About this series
In 2023, the cybersecurity landscape changed in three significant ways. The Securities and Exchange Commission cut the allowed reporting period following a security breach to just four days. Artificial intelligence began to be used in cyberattacks. And after retreating in 2022, ransomware came back stronger than ever.
In response to these threats, cybersecurity buyers, vendors, influencers and decision makers worked to improve their practices around ransomware prevention, privacy and third-party risk, vulnerability management, cloud security, and identity and access management. Yet respondents in several CyberRisk Alliance Business Intelligence surveys reported more than a few challenges in meeting these goals.
The following is the second of a five-part series about how security practitioners struggled or, in some cases, made significant headway throughout 2023. Here, we focus on the risks posed to privacy and security by third-party software and vendor relationships.
Download the full report, 2023 Year in Review.
***
The health-care sector dominated the bad news about third-party applications in 2023, as breaches of patient information made headlines, U.S. federal regulators beefed up enforcement and legislators took notice of high-profile privacy violations.
The Federal Trade Commission fined digital-health provider BetterHealth $7.8 million, online-prescription service GoodRx $1.5 million, and fertility app Premom $100,000 for sharing patient information with Facebook, Google and other advertisers.
U.S. senators questioned three other telehealth providers about similar allegations. One, Cerebral, admitted sharing the data of about 3.2 million patients with third parties. Along similar lines, the FTC moved in June to update its Health Breach Notification Rule so that developers of healthcare applications would be required to post notifications of data breaches.
But the breaches kept coming. In July, data of 11 million patients was stolen from HCA Healthcare after email-formatting software was compromised. In October, medical transcription service provider Perry Johnson & Associates said 9 million patients had had their information compromised.
A study found that 99% of hospital websites used tracking code that funneled patient data to third parties, and the U.S. Department of Health and Human Services said many health-care organizations were still struggling to comply with HIPAA's Security Rule, despite the fact that the rule had gone into effect 17 years earlier.
The supply kill chain
The SolarWinds supply-chain hack of 2020, which in October led the SEC to charge the company CISO with fraud, seems to have inspired North Korean state-sponsored hackers. Over the course of 2023, Pyongyang was tied to supply-chain hacks of 3CX VoIP software, of the JumpCloud cloud-directory-provider, of the Zoho ManageEngine ServiceDesk, of VMConnect, and of CyberLink media-playing software.
Ironically, SolarWinds’ charges had nothing to do with reporting time, and the company would likely have met the new SEC four-day notification deadline had the attack taken place in 2024. (The SEC alleges that SolarWinds told investors its systems were secure even as it knew of many unresolved security issues.)
Publicly traded companies, especially those in the healthcare industry, will need to keep the new SEC reporting rules, along with the more stringently enforced FTC regulations, in mind going forward.
The North Korean supply-chain attack on CyberLink was made possible by malicious Python packages placed in the online repository PyPI. It was one of several such supply-chain attacks involving open-source software. In February, 15,000 phishing packages were found in the NPM repository, and so many spam packages were uploaded to NPM in April that the repository briefly went offline.
Supply-chain attacks on GitHub involved "repojacking," or taking over abandoned usernames, along with old-fashioned typosquatting to lure users to deceptively named tools. Fake vulnerability exploits and fake proofs of concept on GitHub spread malware to security researchers and wannabe black-hats alike.
The widespread availability of code-writing AI tools like Microsoft’s Copilot, already part of GitHub, raised the stakes of third-party software security. AI can “hallucinate” the existence of imaginary code libraries in public software repositories, creating blank slates into which attackers can sneak malicious code through “hallucination squatting.”
Misplaced trust
Fifty-seven percent of all respondents to a January 2023 CRA Business Intelligence survey of 209 IT and security professionals in the U.S. said their organizations had suffered a security incident or data breach related to a third-party partner in the previous 24 months. Fifty-two percent of those said that the attack stemmed from a software vendor.
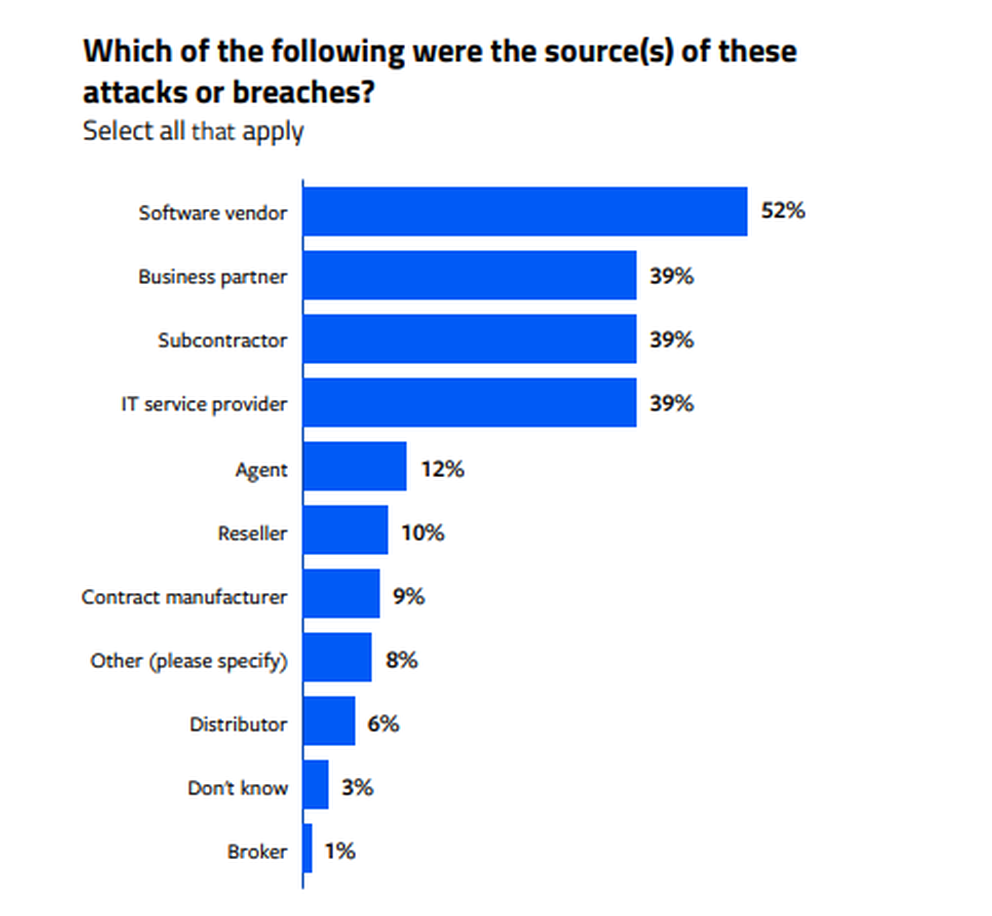
Third-party software vulnerabilities were seen as the gravest threat posed by third-party relationships, with 60% of respondents rating them between 5 and 7 on a 1-7 scale of potential risk.
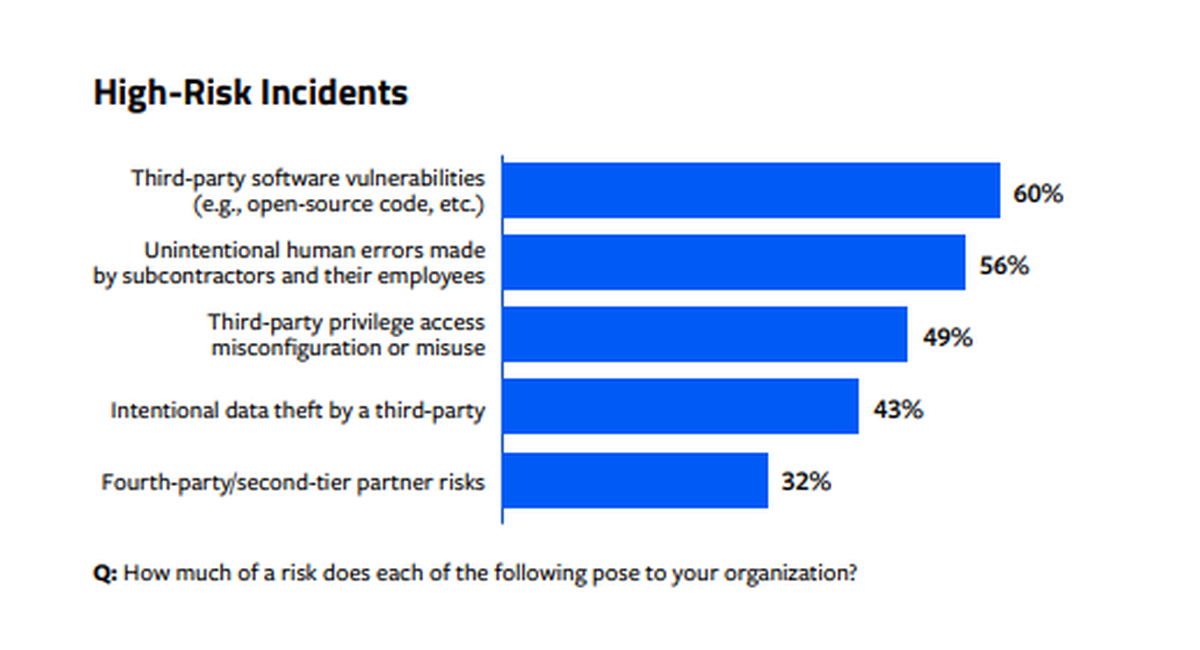
"The third-party ecosystem has become complex, and the open-source software system has been attacked and is an easy target," said one survey respondent. "Without having clear visibility into the remediation process, it poses a big risk."
2024 to-do list:
- If you're a for-profit healthcare provider, plan for tougher FTC enforcement of data-breach rules (non-profit providers are regulated at the state level).
- Perform risk assessments of third-party software and third-party vendor relationships.
- Consider using a software bill of materials (SBOM) to keep track of third-party components.




