Identiverse, part of the SC Media and CyberRisk Alliance family of brands, takes place May 28-31 in Las Vegas. Ahead of the event, we’re sharing the most recent content around identity security, based on responses from our March 2024 Cybersecurity Buyer Intelligence Report capturing the challenges and successes security practitioners have experienced in the past year. For more coverage, visit the 2024 Identiverse website.
The last year saw unauthorized access bring some of the biggest names in industry to their knees. From attacks on Okta and Xfinity, to Microsoft and PJ&A, criminal gangs showed no mercy when it came to weaponizing identity and exploiting weak or non-existent IAM policies against all stripes of organizations.
The devastation has many security professionals worried that current defenses may not be enough. According to a new survey by CyberRisk Alliance (CRA), 3 out of 4 respondents in the cybersecurity industry report being more concerned now about unauthorized access attempts than they were just 12 months ago.

Fifty-eight percent of respondents also say that recent data breaches motivated their organizations to invest more in IAM solutions that could thwart such attacks.
While IAM adoption has risen year over year, at least a third of the survey audience (35%) still haven’t made the leap. And even those who do practice IAM (and reap its added protections) say roadblocks are par for the course.
Here’s what they said are the most common challenges.
Cost
“We lack the budget for truly effective solutions.”“The cost — I understand the importance of it, but the price tag is typically very high.”“Our difficulty is in finding resources to pay for external consultants who can assist us.” Balancing security with user efficiency
“Finding the line between security and productivity is a challenge for us — like keeping employees working efficiently with minimal risk.”“The balance between security and convenience. The focus of education are educators, and any inconvenience to them that is not explained in painstaking detail is at risk of being rolled back when complaints are received.” Integration
“One of the greatest challenges is ensuring IAM is integrated with all relevant systems and applications. This can be a complex and time-consuming process, especially for large organizations with many different systems and applications.”“Customizing IAM may be complex and cumbersome to implement and maintain, and may be disruptive to normal business operations.”“Integrating it with other infrastructure and integrating legacy applications – we haven’t figured that one out.”“Our greatest challenge with IAM is integration with all the moving parts of the company, not everything is up to date in terms of support and some internal systems need re-writing to support it.” Convincing the skeptics
“Getting everyone on the same page for implementation.”“Lack of buy-in for demonstrated need. The C-Suite’s willingness to implement.”“Mostly helping those who need to understand the importance of implementing these new security initiatives.”“Without support from all levels of the organization, an IAM implementation is likely to face delays and roadblocks.”“We are supporting about 49 school districts, and getting the state’s buy-in and helping them understand the importance and significance of it is the biggest challenge. Getting their administration to understand the need and reasoning behind it is a very big challenge.”“Business users' acceptance of IAM is the greatest challenge to implementing IAM.” 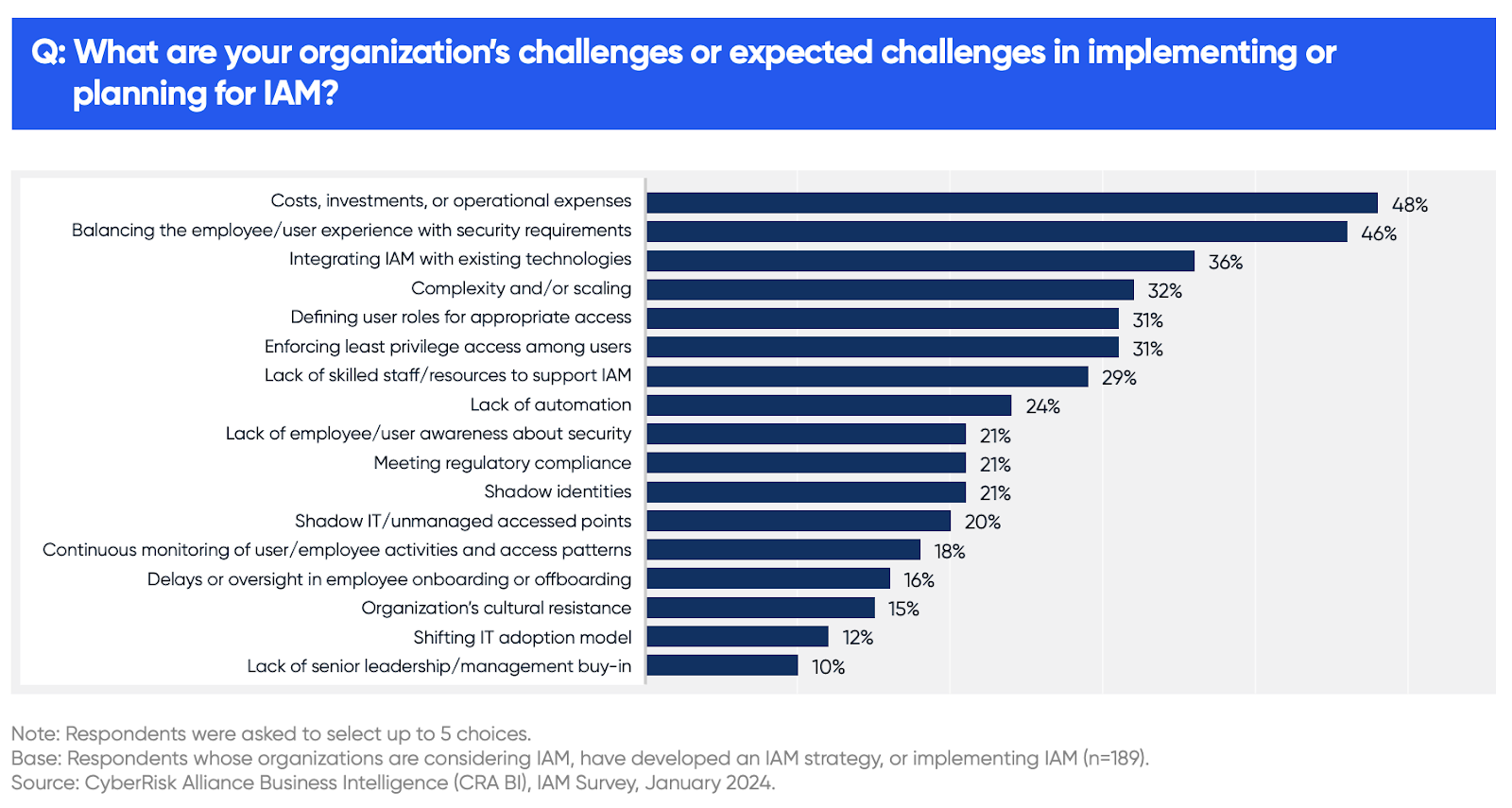
Lack of qualified experts
“Finding the staff with the right IAM skill set.”“Lack of internal staff and experience with IAM product implementation.”“Most IAM functionalities need an expert to set it up and require further assistance for major attributes. As a result, the length of user adoption and the complexity of a product is inversely proportional to the interest of the end-users. Who wants to spend hours in understanding a product or always require additional expertise to handle when its objective is to provide efficiency?” Configuring IAM properly
“Implementing PAM and PIM are challenges right now we are trying to work around, but it’s confusing and no specific information is shared.”“A challenge for us is getting all partners to employ SSO/SAML so we can federate authentication against our AD.”“There’s a lack of dedicated support to help key administrators to configure it. Features are there, but require lots of time and planning. It would be helpful to have build kits for common and best practice configurations. Fighting shadow IT and ingrained user habits
“We have a large user base supported by a relatively small IT staff. The greatest challenge we face when implementing IAM is our employees' use of shadow IT. It seems that many of our users are performing work on their personal computers and smartphones, outside of our company policy.”“Working with these users to remediate their actions has been the largest use of our time.” For more insights on these challenges and other issues in IAM adoption, click here to download the full survey report.
Get essential knowledge and practical strategies to fortify your identity security.