It sounds like a techno-horror movie: Most of the user identities in the modern workplace aren't human, and the number of non-human identities is rapidly growing.
Are we being invaded by aliens? Zombies? No, these non-human identities, or NHIs for short, are used by computer programs, devices, cloud services and other digital processes to interact with each other.
Much in the same way a human user logs into a PC or a cloud service to access its contents, a machine or program uses an application-programming interface (API) or a service account — just two of several kinds of NHIs — to get access to another machine or program.
The problem with NHIs is that, unlike human users, they often aren't properly managed by legacy access-management systems.
Their passwords tend to not be regularly rotated, they often have more privileges than they need, they may not be adequately monitored, and they may not use multi-factor authentication (MFA). Even worse, a non-human identity can cause a very big mess if it's compromised, as it can give attackers a hidden, powerful way into a network.
NHIs also vastly outnumber human identities. We've seen figures ranging from 20:1 to 80:1, but there's no question that the proportions are growing. The advent of widely used artificial intelligence (AI) accelerates the growth of NHIs, with organizations rapidly deploying AI "agents," or tools with specific tasks such as customer service or sales development.
So how can an organization properly manage AI agents, service accounts, APIs and other kinds of NHIs? One of the better ways is to use a comprehensive, cloud-based, highly automated, identity-security platform that combines the features of identity and access management (IAM), privileged access management (PAM), and identity governance and administration (IGA).
Such a platform will be able to automatically onboard, provision, monitor and manage both human and non-human identities.
"Amid the excitement of embracing the next wave of generative AI, companies are moving quickly to deploy agentic use cases, often overlooking the critical need to secure these systems and control the sprawl of non-human identities," says Arnab Bose, Chief Product Officer of the Okta Platform at Okta.
"By bringing these identities into the identity security fabric," Bose adds, "the Okta Platform can help organizations secure the rising digital labor force with the same rigor and vigilance as the human workforce."
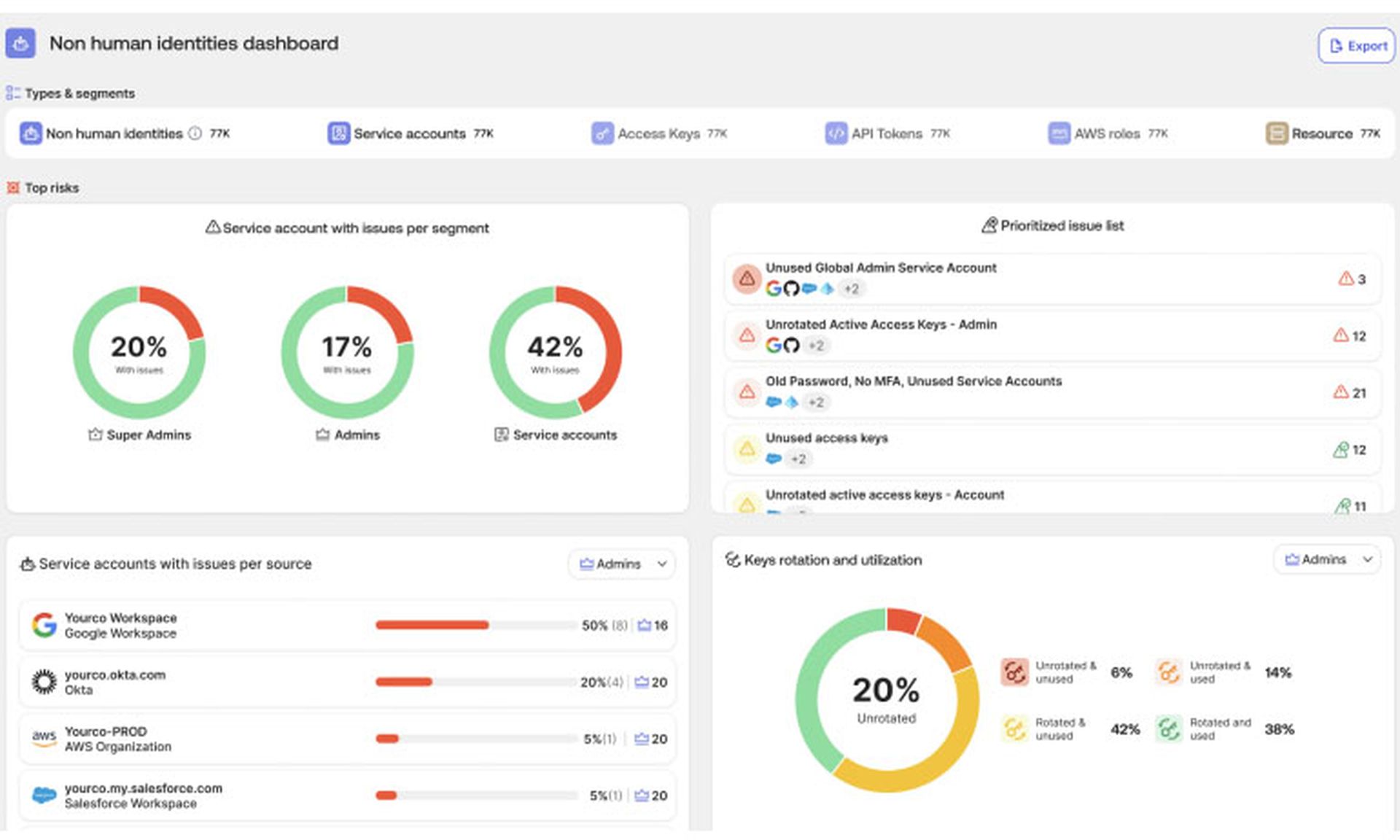
How Okta deals with NHIs
Recent additions and enhancements to the Okta Platform, previously known as Okta Workforce Identity, are specifically aimed at handling NHIs.
The Okta Privileged Access function, for example, now makes sure that NHIs have zero standing privileges, meaning that a non-human identity will get access credentials only when necessary, and those credentials will be revoked after a period of time according to client company policy.
Okta Privileged Access also manages NHI passwords, limits access to secrets such as passwords and API keys, rotates those secrets and audits access logs. It applies risk-based governance to NHI accounts, including by reducing privileges if it determines that an account has too many.
Okta Identity Security Posture Management is similarly being enhanced with the ability to continuously monitor NHIs and spot risks such as unrotated API keys, gaps in the implementation of MFA, and credential misuse among machine identities.
Okta has for some time offered Secure Identity Integrations that allow quick meshing of Okta Platform functions with Salesforce, AWS, Zoom, Office 365, Google Workspace and dozens of other SaaS services. Now, these integrations are being offered as a collection so that clients won't have to individually add them.
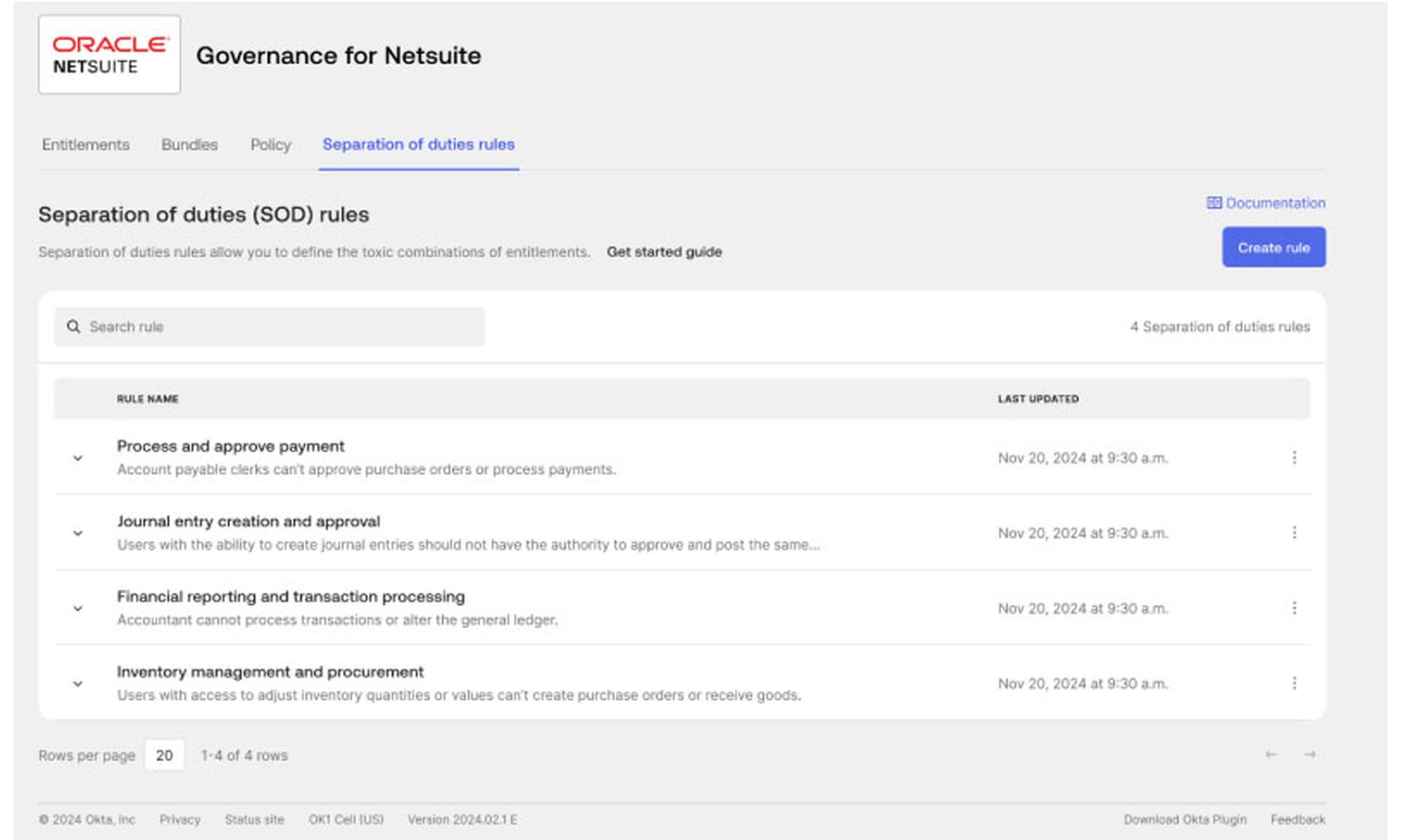
An entirely new feature is Separation of Duties. Part of Okta Identity Governance, it makes certain that users, non-human or otherwise, can't build up contradictory access permissions that might create compliance or security problems.
Also new are Secure Device Features, now part of Okta Device Access. These implement context-aware, dynamic MFA for smartphones, laptops and other remote devices, challenging users to provide supplementary authentication factors depending on device location, time of day, IP address and other bits of information that may seem unusual for a particular user.
Finally, there's Okta On-Prem Connector, which does for on-premises applications what Secure Identity Integrations does for SaaS. It lets Okta clients set up Okta Identity Governance to manage and monitor locally housed programs and features.
The tide of non-human identities flooding workplace identity-management systems won't be receding any time soon. But implementing modern identity systems like the Okta Platform makes sure that your organization can stay afloat.
Screenshot credits: Okta