(A preview of the SC Media eBook “All about MDR: What it is and how to optimize it.")
Many security teams recognize the importance of employing skilled threat hunters to find and eliminate malicious cyber activity. The problem, however, is that it can be just as difficult to find the hunters themselves as the threats they seek to remove.
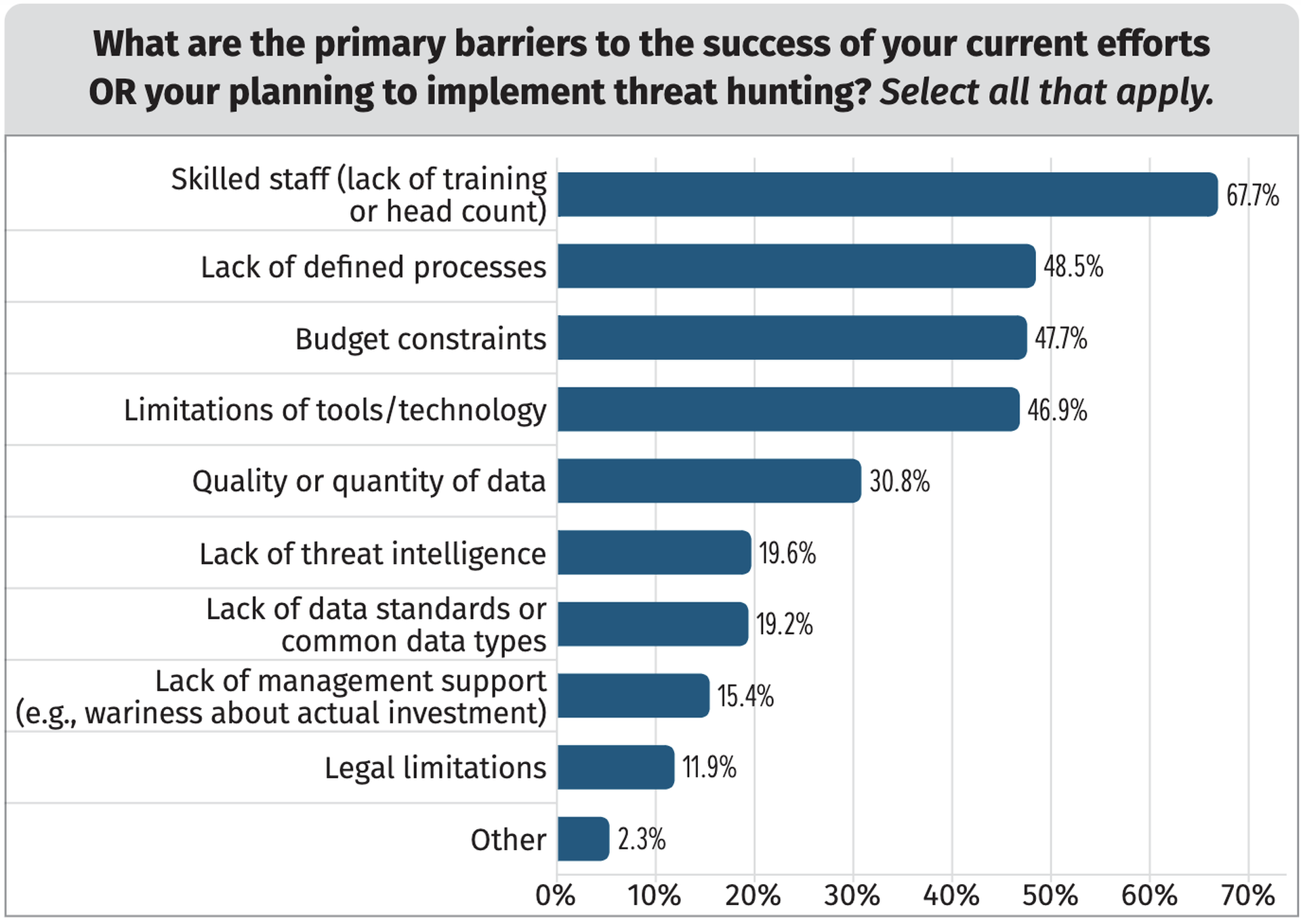
That’s due to an ongoing shortage in cybersecurity expertise across the industry which has left many SOCs short-staffed and overwhelmed by unsustainable alert volumes and increasingly sophisticated ‘red line’ attacks on critical assets. In a 2022 survey conducted by SANS Institute, 68% of security respondents cited a lack of skilled staff and training as a barrier to their organization’s threat hunting agenda, far outpacing other noted obstacles like ill-defined processes (49%) and budget constraints (48%).
It may take years before the supply of cyber talent finally meets the market’s demand, but in the meantime organizations have a powerful threat hunting ally at their disposal in managed detection and response, or MDR.
How MDR solves the threat hunting dilemma
MDR is an agreement whereby a cybersecurity vendor performs dedicated threat hunting investigations, monitoring and incident response on behalf of a customer organization. While there’s many benefits and use cases for working with an MDR vendor, the list below is concerned specifically with how MDR can deliver threat hunting “muscle” to an organization.
#1: Access to expansive network of professional threat hunters
One of the biggest draws to working with an MDR vendor is that customers gain coveted access to threat hunters without having to recruit and retain such talent themselves. Threat hunters are an elite class of cybersecurity professionals, having accrued years of experience in studying the advanced tactics, techniques and procedures (TTP) employed by both ransomware gangs and lone wolf attackers. Because of their niche reputation and supply of best-of-breed security tools, MDR vendors have the clout to attract threat hunting talent that most other organizations lack the budget to compete for.
“The expertise, the mentorship, and the exposure to working on the kind of stuff we work on is just a lot harder for organizations to do internally if they don't have the time and resources to commit to it,” says Mat Gangwer, Vice President of Managed Threat Response at Sophos. “But we have entire programs built up within our team on how we get people through this process.”
#2: Continuous threat coverage
Cybersecurity threats don’t take weekends or holidays off, but employees do. This puts small or short-staffed organizations at considerable risk since they’re often unable to provide the 24/7 continuous monitoring that’s needed to discover and eliminate well-orchestrated threats. Generally speaking, MDR providers don’t have that problem. Sophos, for example, has offices around the world, allowing anyone in their customer network to draw assistance from a global community of professionals who are active at all hours of the day. And because of this sprawling geographic footprint, critical threat intelligence (such as a newly discovered vulnerability) can be reported and rapidly distributed across the entire client network to fix that vulnerability wherever elsewhere it may exist.
“Something bad doesn't have to happen to you to get the benefit of the global footprint of the provider you're working with,” says Gangwer. “That’s a benefit in terms of having a large customer base in different regions, because different geographies get targeted with different sorts of attacks.”
#3: Rapid response and remediation
Discovering threats is one thing, but acting on them is the critical component. MDR follows through on the nature of threat hunting as a proactive, action-oriented discipline. Depending on a customer organization’s hunting maturity, providers of MDR services can scale their working relationships accordingly with regard to response and remediation procedures — from managing full-fledged response on behalf of the customer, to working hand-in-hand with the in-house team on managing response, to a minimalistic approach of alerting the in-house team when threats are discovered and providing remediation guidance. The flexibility of this system means that organizations can modify their level of MDR dependency as they mature and develop threat hunting vigilance.
#4: Improved analytics and threat assessments
MDR allows organizations to make sense of the security alert maelstrom bombarding their SOC daily. Drawing from their pool of expertise, providers can give customers insights about their attack surface and routine updates on the latest vulnerability data collected by its teams of experts stationed around the world. Over time, the steady stream of insights can help organizations identify their persisting weak points and identify actions that can eliminate these weaknesses. In addition, organizations may discover IT assets and potential entry points they didn’t even know they had.
#5: Redirect personnel to focus on improving cyber hygiene and security posture
Dedicated MDR threat hunting means that in-house SOC personnel can devote their attention to strategic, business-focused problems beyond the day-to-day detection and response. By outsourcing responsibility of these items to the MDR provider, an organization can better allocate existing resources, redirect budget and personnel towards improving long-term cyber hygiene and strategy, and focus more generally on less-intensive cybersecurity management and administration.




