

In February 2019, the Ponemon Institute conducted its The Value of Threat Intelligence: Annual Study of North American and United Kingdom Companies. Following is an excerpt from that extensive study, sponsored by Anomali. The importance of threat intelligence as part of an IT security mission should encourage organizations to take steps to improve how it is used. Following are recommendations to close the threat intelligence effectiveness gap:
- Establish a formal and dedicated team to manage threat intelligence activities.
- Allocate adequate budget to threat intelligence, including threat hunting and advanced
- attacker investigations.
- Participate in threat intelligence sharing.
- Participate in an ISAC/ISAO or other industry sharing group.
- Increase the security team’s knowledge about adversaries including their motivations, infrastructure and methods.
- Improve ability to integrate threat intelligence with their tools.
- Improve ability to integrate threat intelligence data with SIEM and IDS/IPS.
Ponemon outlines eight best practices for threat intelligence. These best practices are extrapolated from 198 respondents who self-reported their organizations as highly effective in detecting external threats.
- Adequate budget. Forty-one percent of high performing organizations have resources that focus on threat detection versus only 33 percent of respondents in the overall sample.
- Focused on improving the use of threat intelligence to detect threats. Seventy-two percent of respondents in high performing organizations rate their organizations’ use of threat intelligence data as part of its threat detection efforts as highly effective. In contrast, 41 percent of respondents in the overall sample rate their effectiveness as very high.
- Understand their adversaries. Virtually all high performing organizations want to understand the motivations, infrastructure, and methods of attackers.
- Pay for threat intelligence. Sixty percent of respondents say the primary source of threat intelligence is paid threat intelligence feeds. Twenty-three percent of respondents in the overall sample are more likely than high performing organizations to use open source threat intelligence feeds.
- Implement a dedicated threat intelligence platform. Sixty-nine percent of respondents in high performing organizations have a dedicated threat intelligence platform but less than half (48 percent) of respondents in the overall sample have this.
- Integrate threat intelligence with its SIEM and IDS/IPS with less difficulty than the overall sample. Eight-six percent of respondents in high performing organizations either integrate threat intelligence data from a threat intelligence platform (45 percent) or integrate built-in threat intelligence data provided by the SIEM vendor (41 percent). Eighty-one percent of these respondents say their organizations integrate threat intelligence with their IDS/IPS. High performing organizations also report that the integration with SIEM and IDS/IPS was not as difficult as the overall sample believes.
- Share intelligence with other organizations. Seventy-seven percent of respondents in high performing organizations share threat intelligence with other organizations versus 59 percent of respondents in the overall sample.
- Have a dedicated threat hunting team. Fifty-nine percent of high performing organizations have a dedicated threat hunting team. 43 percent of respondents in the overall sample.
A total of 1,098 IT and IT security practitioners in North America and the United Kingdom participated in this research. According to the findings, these participants strongly believe in the importance and value of threat intelligence data but are struggling to maximize its effectiveness in detecting cyber threats.
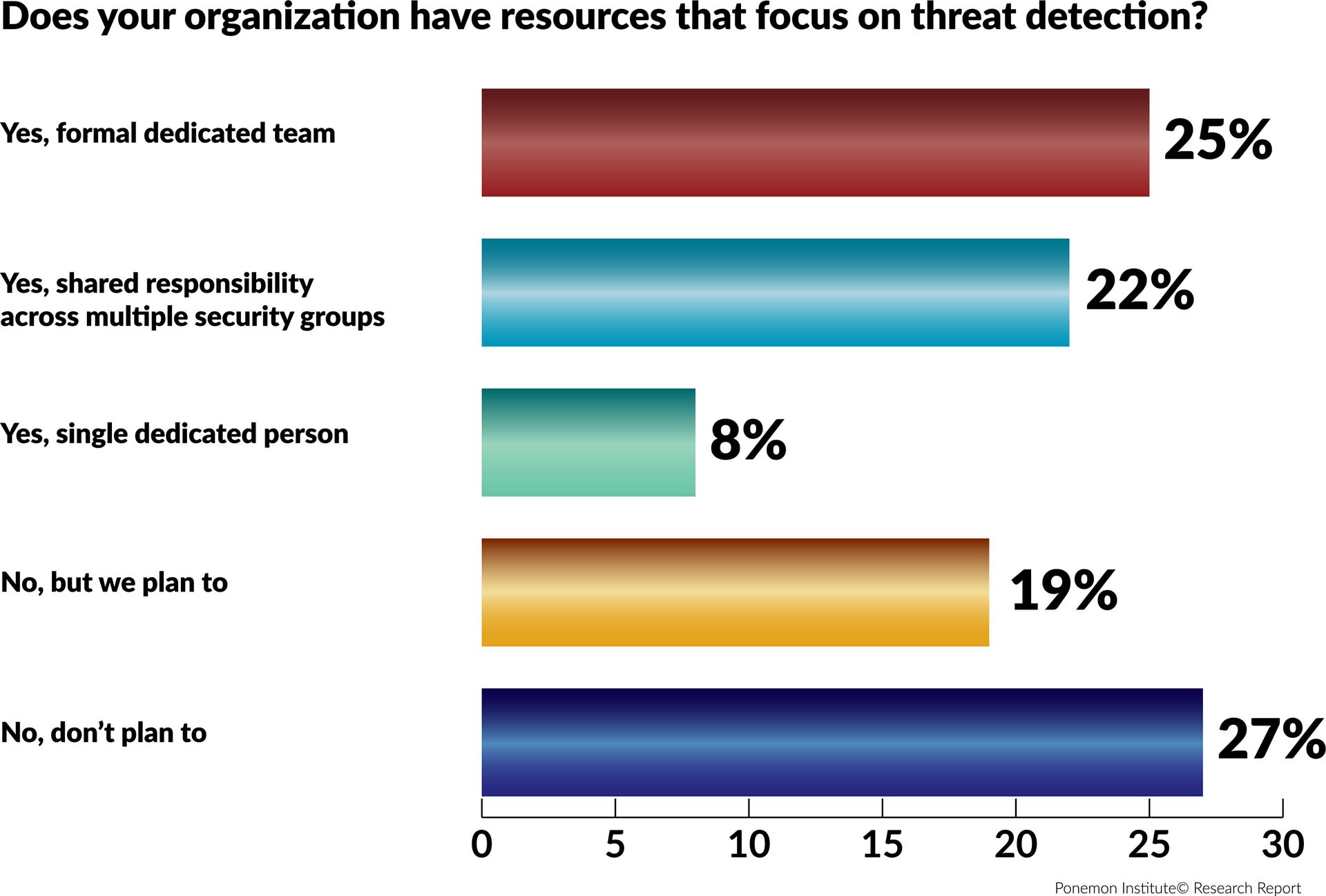
Most organizations say they have resources dedicated to threat detection. According to this figure, 55 percent of respondents say they have a dedicated team (25 percent), shared responsibility across multiple security groups (22 percent) or a single dedicated person (8 percent). However, 27 percent of respondents say their organizations have no plans to focus resources on threat detection. For more information, click here.



