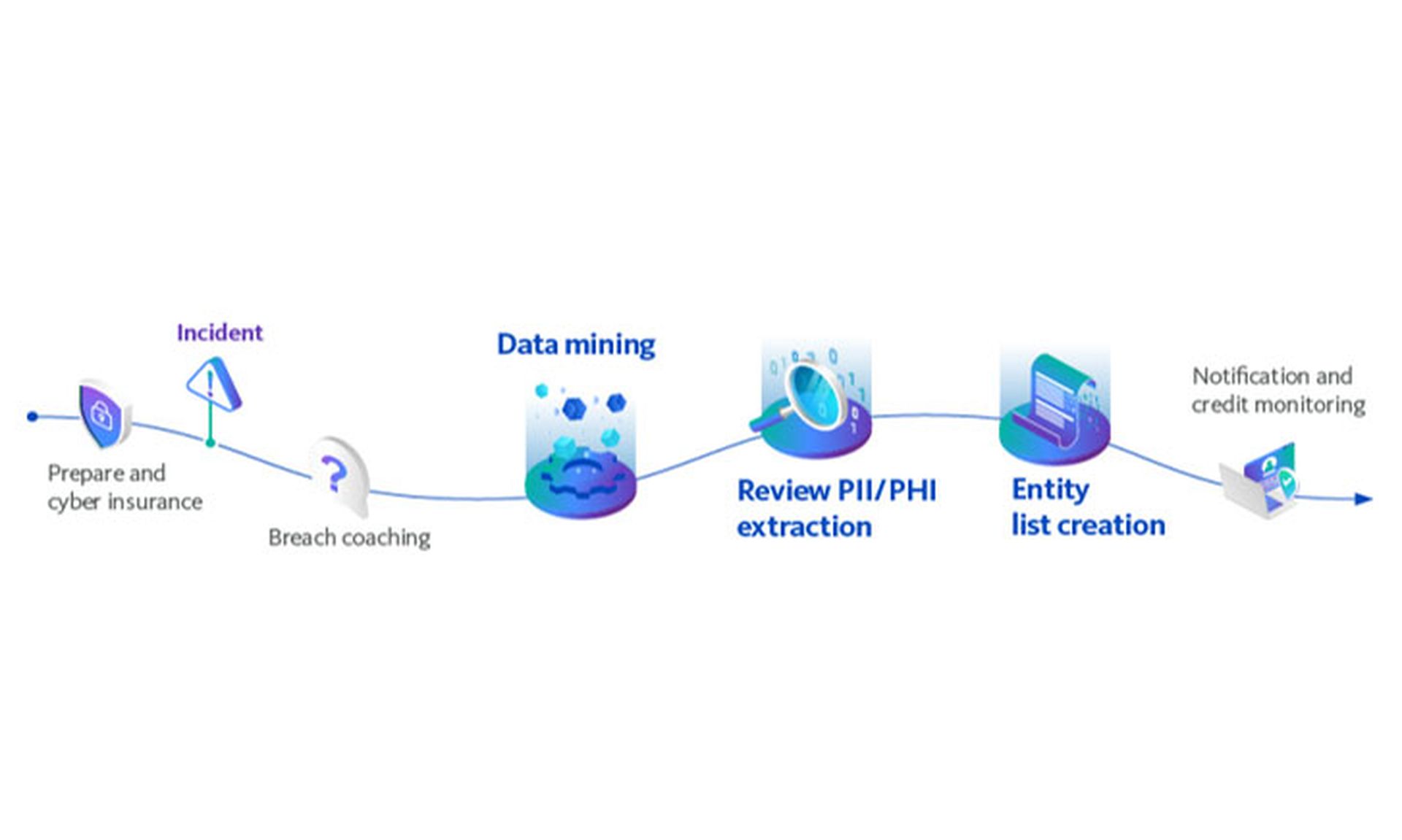
Conduent calls its post-incident response service CyberMine and breaks the process down into three parts.
First, after the compromised data has been identified and segregated, it is handed off by the client, or the external incident-response company, or the client's insurance carrier, or even a specialized firm called a breach coach to Conduent to be analyzed and mined.
"We don't even know the full details because, for obvious reasons, clients don't want to give that information out, and we don't need it to do our bit," says Kennedy.
"Once they've identified what's been hit, they send us the data, and we can tell you whether there's three hundred people or one thousand people or a million people, where they lived, and as much of their information, unfortunately, as is in in that data set."
Credit: Conduent
Any "responsive" data such as credit card numbers, Social Security numbers, full names, dates of birth and health records then will be extracted and presented to the client. One of the aims of Conduent's post-incident analysis is to avoid duplication and minimize the amount of significant information to be acted upon.
"We do a lot of sampling of data, taking that those findings back to a client, and continuing to do that process, because ultimately, we want to have people look at as little as possible," says Kennedy.
Minimizing the data also helps the clients save money, he adds, relating the case study of a client that began with 4 million records that Conduent pared down to 15,000 relevant ones.
"We probably saved them close to half a million dollars by taking that approach, " he says. "There's no great benefit to us other than doing what was right for the client, which is always the goal."
Once the data has been thoroughly analyzed, Conduent can create an "entity list" of the affected parties, whom the client then notifies.
The role of automation
Wrestling with huge amounts of data is partly automated through the use of an eDiscovery tool Conduent has called Viewpoint, which uses industry-standard technology assisted review (TAR) and some of the scientific methodology and thinking behind the computer assisted learning (CAL) process to quickly rip through large datasets.
Kennedy says it's not always the size of the dataset that matters. Small datasets can be significant.
"A small volume of data does not necessarily mean a small impact," he tells us. "If you have someone get the right Excel spreadsheets with all your clients and all of their information in it, it can be still quite extensive and expensive, even though it's a fairly small dataset."
Slower is sometimes better
Because of the increasing number of rules and regulations surrounding data breaches and other incidents, such as the U.S. Security and Exchange Commission's four-day notification rule for "material" incidents, post-incident response has bearing upon compliance.
Kennedy warns that organization's must be careful with the terminology used.
"'Breach' is a real term of art," he says. "We use POST incident, because incident is, 'It's an incident.' There's lots of incidents. Not all of them are breaches."
Does that mean that Conduent is going to rush through its data analysis to get the final results to the clients as fast as possible?
No, says Kennedy, because taking it slowly and deliberately gives you a better view of the data, and involving the client throughout every step of the process often yields better results.
"This can be a very frenetic business where things are happening very quickly, and there's tight deadlines," he says. "But sometimes just if you slow down a bit, think, plan, prepare and then execute, the benefits can be really tangible."




