
In 2022, security practitioners struggled to address the growing attack surface created by their rapid push to remote work and cloud-based operations during the previous two years. Cyber criminals exploited new vulnerabilities — including those introduced by the growing use of third-party software — to launch ransomware and other attacks.
But with tools like zero trust, XDR and more automated threat intelligence tech to bolster vulnerability management, cloud, email and endpoint security, organizations fought back – and established plans to invest more to secure networks and data in the next two years.
The following is the third of a seven-part series about where security practitioners struggled and, in many cases, made headway throughout 2022. Here, we focus on their email security challenges.
Click here to download the full 2022 Cybersecurity Year in Review Report from SC Media.
Consequences of email insecurity
Security teams devoted much attention to email security in 2022, but attackers continued to have the edge, exploiting the vulnerabilities that come with remote work and it’s the explosion of business and personal devices.
Consider the compromise reported by American Airlines in September 2022. The company informed customers that a bad actor breached the email accounts of some employees in July, which led to the personal information of customers and employees potentially being exposed and accessed.
Also in September, a credential phishing attack targeted 16,000 emails at a nonprofit agency. The fraudster in that incident claimed to be the prominent charge card brand American Express and demanded that cardholders open an attachment and contact the card company immediately regarding the cardholder’s account.
Such incidents demonstrate that email security is at its core a people problem, requiring security teams to address risks that can often linger beyond the realm of their control.
The uphill struggle with email security was also captured in a CyberRisk Alliance (CRA) Business Intelligence study in May 2022 among 221 security and IT leaders and executives, security administrators and compliance professionals based in the United States.
In the last two years, cyberattacks traced back to exploited email vulnerabilities and enabled by users falling for phishing attempts led in some cases to uncomfortable consequences.
In October, the state of New York slapped EyeMed Vision Care with a fine — not for the first time — over its massive 2020 email hack and healthcare data breach. The vision benefits company was ordered to pay a $4.5 million penalty for multiple security violations that “contributed to” the data exposure. And fallout from that breach for both the company and customers continues.
Indeed, fears of similar fallout from an email security were reflected in results of a May 2022 CyberRisk Alliance (CRA) Business Intelligence study, based on a survey of 221 security and IT leaders and executives, security administrators and compliance professionals based in the United States.
Respondents reported dealing with some form of email attack daily, with attacks on Microsoft and Google email systems rising substantially. That included increased abuse of both Microsoft 365 and Google email infrastructure. In addition to phishing emails designed to capture login credentials, email attacks also contained payloads that include traditional viruses or application macros, such as those that run in Word or Excel.
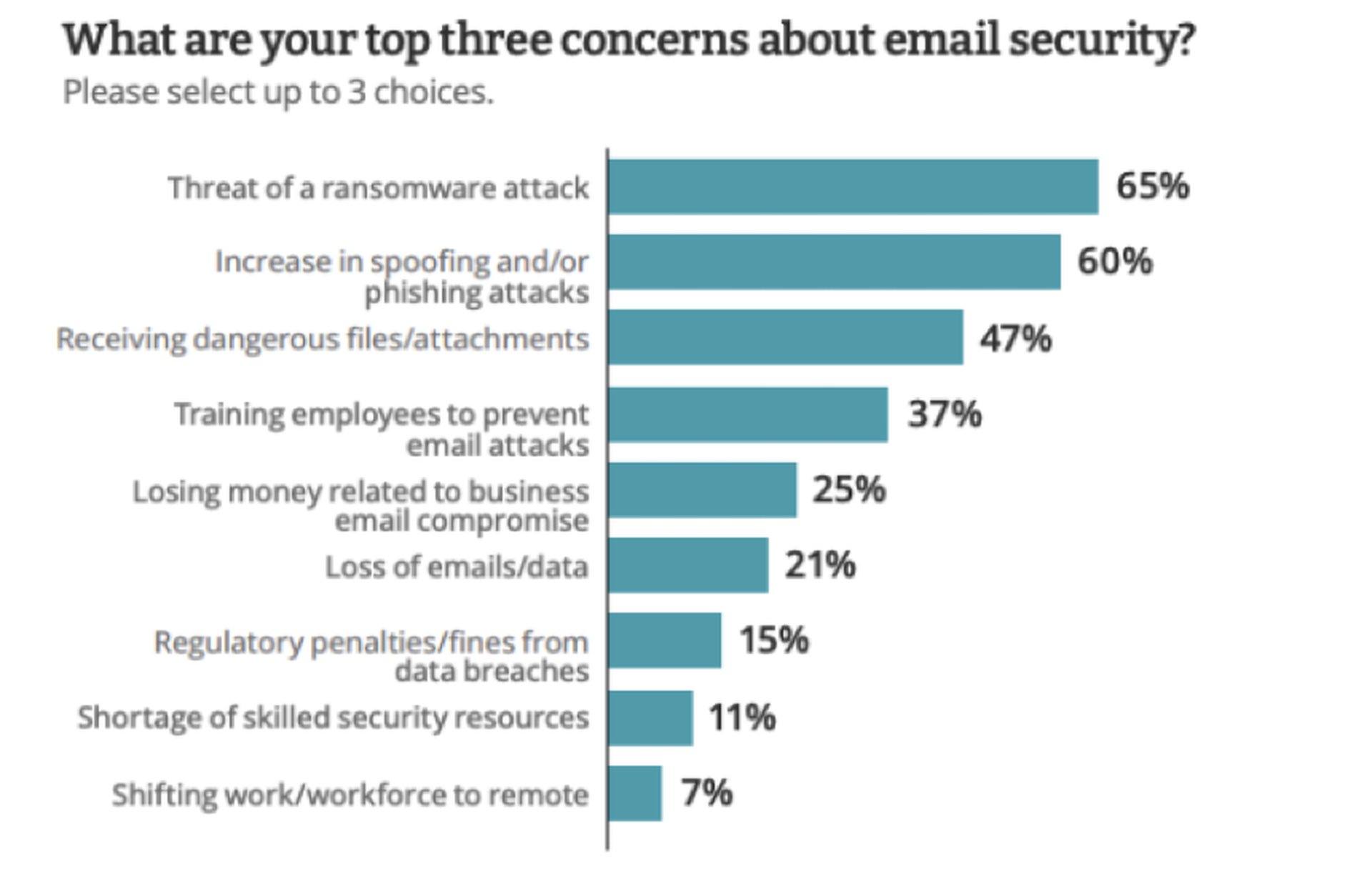
Respondents reported a significant and steady number of email attacks, with one-third experiencing up to 25 attacks on a daily basis. Additionally, about half (51%) of all respondents reported up to 25 business email compromise (BEC) attacks per day while one in five (21%) said they didn’t know and couldn’t estimate the volume of daily BEC attacks. At least half the respondents (51%) said they were very or extremely concerned about email attacks in the next 12 months. The threat of a ransomware attack was a top email security concern for two-thirds of all respondents, followed by an increase in spoofing and phishing.
“While we do run training sessions and communicate about fraudulent emails, people still click on things they shouldn’t, open up emails or attachments when they shouldn’t,” said one survey respondent. “If they don’t get a big red warning from the security systems, they just don’t think about every email they touch.”
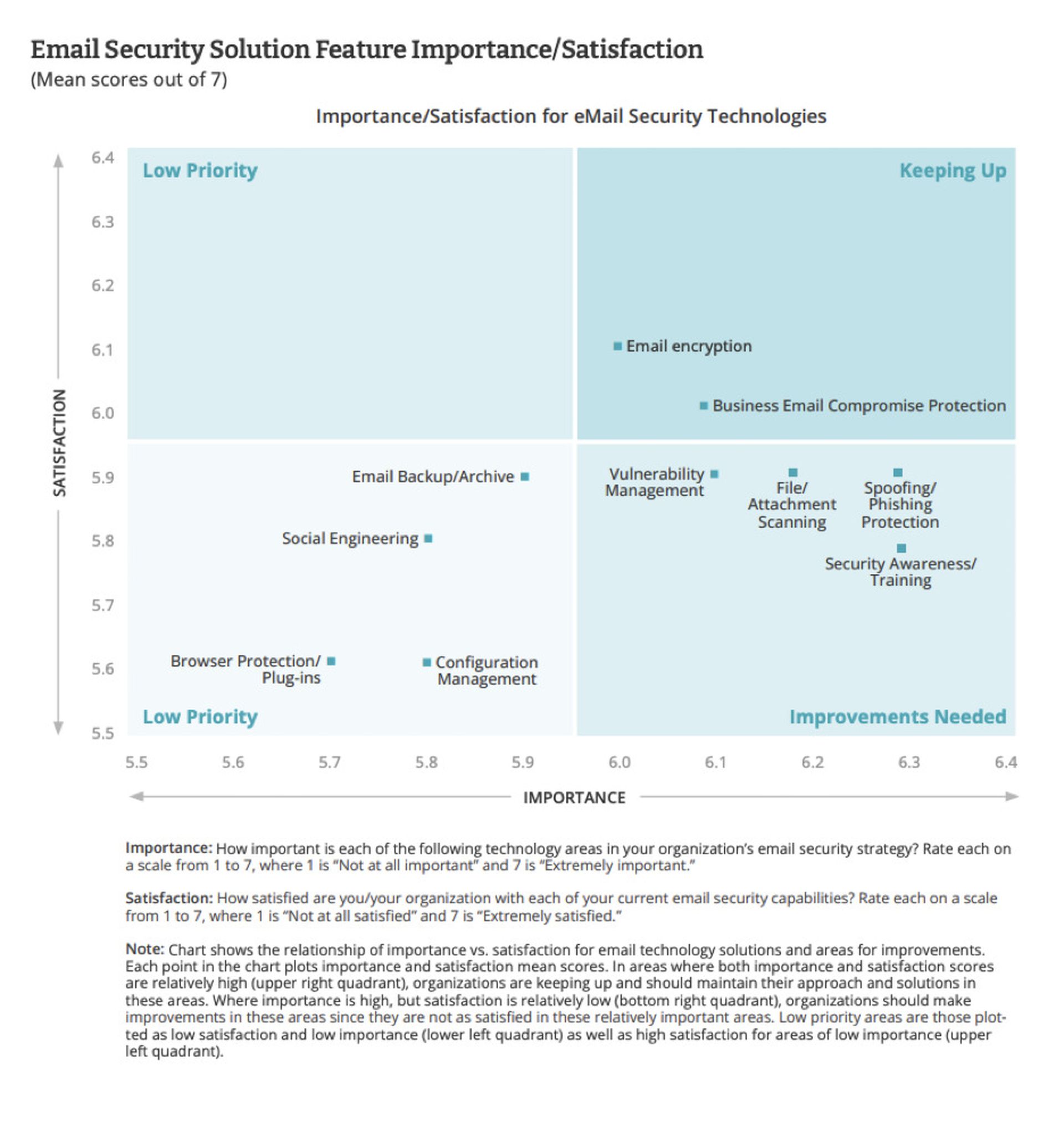
Respondents said they were keeping up with email encryption and business email compromise protection, but were falling behind on vulnerability management, file attachment scanning, phishing protection and security awareness training.
Fighting back with security tech and cyber training
While the email security challenges security practitioners faced were significant, there were some positive developments in 2022, according to the CyberRisk Alliance survey.
Recognizing the serious risks posed by email attacks, a large share of respondents (68%) reported their organization will likely increase spending on email security in the next 12 months. Education regarding social engineering, configuration management and more BEC protection will grab the majority of those additional dollars.
Of course, training is at the heart of plans to address social engineering. Security experts have said the most reliable way to stop email spoofing from succeeding may be by training your workforce to spot bogus emails. No amount of technology can completely stop phishing emails — and no amount of training can either — but a well-educated and well-practiced employee can spot them at least the majority of the time. Combine this stance with DMARC, DKIM and SPF and the odds of a compromise go down astronomically.
Likewise, proper workforce training will educate staffers who manage the company's money about the different tricks used by BEC scammers. (You could also require that more than one employee sign off on large money transfers.) Ideally, employees should participate in dynamic scenarios that simulate common BEC scams.
As one respondent put it, “We need to take a proactive approach to email security solutions as it saves money and time overall. If you are purely reactive, you are wasting valuable time and resources by reacting to an issue.”



