Discussion Topics
In today’s complex cybersecurity landscape, CISOs are tasked with building and maintaining tool stacks that not only defend against evolving threats but also drive efficiency and resilience. However, the strategic selection and optimization of these tools is far from straightforward. Common challenges, such as vendor sprawl, sunk cost fallacy, and automation bias, often complicate the decision-making process, leaving organizations vulnerable to inefficiencies and blind spots.
Vendor sprawl, for instance, leads to the accumulation of tools from various providers, which can create integration difficulties, increase complexity, and strain cybersecurity teams. As organizations invest in tools over time, the sunk cost fallacy can prompt them to stick with outdated or underperforming solutions, sidelining newer, more effective alternatives. Similarly, automation bias can cause security teams to over-rely on automated systems, missing critical oversight that human intervention could provide.
Psychological barriers like groupthink and confirmation bias further complicate the situation. Groupthink may stifle diverse viewpoints, leading teams to overlook innovative approaches or superior tools. Confirmation bias can narrow the focus to evidence that supports current beliefs, reinforcing the status quo at the expense of emerging threats or better-suited technologies.
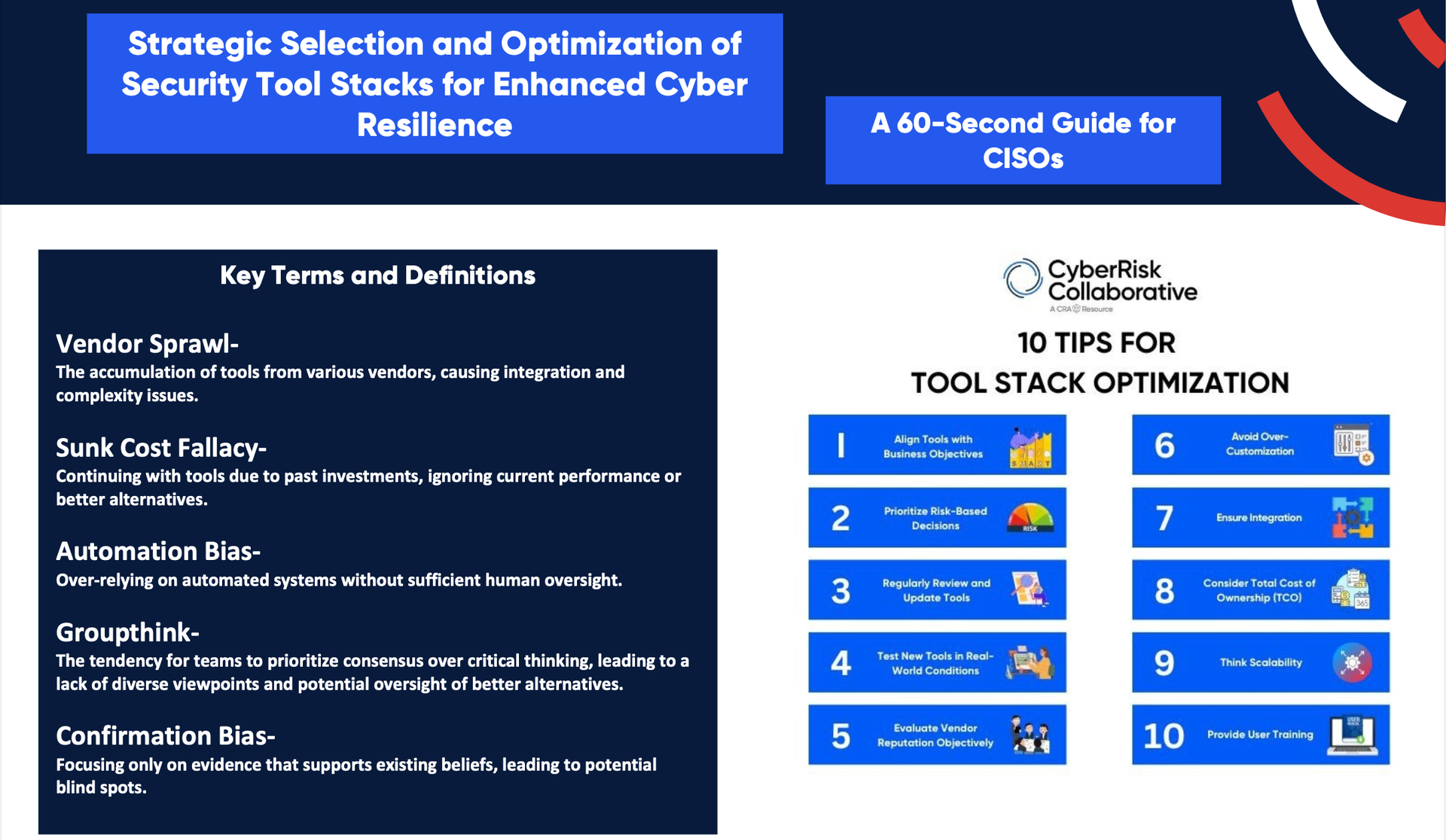
To address these issues, this guide provides 10 actionable tips for tool stack optimization, empowering CISOs to make strategic choices that not only reduce complexity but also bolster cyber resilience. By carefully evaluating existing tools, leveraging diverse perspectives, and maintaining a balance between automation and human oversight, organizations can streamline their security operations and ensure their defenses are future-ready.