Organizations seeking to strengthen their information-security posture must tackle one of the leading causes of breaches and data loss: admin sprawl, or the granting of unnecessary administrative permissions to user accounts.
Nearly 75% of cloud breaches and other cloud-related security failures stem from poorly managed identities and access permissions, a recent Gartner report found.
Meanwhile, identity and access management (IAM) provider Okta found that among its customers, 25% of "super admin" accounts — those with administrative rights over an organization's entire network — were not used to perform any administrative tasks for periods of 45 days or longer.
As Okta states in its Guide to Tackling Admin Sprawl, employees routinely "hold more and higher access and permissions than they need to perform their job — without realizing the threat this could pose to the organization's security posture."
What is admin sprawl?
Administrative sprawl is closely related to two other concepts, "access sprawl" and "identity sprawl." The terms are sometimes used interchangeably.
However, identity sprawl may be better defined as too many people within an organization having too many individual accounts with different usernames and passwords. For example, Jane Smith might have one set of credentials for her network access and email, but other sets of credentials for each of the four SaaS tools and software packages she uses as part of her job.
Admin sprawl, on the other hand, isn't a question of too many accounts and sets of credentials existing overall. It's a question of too many legitimate user accounts having unnecessary admin permissions. It's especially bad when IT supervisors aren't aware of all the admin permissions that accounts may have.
Access sprawl encompasses both admin sprawl and identity sprawl: too many accounts having too many permissions, with sloppy tracking and monitoring of those accounts and their permissions.
Inadequate access management of any kind indicates a weak security posture, but admin sprawl specifically creates certain risks:
- It increases the potential impact of a successful account takeover. The greater the share of an organization's total userbase with admin permissions, the greater the likelihood that an intruder will happen to take over an admin account.
- Unsupervised or undocumented admin accounts may in turn grant admin rights to more users, often without the knowledge of IT supervisors, making a bad problem even worse.
- If admin accounts are unmonitored or undocumented, that may place the organization in potential noncompliance with industry rules and regulations.
"It is increasingly important for permissions to be aligned with the right users and, ideally, be aligned to specific [i.e., limited] timeframes," states the Okta guide, "as this allows organizations to maintain compliance with regulations like SOC 2, NIST-800, and SOX."
How to combat admin sprawl
Fortunately, there are some simple, if sometimes arduous, steps that your organization can take to rein in admin sprawl and make sure its security posture is shipshape.
1. Review all user accounts, and revoke admin rights from those with unnecessary admin permissions.
This will require a company-wide account audit. Depending on the size of your organization, you may want to consider licensing account-discovery scanning tools or implementing a full-fledged IAM platform. You may also need to convince some users, especially those who may rank high in the company, that it's in the company's best interest that their admin privileges be taken away.
2. Implement policies that incorporate role-based access controls and the principle of least privilege.
It's very simple: No user should have any more access permissions or privileges than that user needs to perform their job. Unnecessary permissions should be taken away. If a user takes on a new role within the organization, the user's permissions and privileges should be adjusted accordingly.
3. Determine the proper number of admin and super-admin accounts for your organization.
You should not have many employees who have even limited admin privileges, and you should have even fewer who have total control over the network.
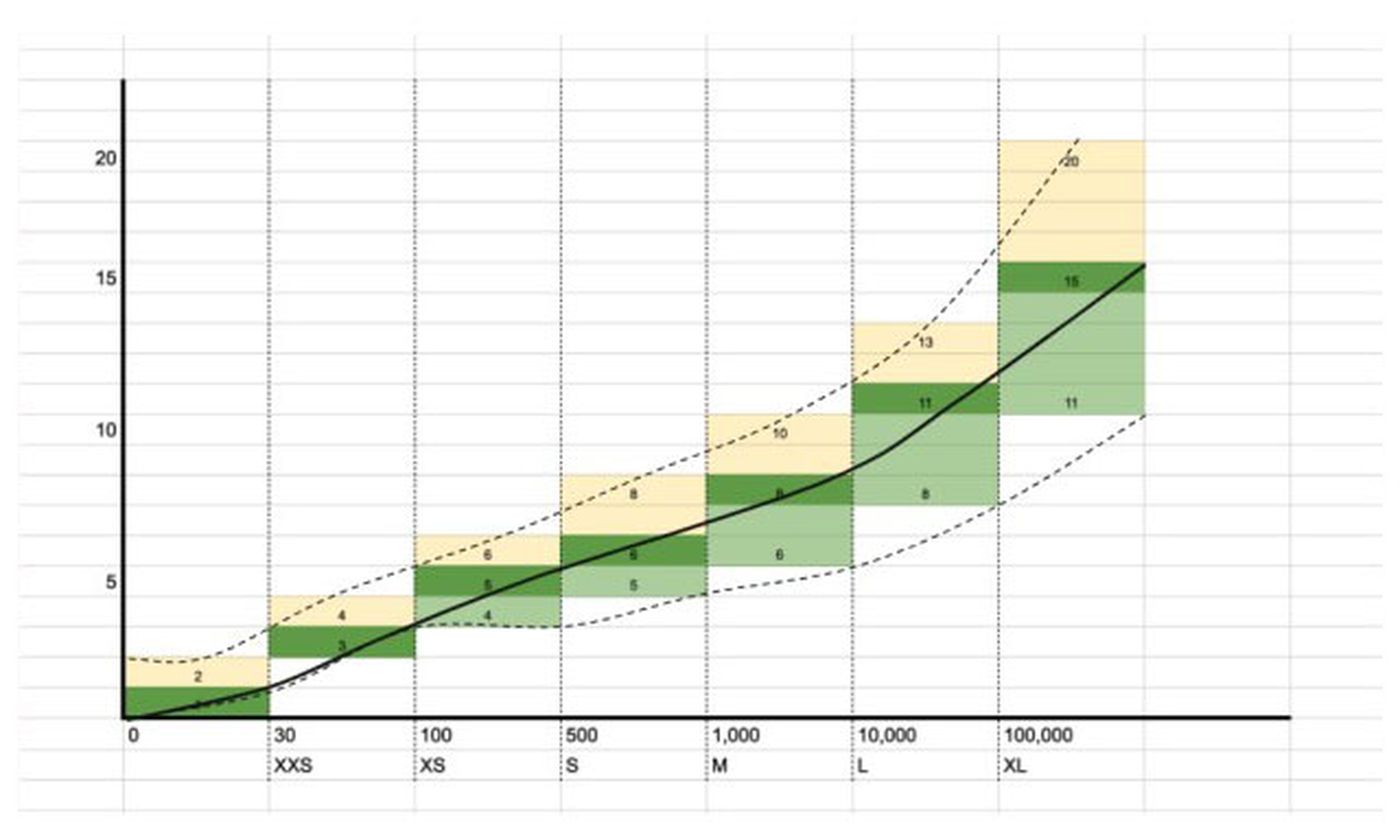
For a company of 100 people, four to six super-admins might be about right, according to statistics compiled by Okta from analyzing its clients. The proportions get smaller as the organizations get larger, with a company of 100,000 people perhaps needing between 11 and 20 super-admins.
4. Set up automated monitoring and policy enforcement.
Your strict new policies won't have teeth if IT and security staffers must manually and continually check each user's privileges and permissions. Instead, license or purchase an IAM solution that can check privileges and lay down the law on its own.
5. Mandate training sessions for admins.
Every user wants admin rights, whether it's to access Facebook or to set up a cloud instance to crunch numbers. You need to keep the numbers of admins small, and you need to drill proper policies and guidelines into those admins to, as the Okta guide puts it, "ensure they understand the responsibilities and risks associated with their roles."
Two possible additional steps might be to:
6. Implement just-in-time (JIT) access for especially sensitive tasks.
This policy grants extensive admin rights to an individual user for just enough time to get a certain job done, and then takes those admin rights away.
For example, an admin may need to rebuild a cloud database. JIT access will make sure that they get rights to alter the database only for the amount of time estimated to perform that task. Automated IAM platforms can implement and enforce JIT access smoothly.
7. Implement a privileged-access-management (PAM) solution.
The regular access-management solution that handles all users may not be robust enough to enforce role-based access controls, take away permissions according to the principle of least privilege, or manage JIT access. A dedicated PAM solution may be the answer, although modern IAM platforms like Okta's Workforce Identity Cloud often include PAM controls.
"Managing admin sprawl is a crucial part of maintaining security, cost efficiency, and compliance within any organization," the Okta guide states. "Taking proactive steps to assess and optimize admin utilization, implementing role-based access controls, and building a culture of continuous monitoring and training can significantly reduce the risks associated with excessive permissions and access."




