You’ve been hearing it every January for the last decade: The coming year will see a continued escalation of ransomware attacks. But these past 12 months have been different.
Ransomware gangs have taken their attacks to a dangerous new level in recent months, targeting ubiquitous software used by business, government agencies and critical infrastructure and revealing multiple vulnerabilities in the software supply chain.
Among them was the SolarWinds attack, discovered this time last year. In May, a ransomware attack crippled the Colonial Pipeline for nearly a week, sending millions along the U.S. East Coast scrambling for gas. Also in May, the JBS meat packing company, which supplies more than one-fifth of all beef in the United States, was forced to halt operations after its plants were pushed offline. In July, the networks of at least 200 U.S. companies were paralyzed when the REvil ransomware syndicate attacked software supplier Kaseya.
SophosLabs, the Sophos Managed Threat Response team and the SophosAI data science group have been helping their customers fight such attacks throughout 2021. Their response is covered in detail within the 2022 Threat Report Sophos released in November.
The report represents the collective wisdom of Sophos’ malware analysts, the machine and network forensics specialists and machine learning experts that make up these core teams within the company and offers analysis of the events that transpired in 2021 and how those events will help shape the threat landscape in 2022 and beyond. It’s organized into five parts:
- The ransomware epidemic and its aftermath
- Trends in conventional malware that targets Windows computers
- Malware on mobile platforms
- Security threats to infrastructure
- Artificial intelligence and how it applies to the practice of information security
Key takeaways
- Ransomware accounted for nearly 80% of Sophos Rapid Response’s engagements, followed by attacks involving Cobalt Strike (6%), Mac malware (5%), web shells (4%), data exfiltration (3%) and crypto miners (3%).
- The Conti and REvil ransomware families pioneered and developed the ransomware-as-a-service business model, where a small team of developers built the ransomware itself, and a larger group of affiliates acted as the delivery mechanism, actively breaking into networks by any means available: brute-force attacks against internet-facing services; exploits of vulnerable software; and occasionally by obtaining legitimate credentials from initial access brokers, a type of criminal service provider.
- Tools like Cobalt Strike were most frequently a component of the kinds of hands-on-keyboards attacks preferred by ransomware groups.
- Threat actors take advantage of a wide variety of commercial software and utilities designed for IT administrators or security professionals.
Checklist
To reduce these ongoing threats, Sophos has been recommending that organizations:
- Ensure they have robust ransomware and malware protection in place
- Remain vigilant about emerging vulnerabilities on Internet-facing software products they operate on their networks.
- Shift some products to vendor-hosted software-as-a-service, which can mitigate some of these risks, as vendors typically patch vulnerabilities in their own deployments of software faster than they can be deployed by on-premises customers.
- Fully deploy malware protection on servers and endpoint devices
- Monitor products to catch attacks that trigger detections or alerts before an attacker with administrative access can defeat protections.
- Have effective data backup practices and business continuity plans, regardless of their size, to ensure that they can survive attacks.
Download the report here.
Article 2: Awaiting Josh Saxe commentary but here’s what I have so far:
The SOC of the future revolves around AI
Sophos Chief Scientist Josh Saxe explains how AI will lead to faster detection and response in the years to come.
By Bill Brenner
In the SOC of the future, artificial intelligence (AI) will anticipate operators’ intentions and suggest relevant actions to users. This approach will dramatically accelerate operators’ security workflows and, in turn, their ability to detect and respond to threats.
Sophos Chief Scientist Josh Saxe outlined the AI-driven SOC of the future at the Sophos Cybersecurity Summit earlier this month.
He started by clearing up some misconceptions, noting that many product marketing teams invoke AI to suggest their products have “some magic secret sauce” that improves their product in unspecified ways. Saxe said his argument is clearer and more direct: “We need to weave AI into the core of the security product user experience going forward. If we do that, we can dramatically enhance how it feels to use security products and dramatically improve outcomes in the real world.”
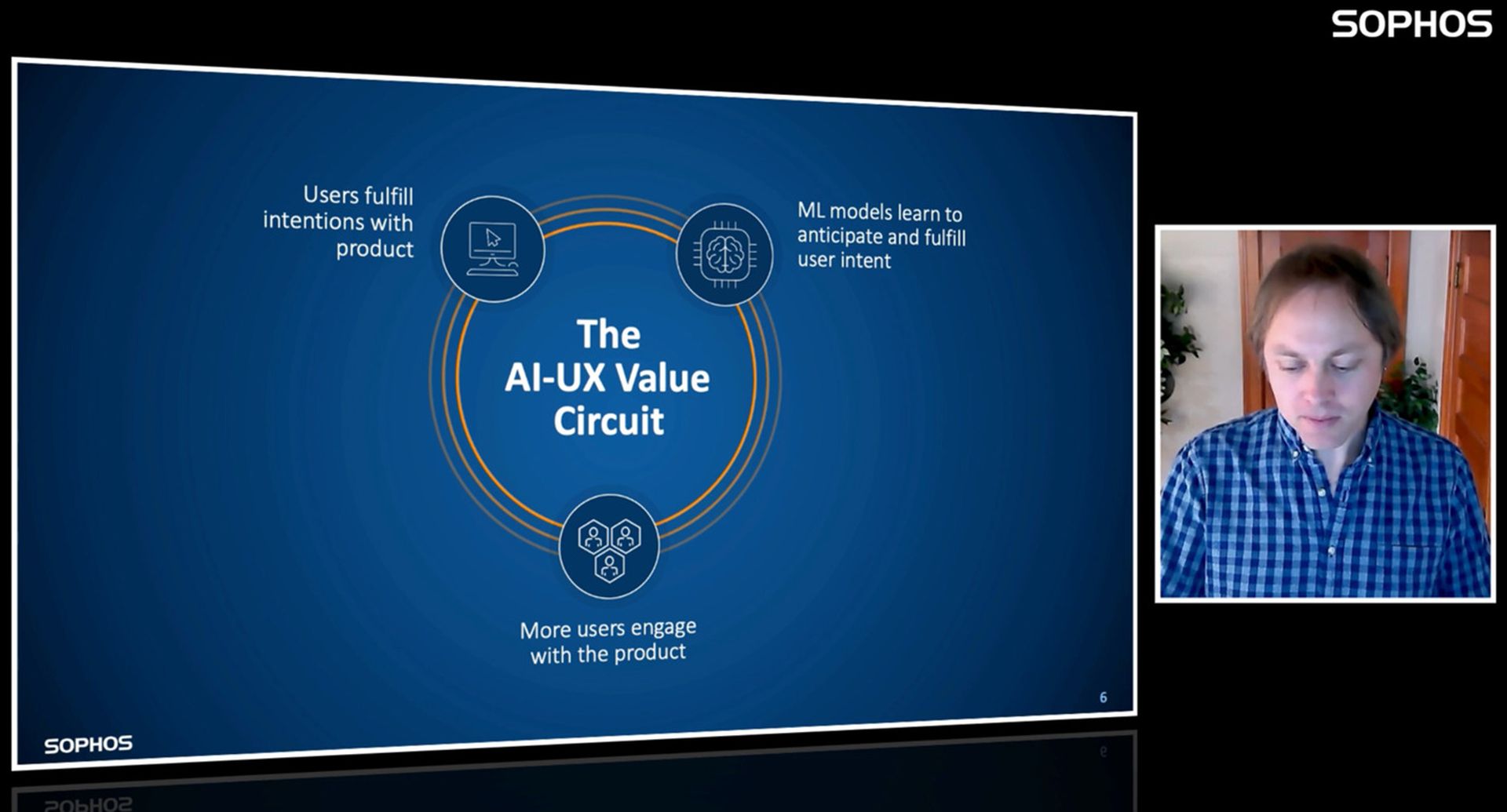
Sophos Chief Data Scientist Joshua Saxe explains the AI-UX Value Circuit that the AI-based SOC is built upon.
He explained what the Sophos data science teams are doing to turn this vision into reality and how AI -- trained on large-scale user-behavioral data -- will integrate into SOC workflows to elevate security and operator efficiency. He also explained how his team is leveraging the threat hunting and incident response expertise of Sophos SecOps to help deliver the AI-driven SOC.
The AI-driven SOC is built on four pillars:
- Alert recommendations
- Security data enrichment
- Incident remediation recommendations
- Workflow automation
“We’re not suggesting that AI will take over the job of SOC analysts in some Skynet fashion,” he said. “As users use adaptive products, machine learning models use the historical data to predict user intentions. Users like that because it makes their tasks easier. The core of our vision is built around the AI-UX value circuit, where users fulfill their intentions with a product, ML models learn to anticipate and fulfill their intent and, as a result, more users engage with the product.”
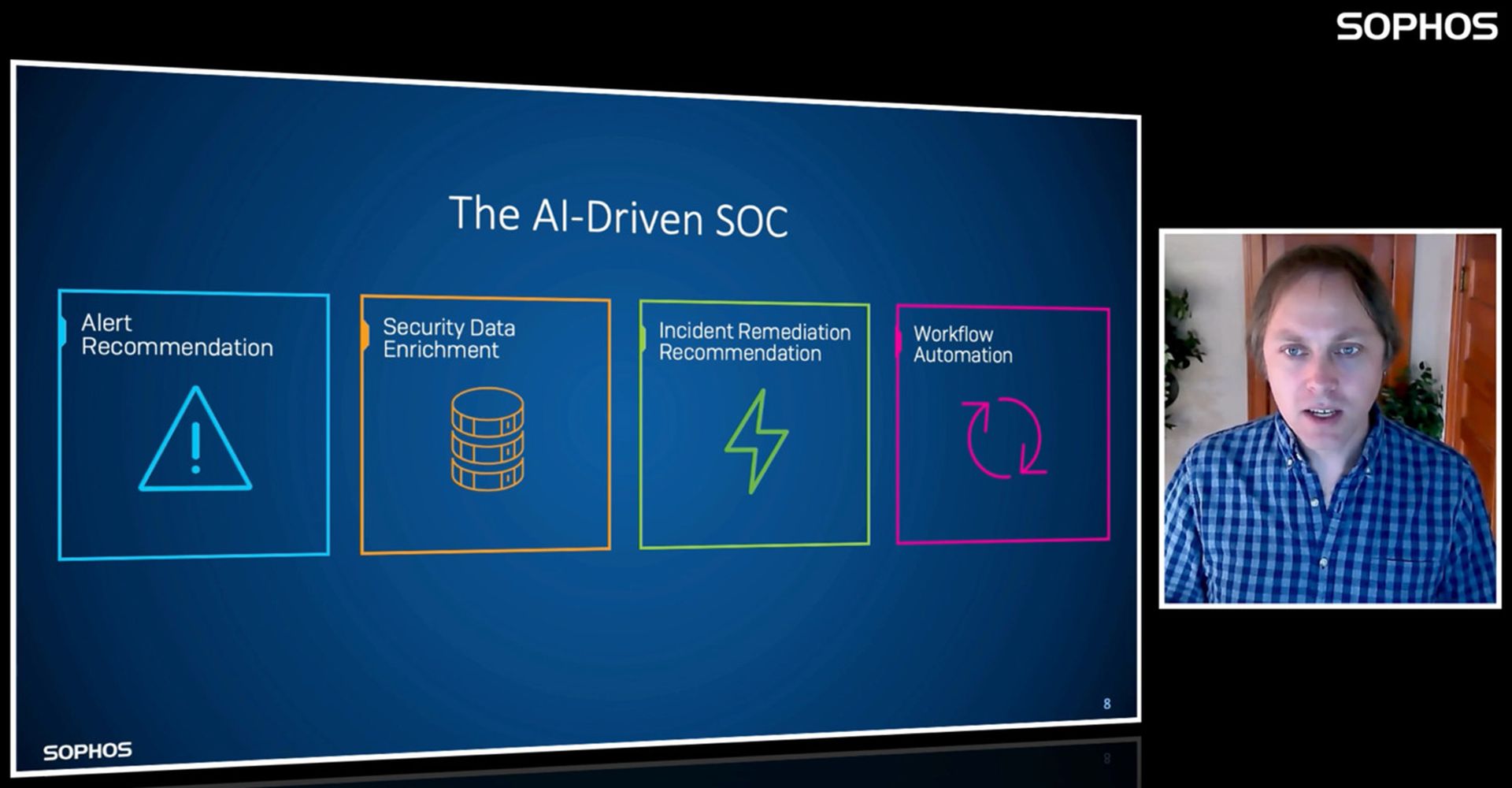
Pictured: The four pillars of an AI-driven SOC.
During the Summit, attendees answered live poll questions regarding their SOC programs. Over half of attendees said they have a SOC with 30% running an internal SOC and a similar percentage (26%) working with a third-party SOC. Within the SOC, alert triage is a key task for many human operators. Over half (54%) of poll respondents reported that their SOC team spends 10% or more of their time on triage, with almost a quarter (22%) spending 25% or more of their time on this activity.
Chris Kissel, research director at IDC, explored different ways that organizations can take advantage of machines and analytics to carry out what he called ‘SOC drudge work’. 20% of poll respondents are already using machines and analytics regularly or extensively to reduce the burden on human operators, while a further 28% are in the early stages.
Sophos has plowed considerable resources into building out AI security since 2017, when the company acquired Invincea to enhance its capabilities. Saxe joined Sophos as part of that acquisition.
Since then, the data science team has been working on several of the ingredients needed for that AI-powered SOC, including behavioral detection. Among them are advanced capabilities to detect malicious email, URLs and IP addresses.
The importance of AI in security is also a factor in Sophos’ 2022 threat report. Since the bad guys have increased their use of AI in their attacks, the good guys must use it to bolster defenses, the report authors wrote:
“In the 2020s, the mere fact that a vendor uses ML in a particular protection technology will not be noteworthy – it will be table stakes. The real question will be how effective companies’ AI detection solutions are, and what novel capabilities, outside autonomous detection workflows, security companies are developing with AI [which] will have tectonic implications for the security landscape. They will influence and shape the development of defensive security technologies, and the security community will identify novel applications for AI, as AI capabilities develop.”
Click here to check out Saxe’s talk along with others, and click here to learn more about Sophos AI and how it fits into security operations.



