About this series
In 2023, the cybersecurity landscape changed in three significant ways. The Securities and Exchange Commission cut the allowed reporting period following a security breach to just four days. Artificial intelligence began to be used in cyberattacks. And after retreating in 2022, ransomware came back stronger than ever.
In response to these threats, cybersecurity buyers, vendors, influencers and decision makers worked to improve their practices around ransomware prevention, privacy and third-party risk, vulnerability management, cloud security, and identity and access management. Yet respondents in several CyberRisk Alliance Business Intelligence surveys reported more than a few challenges in meeting these goals.
The following is the last of a five-part series about how security practitioners struggled or, in some cases, made significant headway throughout 2023. Here, we focus on identity and access management and why organizations feared disrupting the user experience.
***
Many of the top identity and access management stories of 2023 involved Okta, and not in a good way. The widely used cloud-based IAM provider revealed in November that attackers had two months earlier compromised an employee's Google account, letting the attackers steal credentials to an Okta service account. That in turn let them obtain administrative session cookies for Okta clients, including BeyondTrust, Cloudflare and 1Password, and possibly the contact information for every user of Okta's main customer-support system.
You never want your own company to become the focus of an Enterprise Security Weekly podcast with a title like "Five Lessons Learned From Okta's Customer Support System Breach."
Earlier in September, Okta clients found themselves targeted by a social-engineering campaign, attributed to the Scattered Spider aka Oktapus ransomware crew, that tried to cajole service-desk technicians into resetting MFA settings of Okta super-administrator accounts. This wasn't Okta's fault, and few of its clients fell for the ruse, but two very big ones did: gambling-industry giants MGM Resorts International and Caesars Entertainment.
The MGM hackers’ avenue of attack was the telephone, but social-engineering attacks in 2024 may use artificial intelligence to rapidly mount and manage phishing, vishing and business email compromise campaigns. It might not be long before AI bots keep potential victims on the hook with extended email, instant-messaging, or even voice-based conversations, akin to “pig butchering” scams that can take weeks to “fatten up” the target.
The drip-drip-drip of revelations stemming from a single Okta breach might not fly well with an SEC seeking to enforce its new four-day reporting rule. Clients of IAM providers should look into stopgap solutions should their providers be similarly compromised. If the clients are publicly traded, they should be ready to quickly report their own resulting breaches to the SEC.
Not an isolated incident
If it's any consolation to Okta, Microsoft in September had 38 terabytes' worth of its private GitHub data exposed, thanks to an abused shared access signature (SAS) token. The compromised data included 30,000 Teams messages, capping a summer of woe for Microsoft's messaging platform.
It began with the July release of a red-teaming tool called TeamsPhisher, which lets you send files directly to a Teams user from outside the user's organization's network, exploiting a vulnerability that Microsoft said it doesn't plan to patch. That led to a spate of phishing attacks on Teams users.
Teams was also hit hard by the Russian state-sponsored attackers Cozy Bear, the DarkGate malware crew and a broader Microsoft-services attack by Chinese state-sponsored hackers who had found a private encryption key in a crash-dump file stored on a Microsoft engineer's computer. None of those attackers seemed to be using TeamsPhisher.
For a bit of good news, the passwordless "passkey" system developed by Apple, Google and Microsoft became widely available in 2023 and was the hot topic at Identiverse 2023. In May, Google made passkeys an option for user accounts and then for enterprise users; by the autumn, GitHub, 1Password and WhatsApp had followed suit.
User-experience concerns hamper efforts to move past passwords
In a CyberRisk Alliance Business Intelligence survey of 203 security and IT managers in North America, conducted in December 2022 and January 2023, 44% of respondents said that their organizations had at least partly implemented IAM solutions, and 26% were considering one. Of those who had moved ahead with IAM, roughly equal numbers went with on-premises, cloud-based or hybrid deployments.
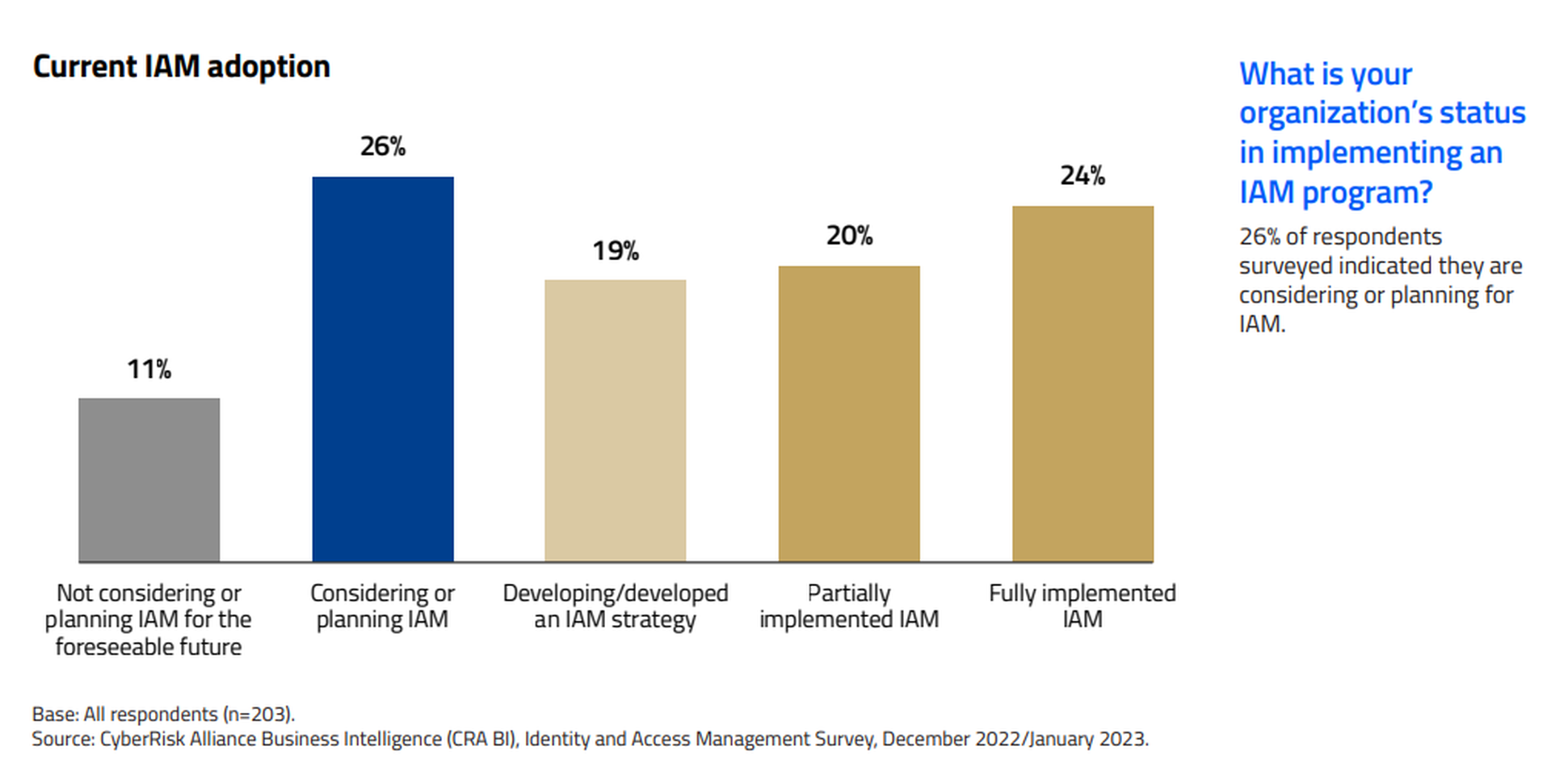
However, along with endpoint security and remote access, IAM implementers were concerned about the user experience, a constant worry with IAM deployments. Fifty-six percent of survey respondents said they were "currently focused" on the user experience, and another 32% said they were planning to focus on it.
Hesitation to take users into unfamiliar territory may explain why even as 82% of respondents said their IAM programs enforced unique user passwords, less than one-third of respondents said they used a more advanced authentication method such as biometrics, pre-shared keys or behaviors.
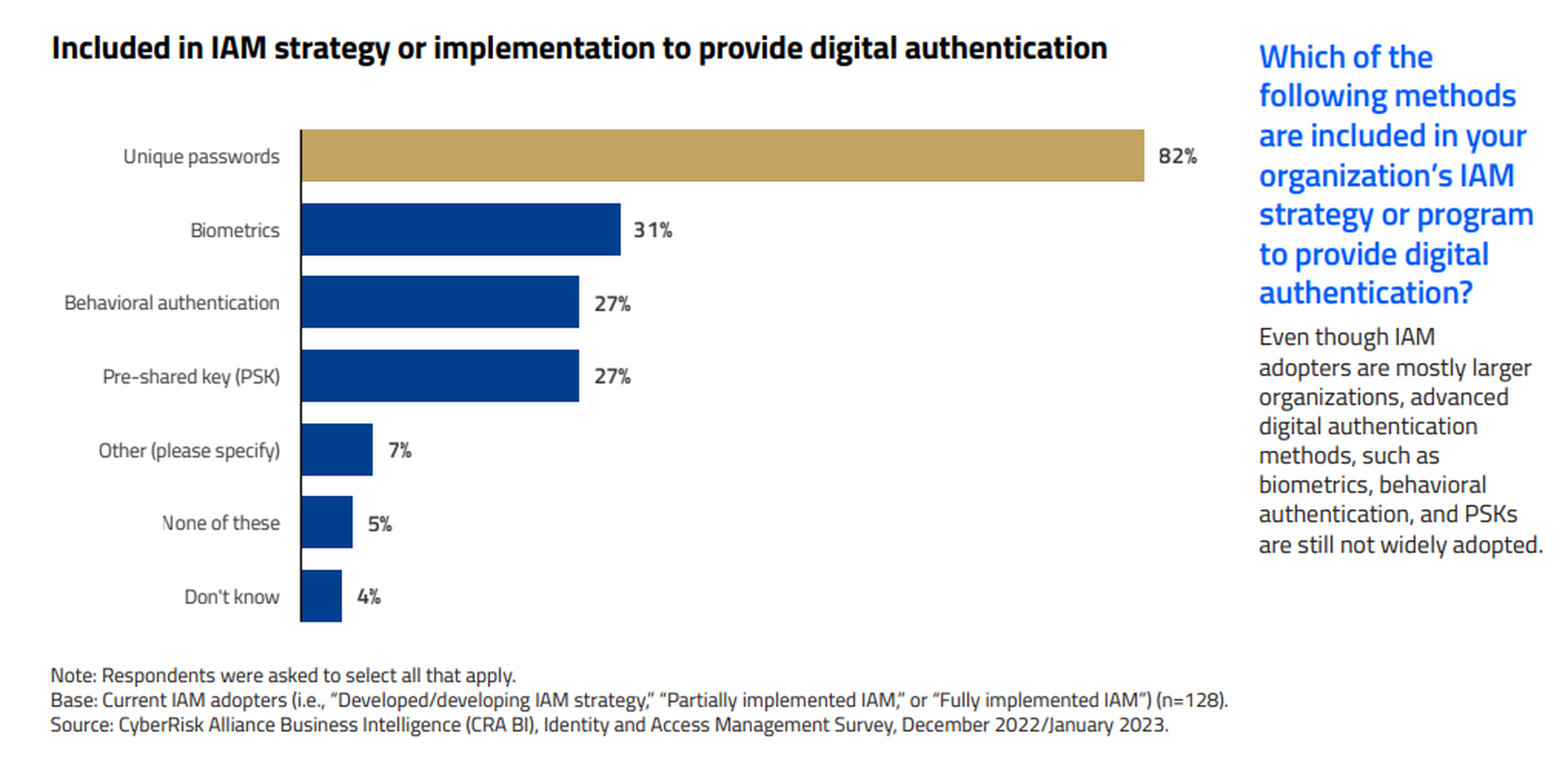
"Who wants to spend hours in understanding a product that always requires additional expertise to handle when its objective is to provide efficiency?" asked one respondent.
Another said that "not disrupting the end user is difficult and requires more people than we currently have devoted to the project."
2024 to-do list
- Look into mandating passkeys for high-privilege administrative personnel and executives.
- Create internal “fail closed” procedures in case your external IAM provider is compromised.
- Keep the user experience in mind when implementing new IAM procedures, but don’t let it hamper progress.




